Penetration Testing
-
OSCP

This is NullByte from vulhub
Overview: Target Machine IP Address: 192.168.56.122 My Machine IP Address: 192.168.56.117 Mission: Boot to Root Get to /root/proof.txt and follow…
Read More » -
offsec
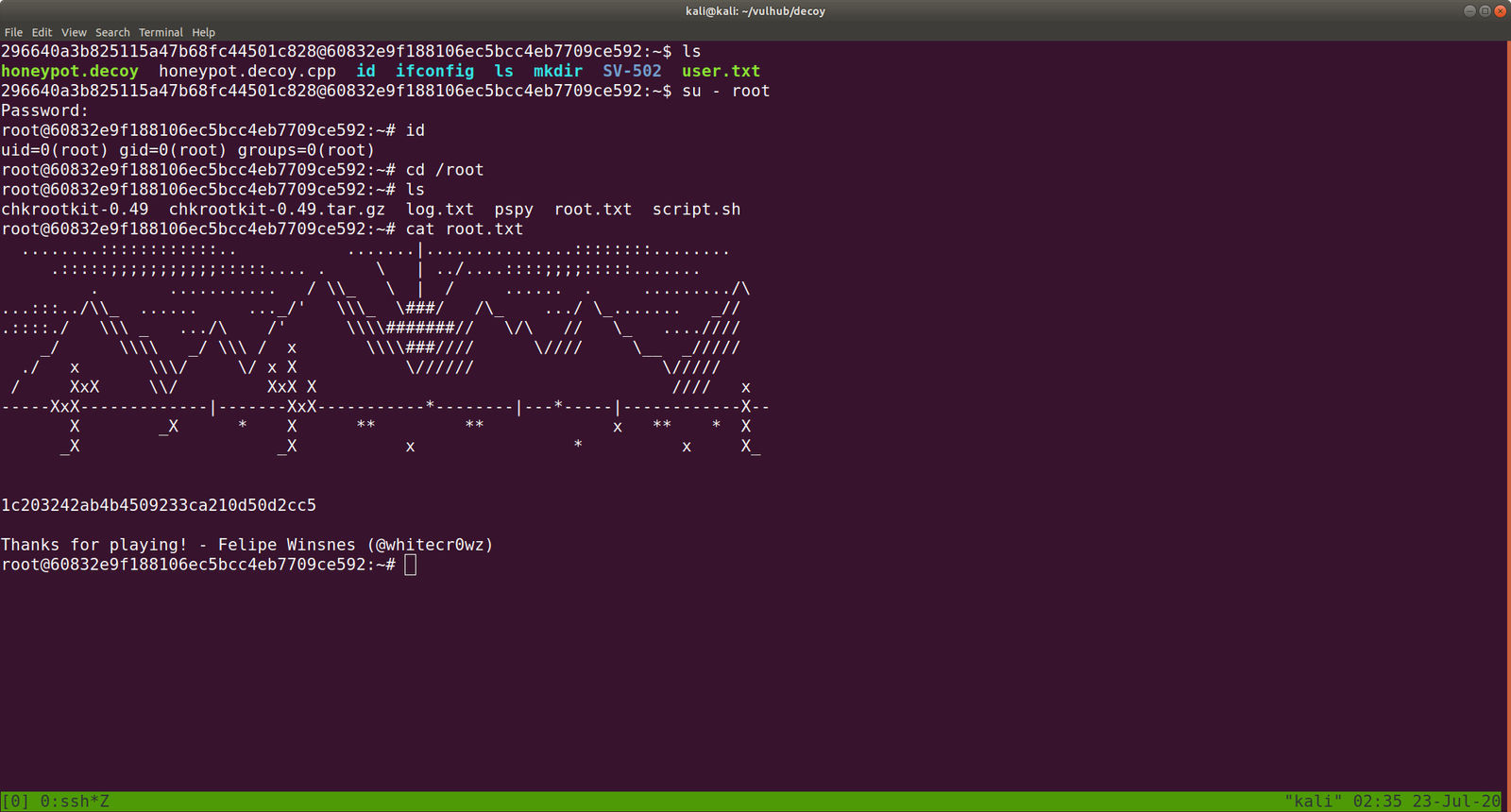
Shelling Decoy
Overview: Target Machine IP Address: 192.168.56.42 My Machine IP Address: 192.168.56.20 Mission: THIS IS A MACHINE FOR COMPLETE BEGINNER, THERE…
Read More » -
OSCP

Let’s pwn cybersploit machine
Overview: Target Machine IP Address: 192.168.56.40 My Machine IP Address: 192.168.56.20 Mission: THIS IS A MACHINE FOR COMPLETE BEGINNER, THERE…
Read More » -
Let’s take down victim01
Overview: Pwned Machine IP Address: 192.168.56.38 My Machine IP Address: 192.168.56.20 Mission: To gain access to root and read the…
Read More »
