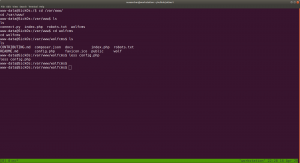
Firstly we need to know the machine (Target Machine) IP address. I know three ways to get it, but in this write up, I will go with the one which I picked up recently.
By the way, my Host IP address is 192.168.56.1
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target Machine IP : 192.168.56.3
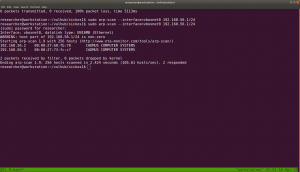
Now, we need to know what services, ports etc. are running on the machine.
nmap -sC -sV -p- -Pn 192.168.56.3/24 -oN nmap.log
We can clearly see that it is running
1. SSH 22
2. http-proxy Squid http proxy on port 3128
I had to struggle a little on Squid Proxy because I thought too much like its functionalities and lot of other stuffs..
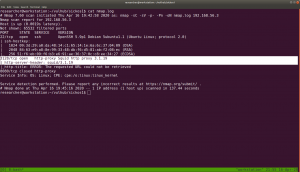
I was little disappoint with gobuster, however nikto really helped me in this.
nikto -h http://192.168.56.3 -useproxy http://192.168.56.3:3128
I am happy that it ran, but it didn’t me any important things.
Without Proxy
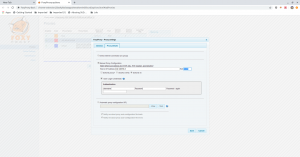
Hats-off to foxy-proxy. It made my life easy.
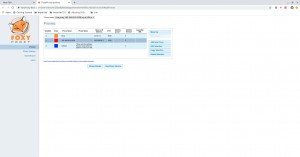
After setup, we got the access to the website.
There isn’t anything in the source code.
Browse http://192.168.56.3/wolfcms/?about-us.html
I visited almost all the page and links and came saw there is ? in all the URL http://192.168.56.3/wolfcms/? Besides, every CMS has a admin panel login like wp-login.php or wpadmin for wordpress and admin for joomla. Likewise, I tried login and admin. And finally, admin parameter helped me to redirect to the login page.
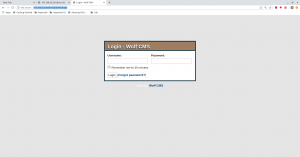
Visit http://192.168.56.3/wolfcms/?/admin/login
I tried admin:password and admin:admin for username and password respectively and admin:admin did logged in.
Then, I didn’t bother much as soon as I saw the Home page with PHP code, written in it. I paste a php revershell, and it did work for me.
On my host machine, I am waiting a reverse connection from the above CMS.
nc -lvp 9000
As soon as I visit the Homepage, I got a reverse connection.
python -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
From above, we can conclude that there is a username called sickos.
And since we know that there is CMS is running, it can be certain that there is file which contains Database Credentials like wp-config.php in WordPress.
username: root and sickos (Which we got from above enumeration)
password: john@123
I tried ssh connection with above credentials. Only username with sickos@192.168.56.3 worked with the password john@123
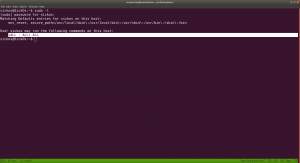
Every time, as soon as I got ssh, I like to check the privilege of the user with
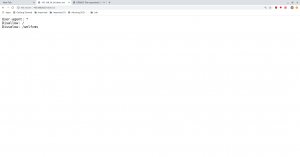
sudo -l
The current user has the sudo permission allowed.
we got the flag, finally 🙂
It’s almost 11PM here, I think now I can have a good night sleep 🙂





Leave a Reply