Tashi Delek everyone,
I hope you all are doing well 🙂 I know the way how I present my blog doesn’t attract much people, and those who read my blogs were either my old friends or new friends who I have met you somewhere and I had shamelessly bragged about my blog.
The quality of the blog is still kind of crude, for which I am working on. I hope you will see the progress.
You are most welcome to leave some comment and suggestions; and share your blog in the comment as well (please leave any suspicious link, I might block u for good).
I am not sure you have heard about this book called Practical Malware Analysis. It is quite popular and, to be honest it has been occupying my to do list for quite sometime. I think it is perfect time for me to read the book and share something which I learn each day apart from my daily chores. Of course, I see there were a couple of Lab exercise which I am going to do it and I will share the write-ups for the same.
Since the first chapter was emphasizing on static analysis and check of the metadata, I thought to share with you an incidence. It was around 5:30PM (our office timing gets over by 5:00PM), I received an email from one of the department. They asked me to analyzed 10 PDFs and check whether it was suspicious or not. I thought I need to automate the tasks with help of some bash scripts.
Yes, when I received the sample, first thing I did was make a copy of the files.
Since, I can’t share the original files here, let’s build the scenarios with help of some random files
Building Scenarios
cd /tmp
mkdir original_samples
cd original_samples
touch sample{1..10}.pdf #create 10 pdf files in one line
cd ..
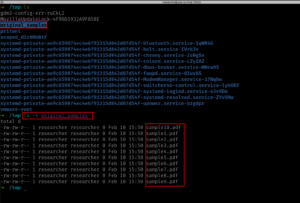
Actual Analysis
cp -r original_samples samples cd samples ls -l samples
Step 01:
Take the SHA256 of the file
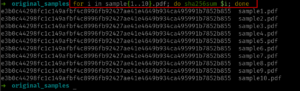
for i in sample{1..10}.pdf; do sha256sum $i; done
Yes, since I use bash to do most of my works therefore, therefore so far it was ok.
Let’s slice the column and store only the first field which contains the hashes. Because I would like to write a script and do the virustotal check automatically.
for i in sample{1..10}.pdf do sha256sum $i; done > hashes.txt
I am not going to share here how to create a virustotal account here, if you have a facebook or instagram account, you can do it 😉
Yes, I got my Private API.
I know such tasks could be easily completed if I use the ChatGPT or any AI tools, however, the reason I am doing these things is that I want to learn something. Of course, I could use the AI later when I really need the help. I am not against with AI but I am against using it before you understand the things you do.
After doing some google-fu, I found a stackoverflow link on which some of the people they have discussed about scanning the sample with VirusTotal using the apikey
I took down the script
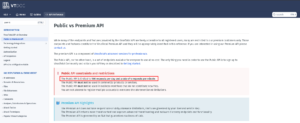
#!/usr/bin/bash while read -r line; do echo "$line" curl -s -X GET --url "https://www.virustotal.com/vtapi/v2/file/report?apikey=f41277fd391d1a80fc4cfbf0afae5184dXXXXXXXXXXXXXXXXXXXXXXXXXXXX&resource=$line" done <"hashes.txt" I am not able to get pass the entire hashes, because I can only pass 4 hashes in 1 minutes and it can process 500 requests per day; rate limit.
source: https://docs.virustotal.com/reference/public-vs-premium-api
At that time, I was thinking how about I set a counter and after 4 requests, I should make the script sleep for 1 minutes and then proceed. If possible, when it reach 450 requests (count), should give me a prompt/ warning.
Yes, that’s all for today! See you all tomorrow 🙂
“`
#!/usr/bin/env bash
VT_API_KEY=”your_api_key_here”
# Check if the API key is set
if [[ -z “$VT_API_KEY” ]]; then
echo “Error: VirusTotal API key is missing. Please set it in the script or as an environment variable.”
exit 1
fi
# File containing hashes
INPUT_FILE=”hashes.txt”
# Check if file exists
if [[ ! -f “$INPUT_FILE” ]]; then
echo “Error: File ‘$INPUT_FILE’ not found!”
exit 1
fi
# VirusTotal API URL
API_URL=”https://www.virustotal.com/api/v3/files/”
# Read each hash from the file and check with VirusTotal
while read -r hash; do
echo “Checking hash: $hash”
# Send API request
response=$(curl -s -X GET “${API_URL}${hash}” \
-H “x-apikey: ${VT_API_KEY}”)
# Print the response
echo “Response: $response”
# Avoid sending too many requests at once (wait for 15 seconds)
sleep 15
done < "$INPUT_FILE" ```

Leave a Reply