Hello and Tashi Delek everyone,
Although there isn’t many COVID19 cases around the place I stay, the ominous air of uncertainty and concern from the people getting increases. By the way, I reached Dharamsala yesterday and, as soon as I got in room, I did wash all the clothes I wear during the journey (I took a flight and a bus to reach here), and apart from few electronic gadgets, literally I washed everything and had loaded my kitchen with rations (this is my ritualistic habit whenever I get back to room, not because of the current situation though) and other amenities.
After a sumptuous meal, I retired early yesterday.
Anyway, I woke up around 5 o’clock today and feeling fresh and rejuvenated. Nevertheless, I had to wait till April to renew my internet connection.
I thought why not I play this “born2root” to kill some time, because I find it abnormally quiet here (because at Bangalore, I stay at my friend’s place and usually commotion of college students push life in the atmosphere there). Am I missing the place?!
Let’s see whether we can break this machine or not 🙂
Step 01: ifconfig Kali Machine IP: 192.168.56.11 Step 02: nmap 192.168.56.11/24 > target_ip.log Target Machine IP: 192.168.56.14 Step 03: Information Gathering nmap -sC -sV -p- 192.168.56.14 -oN nmap.log
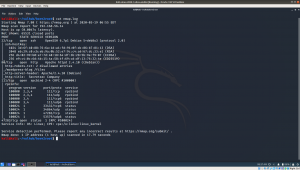
From the output, I can deduce that it runs SSH, Apache webserver and rpcbind. Let’s check the low hanging first. The web part.
It has a website on it, it reveals lot of information. I am not sure why, but I feel like taking the website content (including keywords and usernames) to make a list, perhaps I could use it as dictionary later on.
http://192.168.56.14
Then I visit robots.txt and I didn’t get potential information. I did run exiftool on the image though..
I ran nikto to enumerate and usually if I don’t find any, I use gobuster.
nikto -h 192.168.56.14 > nikto.log
Indeed, it shown couple of interesting information however, much of those yield no important information apart from one file.
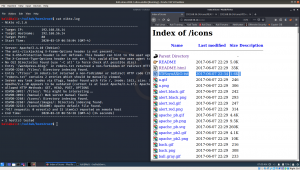
I visited the first two text files, I got this key.
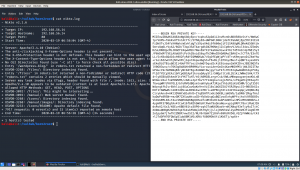
I didn’t check further because I got this key. However, if it is real application, I would definitely download the entire pictures and analyze each one though.
Remember, we got couple of good username from the above steps. So, first is martin, I tried to login with this username.
ssh -i id_rsa martin@192.168.56.14
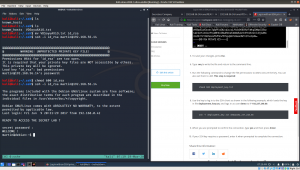
Oh my god, I used a good amount of time, simple to know the password for it. It really got me.. IT”S A TROLL AND YOU JUST NEED TO PRESS ENTER!
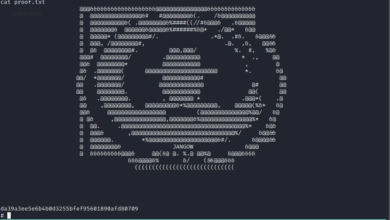
And then, I reached to a state that I couldn’t find anything.. Here is the proof that what I was doing..
At this moment, I really learned a new tip, that is if you want to check whether any cron job is set or not, don’t just depend on crontab -l
But check,
cat /etc/crontab to know the full entry of cron. I learned this from other blog
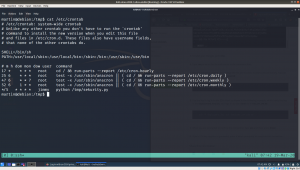
yes, from above write we can see that there is a cronjob entry for user jimmy which runs at every 5 minutes. Therefore, I copied a python reverse shell command from pentest monkey.And waiting for the reverse connection. So finger cross 🙂
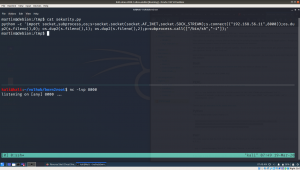
By the way, if you are not getting reverse connection, try to polish the script you copy from the pentest money and make it more like native python program (like how we used to write normally with shbank). By the way, don’t try to execute the python program, you can get the reverse shell connection with martin user again. So patiently wait for five minutes or go and fill up your tea cup 🙂
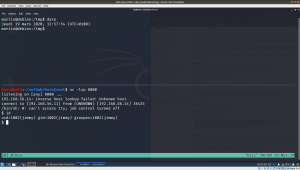
yes, I got the reverse connection of user jimmy.
Then, I try to switch user to jimmy and martin and it was not successful. I reached my wits end. Had a delicious mushroom noodle with broth made of vegetables. (Yeah, I am veggie lol). Then had brushed my teeth and literally if I can pwn this box, I am sure I will have a great sleep 😉
I googled and came to know of a beautiful tool called cewl. I try with hydra and it was not successful. Then, I read this writeup. The author tried a tool called cupp to generate dictionary and it was beautiful. Nevertheless, I was not able to crack with hydra. I read the writeup again and check it again and it seems the password of user hadi is hadi123. I was little baffled why the wordlist generator eliminate such obvious password. Anyway, I add it manually to my dictionary and it helped me confirm that it was not hydra’s fault. Cheers buddy lol

And I got login [You can click on the image to see the command]
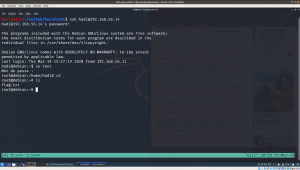
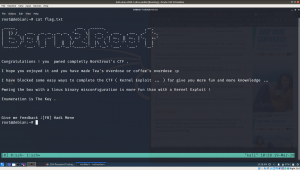
Finally, here is the flag 🙂