OtterCTF 2018 Memory Forensic Walkthrough
Hola!
I know they are not many reader to this blog apart from some occasional spammer therefore, the entire writeup was done in a way that it’s more of record keeping than for a potential reader.
By the way, I would like to take this opportunity to say thanks to all the friends I met at IFF (this is my second time) and Coconet, and to all my mentors in India and abroad, who has guided me and encouraged me to follow my dream!
Please bear with my lousy English and you might not believe that I was once selected as one of the top six Tibetan students to study in U.S. on full funded scholarship to pursue double Master. Nevertheless, due to my shabby English skill, the opportunity was fallen off from the plate. Therefore, I already kind of feeling empathy towards my genuine readers 🙁
OK. I will cut my crap here and do the write-ups 🙂
***
You can download the OtterCTF.vmem from here.
Question1:
->
We need to first find the profile of the image.
volatility -f ../OtterCTF.vmem imageinfo (Of course you don’t have to put ../ I put it there as my .vmem file is located at outside)

By the way, every time I use the first recommendation as profile of the image. In this case it is Win7SP1x64
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 mimikatz

Flag: CTF{MortyIsReallyAnOtter}
Question2:
->
From above we already got the PC name, therefore, the
Flag: CTF{WIN-LO6FAF3DTFE}
Since we need to know the PC IP address, we can use netscan.
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 netscan | more
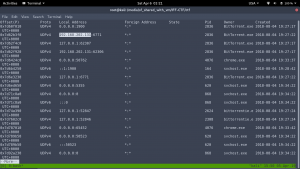
Flag: CTF{192.168.202.131}
Question 3:
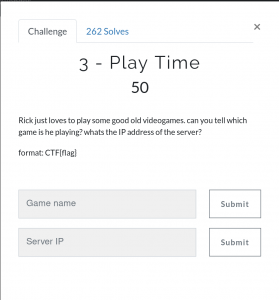
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 pslist | more
I literally googled every suspicious process and came to know the LunarMS still alive lol Here is the link, if you are interested in the game (http://lunarms.zapto.org/?base=main)
Flag: CTF{LunarMS}
Question 4:

->
strings ../OtterCTF.vmem | grep ‘Lunar-3’ -A5 -B5
(-A5 and -B5 will help us to get the after and before the string Lunar. )

Flag: {0tt3r8r33z3}
Note: I must admit that most of the time, whether it is work or CTF challenges, I had to depend mostly on my intuition based on my failed attempts or experiences!
Question 5:

If you read my write-up it may give you a feeling that I am lucky that I get all the solutions but I can assure you that I really struggle alot before doing the write-up. I almost spend four days to solve the problem.
Ok the question is 0x64 0x??{6-8} 0x40 0x06 0x??{18} 0x5a 0x0c 0x00{2}
For my convenience, it is like the following pattern in my mind
unknown known unknown known known
or
x{6-8} 40 6? 5a 0c 00
I really can’t come up a better idea than load the OtterCTF.vmem in some hex editor and find the pattern 5a 0c 00 and again I have to rely on my hunch (perhaps something like str33th@ck3r).
I will use bless (hex editor) tool.
sudo apt-get install bless -y (to install bless tool)
****
Question 6:
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 clipboard

Flag: CTF{M@il_Pr0vid0rs}
Question 7:
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 pstree | more
Apparently the process vmware-tray.exe personally sounds a legit process. Nevertheless, I really don’t get it is the sub-process of another non system process Rick And Morty. Therefore, to be honest, I have no 100% evidence to say it with straight face that both or either one of the process is a bad process. Anyway, let’s dump it and see whether the hunch is right 🙂
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 procdump -D . -p 3720
mv executable.3720.exe vmware-tray.exe (The reason I change the process name for my convenience)
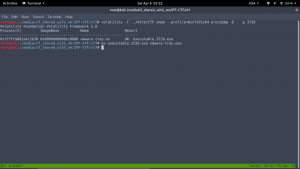
Virus Total Result:
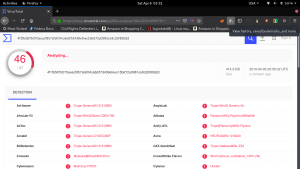
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 procdump -D . -p 3820
mv executable.3820.exe Rick_And_Morty.exe

Virus Total Result:

In conclusion, both files are infected but if I have to pick one, obviously I will pick vmware-tray.exe. Therefore,
Flag: CTF{vmware-tray.exe}
Question 8:
pslist of Volatility made me confirm that Rick is using Chrome. Therefore, I dumpfiles all the Chrome processes.
->
volatility -f ../OtterCTF.vmem –profile=Win7SP1x64 dumpfiles -Q 0x000000007d468850 -D .
-Q (offset or memory location)
-D (directory location)
. (at current directory)
I recursively download the entire Chrome processes.
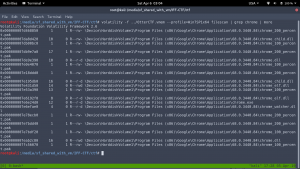
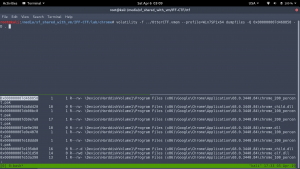
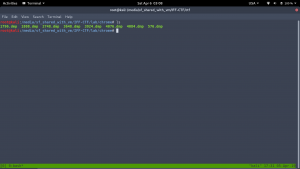
->
strings *.dmp | grep -i ‘Rick and Morty’ -A5 -B5 | sort -u | more
I see many duplicate data therefore, to make it more easy to get the key, I just sort it and unique it.

This screenshot proves the narration that victim has indeed used the Chrome to download the torrent file!
Anyway, that’s not the answer we are looking for.
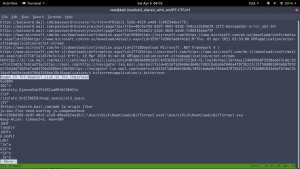
After lot of time, I got this string. However, it is not working. (I mean the flag is not accepting).