Exploiting Easy RM to MP3 Converter on Windows 7 (Replica)
Around five years back, I had the privilege to learn buffer overflow from one of my dear mentor. Nevertheless, due to changes in the nature of my work, I didn’t get proper time to explore more.
Many of my colleague had shared me their challenges to understanding the concept, despite they were comfortable in programming; I had the other way round experience. I enjoyed the subject back then and perhaps I could say that I was the sole individual who had wrote an exploit for a Vulnerable Application (which we had downloaded from exploit-db.com; it was war-FTP).
However, I must confess here that I forgot almost everything apart from esp, eip, ebp..
Required Software:
Download the vulnerable app from here.
Download the Window 7 32 bit from here. (By the way, don’t forget to take a snapshot, as after 30 days you might not access the Virtual Machine. I choose IE11 and VirtualBox).
Download Immunity Debugger from here. (If you are concerned with providing real email id, you can put some fake ID).
Download Mona from here. (I must confess, I have never used mona before)
I will not mention from where you will get, Kali Linux, Virtualbox and Virtualbox extension etc..
**************
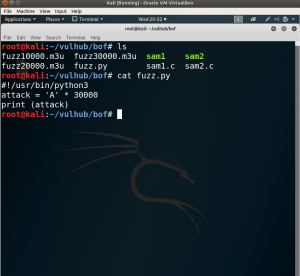
#!/usr/bin/python3 attack = 'A' * 30000 print (attack)
I tried with 10000 (As), followed by 20000. At 30000, the application finally crashed lol.
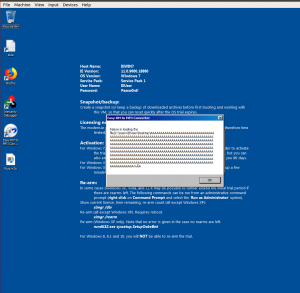
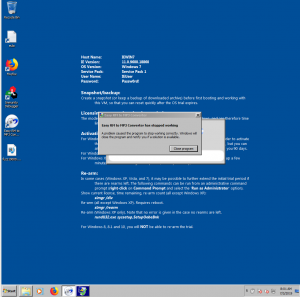
Let’s Assess the Application using Immunity Debugger: