Overview:
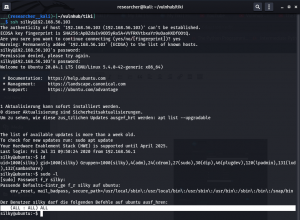
Target Machine IP Address: 192.168.56.103 My Machine IP Address: 192.168.56.1
Mission:
Boot to Root
1. To get root flag
2. To get root access
Description:
"Oh no our webserver got compromised. The attacker used an 0day, so we dont know how he got into the admin panel. Investigate that. This is an OSCP Prep Box, its based on a CVE I recently found. Its on the OSCP lab machines level."
Level: Easy/Medium
Easy/Medium
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target IP: 192.168.56.103
nmap -sC -sV -p- -Pn 192.168.56.103 -o nmap.log
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 a3:d8:4a:89:a9:25:6d:07:c5:3d:76:28:06:ed:d1:c0 (RSA) | 256 e7:b2:89:05:54:57:dc:02:f4:8c:3a:7c:55:8b:51:aa (ECDSA) |_ 256 fd:77:07:2b:4a:16:3a:01:6b:e0:00:0c:0a:36:d8:2f (ED25519) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) | http-methods: |_ Supported Methods: POST OPTIONS HEAD GET | http-robots.txt: 1 disallowed entry |_/tiki/ |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works 139/tcp open netbios-ssn Samba smbd 4.6.2 445/tcp open netbios-ssn Samba smbd 4.6.2 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: 5h29m58s | nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | Names: | UBUNTU<00> Flags: <unique><active> | UBUNTU<03> Flags: <unique><active> | UBUNTU<20> Flags: <unique><active> | \x01\x02__MSBROWSE__\x02<01> Flags: <group><active> | WORKGROUP<00> Flags: <group><active> | WORKGROUP<1d> Flags: <unique><active> |_ WORKGROUP<1e> Flags: <group><active>
1. HTTP (80/tcp)
http://192.168.56.103/tiki/tiki-index.php
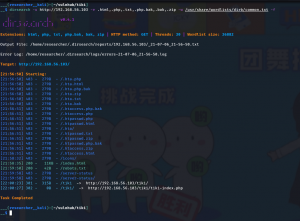
gobuster dir -u http://192.168.56.103 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .html,.php,.txt,.php.bak,.bak,.zip -o gobuster.log

dirsearch -u http://192.168.56.103 -e .html,.php,.txt,.php.bak,.bak,.zip -w /usr/share/wordlists/dirb/common.txt -f
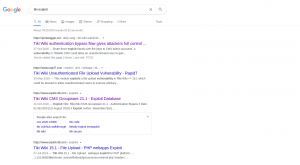
I got tiki right from the robots.txt however, couldn’t figure out how to find the version of the tiki cms. Therefore, I have to find other way based on the information I have (from the nmap result).
Since the target box is running smb, let’s enumerate it using enum4linux
enum4linux 192.168.56.103
smbclient //192.168.56.103/Notes
cat Mail.txt
Password of TikiCMS: 51lky571k1
I struggle alittle for the username as I was think a way to bruteforce it. All of sudden I remember that the box itself shows a username silky when we start the machine. When I tried that, it let me in 🙂
! Hi my Name is Silky, This is my third CTF. Dont give up, there is always a way to __root__! I like Cats, Frogs, Snakes and cute Doggos but thats not helpful isnt it? Hmmm maybe you like something different, ... You like Hacking right? I got a new CVE Number: But I constantly forget its ID :/
When I see this message (specially the bold one), I tried every way possible to know the version of the Tiki running on our target machine. Nevertheless, it took me more than two days lol (I mean the leisure time). Guess what? I even asked in a telegram group. But no luck.
Therefore, I tried my Jungle Knowledge…
The last modification date is 2020 July 30, so when I need to find an exploit which has CVE number around at year and time. (Pure guessing out of desparation)
I checked both the exploit and it is same. So I didn’t bother much but directly visited the exploit-db.
You can copy the exploit as per your preference 🙂
You can run the exploit using
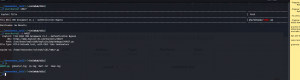
python3 48927.py 192.168.56.103
Based on the output, we need to fire the burpsuite.
i) Burp is ready and then I tried to login with username admin and a fake password badman.
ii) Then I erased the password value and forward the request and I was able to login with admin privilege.
You might see sam, actually sam is not there. I tried to upload a php-reverse-shell, thought to get a reverse connection but was not successful lol
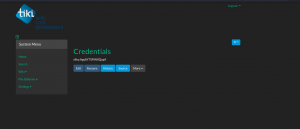
Then the credential page caught my eyes. and it has indeed hidden gems in it 🙂
We know SSH protocol is running and got the following credentials.
username and password
silky:Agy8Y7SPJNXQzqA
flag:88d8120f434c3b4221937a8cd0668588
That’s all guys… It is my habbit to pray before I retire to bed and I think right now is the perfect time to do so 🙂 By the way, I pray for all the sentient beings which includes you, and I wish you happiness 🙂